Protege Config: Transform Your Security Reader Setup Without Extra Hardware
Struggling with tangled cables and bulky laptops at client sites, I nearly dropped my third coffee that month when discovering Protege Config. This unassuming app erased hours of logistical headaches by letting my phone directly configure ICT TSEC readers. As a security system integrator juggling fifteen commercial properties, its profile-based setups became my silent partner in reclaiming sanity. For technicians drowning in hardware cases, this isn't just convenient—it's liberation.
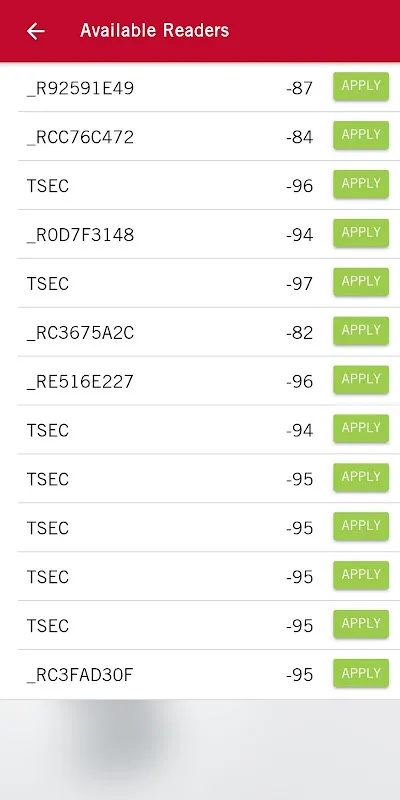
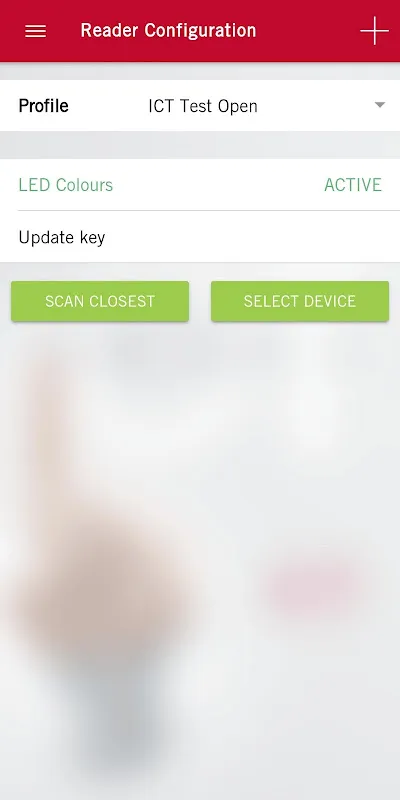
Profile-Based Configuration reshaped my workflow during a multi-building hospital retrofit. While standing at Cardiology's restricted entry, I saved door-specific settings as "Wing A Clearance" before walking to Oncology. The relief was physical—shoulders unclenching as configurations organized themselves like digital file cabinets. Previously, handwritten notes would smear in the rain; now tapping "Apply to Oncology" replicates settings before I finish my espresso.
Mobile Credential Authentication surprised me with its elegance during a midnight emergency call. With my assigned credential active, authenticating took less time than unlocking the server room. The subtle vibration confirming access felt like a handshake with the system itself—no fumbling for keycards with gloved hands. What I didn't expect? Using this feature to train junior techs by temporarily granting them configuration rights during installations.
Firmware Intelligence saved a downtown skyscraper project from delays. Scanning a reader revealed outdated firmware before configuration attempts. Though initially frustrated, the auto-generated report for the client justified immediate updates. Post-update, the crisp click of relays engaging through the app delivered visceral satisfaction—like hearing a vault door thud shut securely.
Tuesday 3 AM at the data center: chilled air humming as I crouched beside rack-mounted readers. Sweat trickled down my neck until Protege Config's interface glowed—swiping through profiles felt like flipping a master switchboard. When "Server Room Profile" loaded pre-set timings, the relief was auditory: my own exhale echoing in the silence as green status lights bloomed across the corridor.
Friday rush hour traffic: dashboard vibrating with an urgent reconfiguration request. Pulling over, I remotely adjusted holiday schedules for a retail client before the light turned green. The tactile scroll through time slots—fingertip grazing midnight thresholds—made complex programming feel like setting a kitchen timer.
The triumph? Launching faster than my parking app when urgent alerts hit. But that firmware requirement haunts me—like discovering empty batteries during a thunderstorm. Still, watching configurations deploy seamlessly from a rain-smeared phone screen outweighs occasional version checks. For security nomads trading toolbelts for smartphones, this is your pocket-sized command center.
Keywords: Protege Config, ICT TSEC reader, mobile configuration, security system, firmware