evidence authentication 2025-11-13T04:12:42Z
-
 Evidence, Grand CahorsPrepare your travels with the best application Evidence, Grand Cahors.The application Evidence, Grand Cahors offers all the features to travel on your transit network: real-time and theoretical schedules, traffic info, route search, plans.Consult with one click the next passages in real time at the stops closest to you!Easily find the last stops that you have searched for and add your stop to favorites in one click.Why use Evidence, Grand Cahors?Be on time: check the waitin
Evidence, Grand CahorsPrepare your travels with the best application Evidence, Grand Cahors.The application Evidence, Grand Cahors offers all the features to travel on your transit network: real-time and theoretical schedules, traffic info, route search, plans.Consult with one click the next passages in real time at the stops closest to you!Easily find the last stops that you have searched for and add your stop to favorites in one click.Why use Evidence, Grand Cahors?Be on time: check the waitin -
 LEGIT APP AuthenticationLEGIT APP - Fast & Secure Luxury Authentication** Featured in ELLE, Harper's BAZAAR, Hypebeast, TikTok Shop and More**LEGIT APP is your fast & globally trusted authentication solution for luxury handbags, sneakers and designer products. Powered by a great team of expert authenticators and cutting-edge AI technology.\xe2\x80\xa2 Trusted by millions: We've completed over 3 million authentications worldwide, earning nearly 20,000 5-star reviews from satisfied customers in Ap
LEGIT APP AuthenticationLEGIT APP - Fast & Secure Luxury Authentication** Featured in ELLE, Harper's BAZAAR, Hypebeast, TikTok Shop and More**LEGIT APP is your fast & globally trusted authentication solution for luxury handbags, sneakers and designer products. Powered by a great team of expert authenticators and cutting-edge AI technology.\xe2\x80\xa2 Trusted by millions: We've completed over 3 million authentications worldwide, earning nearly 20,000 5-star reviews from satisfied customers in Ap -
 Spriv TwoFactor AuthenticationWhat makes Spriv so cool? Only one single click on \xe2\x80\x9cAllow\xe2\x80\x9d and all future logins from the same computer and the same location will automatically be allowed without any user intervention, as long as the phone is near the same computer and the same l
Spriv TwoFactor AuthenticationWhat makes Spriv so cool? Only one single click on \xe2\x80\x9cAllow\xe2\x80\x9d and all future logins from the same computer and the same location will automatically be allowed without any user intervention, as long as the phone is near the same computer and the same l -
 Indian Evidence Act 1872 (IEA)Refer to Bharatiya Sakshya Adhiniyam, 2023 in Law App for latest Criminal Reforms in India\xe2\x80\x98Indian Evidence Act 1872 (IEA)\xe2\x80\x99 is the Best Indian Evidence Act learning App with latest Amendments. It is a free and offline app providing detail Section-wi
Indian Evidence Act 1872 (IEA)Refer to Bharatiya Sakshya Adhiniyam, 2023 in Law App for latest Criminal Reforms in India\xe2\x80\x98Indian Evidence Act 1872 (IEA)\xe2\x80\x99 is the Best Indian Evidence Act learning App with latest Amendments. It is a free and offline app providing detail Section-wi -
 Police & Criminal Evidence Act\xe2\x80\x98Police & Criminal Evidence Act\xe2\x80\x99 is the Best Police and Criminal Evidence Act 1984 learning App with latest Amendments. It is a free and offline app providing detail Section-wise and Chapter-wise Legal Information of Police and Criminal Evidence Ac
Police & Criminal Evidence Act\xe2\x80\x98Police & Criminal Evidence Act\xe2\x80\x99 is the Best Police and Criminal Evidence Act 1984 learning App with latest Amendments. It is a free and offline app providing detail Section-wise and Chapter-wise Legal Information of Police and Criminal Evidence Ac -
 Microsoft AuthenticatorTwo factor authentication (2FA or TFA) is easy, convenient, and secure when you use Microsoft Authenticator. Use your phone, not your password, to log into your Microsoft account. Just enter your username, then approve the notification sent to your phone. Your fingerprint, face ID, or PIN will provide a second layer of security in this two step verification process. After you\xe2\x80\x99ve signed in with two factor authentication (2FA or TFA), you\xe2\x80\x99ll have access
Microsoft AuthenticatorTwo factor authentication (2FA or TFA) is easy, convenient, and secure when you use Microsoft Authenticator. Use your phone, not your password, to log into your Microsoft account. Just enter your username, then approve the notification sent to your phone. Your fingerprint, face ID, or PIN will provide a second layer of security in this two step verification process. After you\xe2\x80\x99ve signed in with two factor authentication (2FA or TFA), you\xe2\x80\x99ll have access -
 PassLogic Authenticator"PassLogic Authenticator (Former name: PassClip L)" is the mobile app for the MFA Solution "PassLogic".It generates one-time passwords and offers LoginProtect (Android 6+ for fingerprint authentication, Android 9+ for biometric authentication). It supports MFA with PassLogic and smartphone biometrics.To use "PassLogic Authenticator", installation of the "PassLogic" is required. For more information about "PassLogic", please visit the official PassLogic website: https://pas
PassLogic Authenticator"PassLogic Authenticator (Former name: PassClip L)" is the mobile app for the MFA Solution "PassLogic".It generates one-time passwords and offers LoginProtect (Android 6+ for fingerprint authentication, Android 9+ for biometric authentication). It supports MFA with PassLogic and smartphone biometrics.To use "PassLogic Authenticator", installation of the "PassLogic" is required. For more information about "PassLogic", please visit the official PassLogic website: https://pas -
 Authenticator AppAuthenticator App 2FA - Password Manager is a multifunctional security and account management application with many useful and reliable features.With the Scan QR 2FA feature, logging into your accounts becomes easier and safer.The Backup & Sync feature ensures that you never lose your data when changing devices or having to reinstall from scratch.The Password Manager and Autofill help you store and manage passwords securely and efficiently. It will automatically fill in your log
Authenticator AppAuthenticator App 2FA - Password Manager is a multifunctional security and account management application with many useful and reliable features.With the Scan QR 2FA feature, logging into your accounts becomes easier and safer.The Backup & Sync feature ensures that you never lose your data when changing devices or having to reinstall from scratch.The Password Manager and Autofill help you store and manage passwords securely and efficiently. It will automatically fill in your log -
 Yubico AuthenticatorStore your unique credential on a hardware-backed security key and take it wherever you go from mobile to desktop. No more storing sensitive secrets on your mobile phone, leaving your account vulnerable to takeovers. With the Yubico Authenticator you can raise the bar for securit
Yubico AuthenticatorStore your unique credential on a hardware-backed security key and take it wherever you go from mobile to desktop. No more storing sensitive secrets on your mobile phone, leaving your account vulnerable to takeovers. With the Yubico Authenticator you can raise the bar for securit -
 Evidenced Based Medicine GuideEvidence-Based Medicine Guidelines (EBMG) is an easy-to-use collection of clinical guidelines for primary and ambulatory care linked to the best available evidence. Continuously updated, EBMG follows the latest developments in clinical medicine and brings evidence into practice.EBMG is designed to provide you with the information you need quickly (seconds, not minutes) and using a single search term. Designed for use at the point of care, the guidelines are delivere
Evidenced Based Medicine GuideEvidence-Based Medicine Guidelines (EBMG) is an easy-to-use collection of clinical guidelines for primary and ambulatory care linked to the best available evidence. Continuously updated, EBMG follows the latest developments in clinical medicine and brings evidence into practice.EBMG is designed to provide you with the information you need quickly (seconds, not minutes) and using a single search term. Designed for use at the point of care, the guidelines are delivere -
 Granny's Silent ResidenceImmerse yourself in cinematic horror that will not let you go until the very end of the mysterious story. Enjoy dynamic first-person cutscenes and take part in an incredible storyline.Dare you to challenge your fears and travel to an old abandoned evil house in a village in the hills and unravel all the disturbing secrets?Do you remember that your granny told you scary tales about a silent, abandoned playhouse where the evil spirit lady Hasshaku-sama (or slendrina for ex
Granny's Silent ResidenceImmerse yourself in cinematic horror that will not let you go until the very end of the mysterious story. Enjoy dynamic first-person cutscenes and take part in an incredible storyline.Dare you to challenge your fears and travel to an old abandoned evil house in a village in the hills and unravel all the disturbing secrets?Do you remember that your granny told you scary tales about a silent, abandoned playhouse where the evil spirit lady Hasshaku-sama (or slendrina for ex -
 Authenticator - 2FA & Password\xf0\x9f\x91\x8b Welcome to Authenticator - 2FA & Password, your dedicated solution for Two-Factor Authentication (2FA) and 2-Step Verification across all your accounts! Looking for a dependable and user-friendly 2FA & 2-Step Verification solution? Your search ends here!\xf0\x9f\x9a\x80 Safeguard your digital life with Authenticator - 2FA & Password! Enjoy unparalleled security for your online accounts, ensuring peace of mind with every login.Why choose Authenticat
Authenticator - 2FA & Password\xf0\x9f\x91\x8b Welcome to Authenticator - 2FA & Password, your dedicated solution for Two-Factor Authentication (2FA) and 2-Step Verification across all your accounts! Looking for a dependable and user-friendly 2FA & 2-Step Verification solution? Your search ends here!\xf0\x9f\x9a\x80 Safeguard your digital life with Authenticator - 2FA & Password! Enjoy unparalleled security for your online accounts, ensuring peace of mind with every login.Why choose Authenticat -
 Authenticator App - 2FA\xf0\x9f\x91\x8bWelcome to a new era of digital security with Authenticator App \xe2\x80\x93 2FA: a dedicated two-factor authentication(2-Step Verification) solution designed for all your accounts! Are you seeking a reliable and easy-to-use Two-Factor Authentication (2FA&2-St
Authenticator App - 2FA\xf0\x9f\x91\x8bWelcome to a new era of digital security with Authenticator App \xe2\x80\x93 2FA: a dedicated two-factor authentication(2-Step Verification) solution designed for all your accounts! Are you seeking a reliable and easy-to-use Two-Factor Authentication (2FA&2-St -
 Twilio Authy AuthenticatorAuthy brings the future of strong authentication to the convenience of your Android device.The Authy app generates secure 2 step verification tokens on your device. It helps you protect your account from hackers and hijackers by adding an additional layer of security.Why Au
Twilio Authy AuthenticatorAuthy brings the future of strong authentication to the convenience of your Android device.The Authy app generates secure 2 step verification tokens on your device. It helps you protect your account from hackers and hijackers by adding an additional layer of security.Why Au -
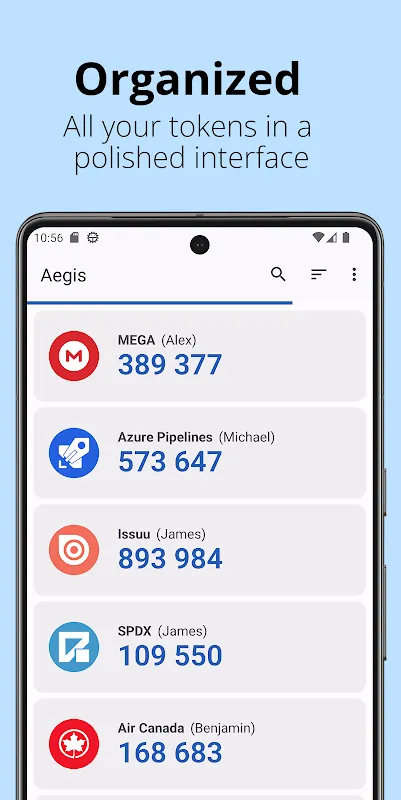
 Aegis Authenticator - 2FA AppAegis Authenticator is a free and open-source application designed for managing two-factor authentication (2FA) tokens for various online services. This app, often referred to simply as Aegis, provides users with a secure method to enhance the security of their online ac
Aegis Authenticator - 2FA AppAegis Authenticator is a free and open-source application designed for managing two-factor authentication (2FA) tokens for various online services. This app, often referred to simply as Aegis, provides users with a secure method to enhance the security of their online ac -
 The Eminence in Shadow RPGPlay the all-new online fantasy RPG based on the new hit anime, The Eminence in Shadow!\xe2\x97\x86 Experience The Eminence in Shadow's epic story modes!Continue the story with new chapters, beat exciting new challenges and get the latest characters after every new episode
The Eminence in Shadow RPGPlay the all-new online fantasy RPG based on the new hit anime, The Eminence in Shadow!\xe2\x97\x86 Experience The Eminence in Shadow's epic story modes!Continue the story with new chapters, beat exciting new challenges and get the latest characters after every new episode -
 IIJ SmartKeyOnly enterprise user needs to register your device.You can skip registering your device, if you don't need it.The IIJ SmartKey app produces one-time passwords that conform to TOTP (RFC 6238) standards and can be used in the 2-step verification authentication processes of a variety of onl
IIJ SmartKeyOnly enterprise user needs to register your device.You can skip registering your device, if you don't need it.The IIJ SmartKey app produces one-time passwords that conform to TOTP (RFC 6238) standards and can be used in the 2-step verification authentication processes of a variety of onl -
 Rain lashed against my hotel window in Berlin when the notification chimed. My CEO's frantic Slack message blinked: "EMERGENCY - AWS root account compromised." My fingers froze mid-sip of awful room-service coffee. That bitter taste wasn't just the stale brew - it was the metallic tang of dread. As cloud architect for a healthcare startup, I'd argued for months about ditching SMS verification. Now, our entire patient database hung in the balance while I scrambled for my backup Yubikey... only to
Rain lashed against my hotel window in Berlin when the notification chimed. My CEO's frantic Slack message blinked: "EMERGENCY - AWS root account compromised." My fingers froze mid-sip of awful room-service coffee. That bitter taste wasn't just the stale brew - it was the metallic tang of dread. As cloud architect for a healthcare startup, I'd argued for months about ditching SMS verification. Now, our entire patient database hung in the balance while I scrambled for my backup Yubikey... only to -
 Rain lashed against the Amsterdam hostel window as I frantically stabbed at my phone screen. My flight check-in closed in 18 minutes, but the airline app demanded that cursed six-digit passcode. Google Authenticator showed empty squares where my tokens should’ve been after last night’s OS update. Sweat glued my shirt to the plastic chair as I visualized missing this flight, stranded without access to funds or reservations. That’s when my trembling fingers remembered the blue shield icon buried i
Rain lashed against the Amsterdam hostel window as I frantically stabbed at my phone screen. My flight check-in closed in 18 minutes, but the airline app demanded that cursed six-digit passcode. Google Authenticator showed empty squares where my tokens should’ve been after last night’s OS update. Sweat glued my shirt to the plastic chair as I visualized missing this flight, stranded without access to funds or reservations. That’s when my trembling fingers remembered the blue shield icon buried i
