Citrix Secure Access: Unbreakable Business VPN with Zero Downtime
Stranded at a rural inn with critical project deadlines, my pulse raced when corporate systems rejected connection attempts. That panic dissolved the moment I deployed Citrix Secure Access. Suddenly my tablet became a fortified extension of headquarters, granting instant access to financial dashboards and development environments through encrypted tunnels that felt like physical office networks. This isn't just another VPN - it's an enterprise lifeline reshaping how distributed teams operate.
The Always-On connection became my silent guardian during transatlantic flights. When turbulence disrupted cabin Wi-Fi over Greenland, my fingers tightened around the armrest anticipating crashed sessions. But client certificates maintained the link invisibly, preserving my virtual desktop exactly as I left it. That first seamless reconnection sparked audible relief, transforming airport lounges into productive hubs.
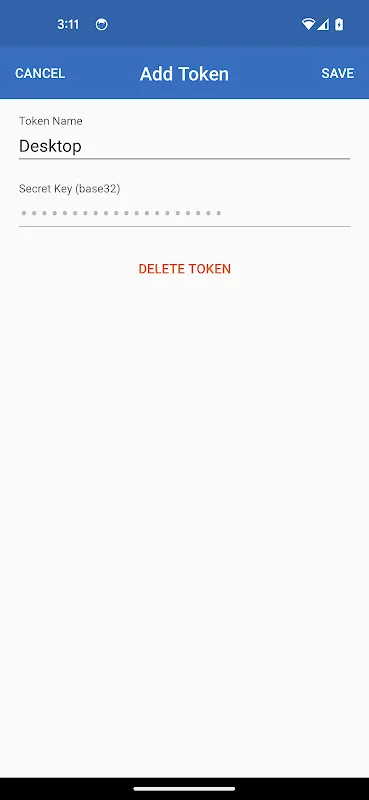
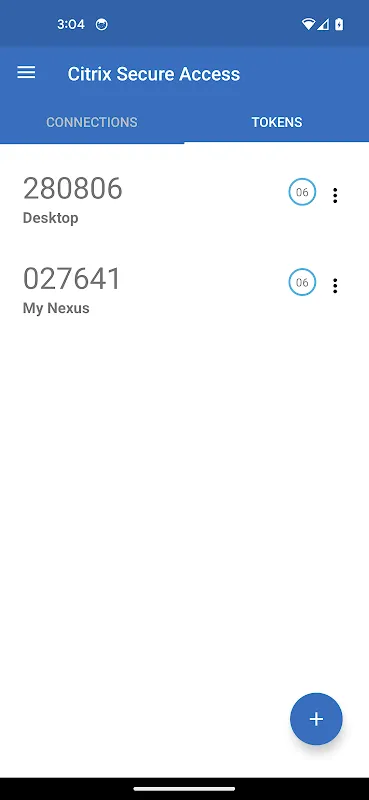
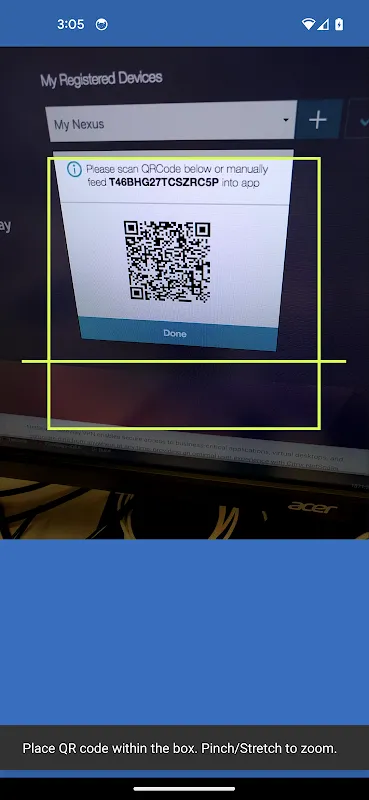
During quarterly audits, per-app VPN routing proved unexpectedly vital. While analyzing sensitive payroll data, I restricted access solely to our accounting software. The tactile satisfaction of toggling application-specific tunnels created psychological boundaries - knowing my social media apps operated outside the secure bubble eased compliance anxieties. MDM integration meant new hires gained precisely configured access within minutes, not days.
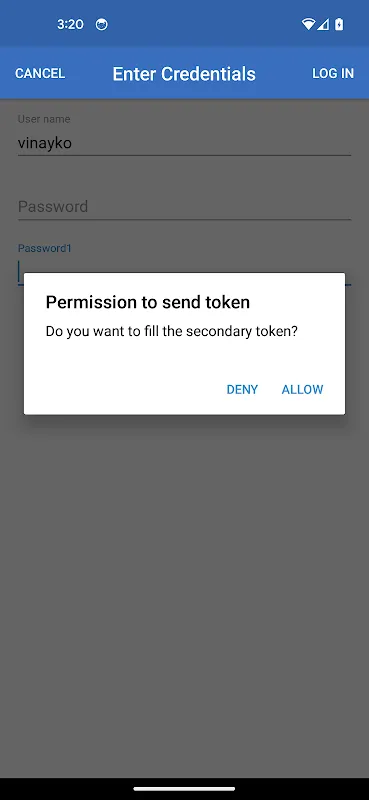
Multi-factor authentication evolved from chore to triumph through biometric integration. After midnight coding sessions, bleary-eyed login attempts would previously trigger security lockouts. Now, fingerprint recognition blended security with exhaustion-friendly access. The push notification approval system particularly shined during board presentations - discreetly authorizing access mid-sentence without disrupting flow.
Network resilience stunned me during a coastal retreat. Walking from cottage veranda to beachside café triggered four network handoffs. Yet my video conference persisted uninterrupted, the seamless session transition mimicking cellular handover perfection. Only later did I appreciate the engineering marvel maintaining TLS tunnels across volatile connections.
When debugging an authentication glitch, the built-in log emailer transformed frustration into gratitude. Rather than describing symptoms to IT, attaching diagnostic files directly from the app interface created collaborative troubleshooting. That feature alone saved three support tickets last quarter.
At dawn in Barcelona, I activated the VPN while reviewing contracts. Mediterranean light flooded the hotel room as localized interfaces automatically switched to Spanish, eliminating clumsy translation efforts during regional negotiations. This linguistic intelligence feels particularly considerate when working across European branches.
The tradeoffs? Initial configuration requires IT assistance - a necessary complexity for this security grade. And while biometrics work flawlessly on modern devices, older tablets occasionally require manual fallbacks. Still, watching the persistent notification icon during high-stakes operations delivers profound reassurance. For consultants juggling sensitive data across unstable networks, this isn't just convenient - it's career armor.
Keywords: enterprise VPN, remote access, multi-factor authentication, business continuity, secure tunneling