intrusion detection 2025-11-03T00:16:23Z
-
 Dream Detective: Merge Game"Dream Detective: A Casual Puzzle Adventure with a Twist of Merging and Mystery"Embark on an innovative puzzle-solving quest with "Dream Detective: Merge Game" \xe2\x80\x94 a unique casual puzzle adventure that seamlessly blends the joy of merging gameplay with the intrigu
Dream Detective: Merge Game"Dream Detective: A Casual Puzzle Adventure with a Twist of Merging and Mystery"Embark on an innovative puzzle-solving quest with "Dream Detective: Merge Game" \xe2\x80\x94 a unique casual puzzle adventure that seamlessly blends the joy of merging gameplay with the intrigu -
 Color Detectorby using the camera Color Detector can detect and identify the name of colors around you, and this Application is also able to detect colors contained in the image too!DETECTING AND IDENTIFY COLORS FROM THE CAMERA:detect and identify the name of colors in your environment! you can tap/swipe at different spots on the screen for the color at that point, as well as zoom and pause the camera to look at one frame more closely.Note: now in version (3.1.5) or higher you can use front cam
Color Detectorby using the camera Color Detector can detect and identify the name of colors around you, and this Application is also able to detect colors contained in the image too!DETECTING AND IDENTIFY COLORS FROM THE CAMERA:detect and identify the name of colors in your environment! you can tap/swipe at different spots on the screen for the color at that point, as well as zoom and pause the camera to look at one frame more closely.Note: now in version (3.1.5) or higher you can use front cam -
 Metal detectorMetal Detector is a mobile application designed for Android devices that allows users to detect the presence of metal objects in their vicinity. This app, often referred to simply as a metal detector, utilizes the magnetic sensor embedded in smartphones to measure variations in the mag
Metal detectorMetal Detector is a mobile application designed for Android devices that allows users to detect the presence of metal objects in their vicinity. This app, often referred to simply as a metal detector, utilizes the magnetic sensor embedded in smartphones to measure variations in the mag -
 Rain lashed against my apartment windows last Tuesday, turning the city into a watercolor smudge. I'd just microwaved sad leftovers when my phone buzzed – not a text, but a fragmented police report bleeding across the screen from that detective app I'd downloaded on a whim. "Partial fingerprint recovered near river... matches your suspect." My fork clattered onto the plate. Suddenly, the dreary afternoon snapped into razor-sharp focus. This wasn't passive entertainment; it felt like I'd been han
Rain lashed against my apartment windows last Tuesday, turning the city into a watercolor smudge. I'd just microwaved sad leftovers when my phone buzzed – not a text, but a fragmented police report bleeding across the screen from that detective app I'd downloaded on a whim. "Partial fingerprint recovered near river... matches your suspect." My fork clattered onto the plate. Suddenly, the dreary afternoon snapped into razor-sharp focus. This wasn't passive entertainment; it felt like I'd been han -
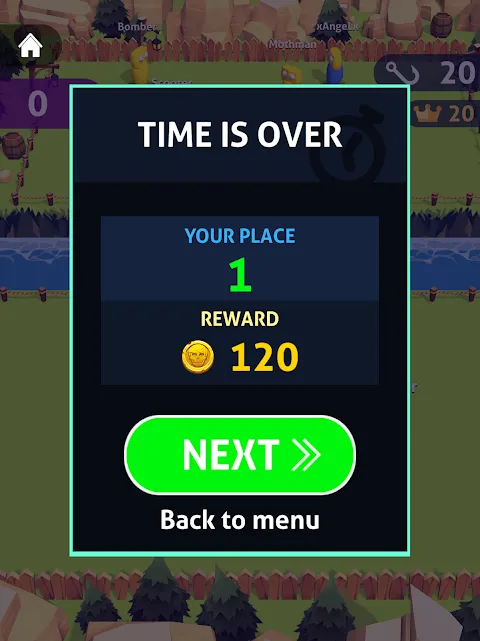 The fluorescent lights of the airport gate hummed like angry bees, casting a sickly glow on rows of plastic chairs bolted to the floor. I slumped deeper into the unforgiving seatback, flight delay notifications mocking me from the departures screen. That's when muscle memory took over—thumb sliding across cold glass, hunting for distraction in the digital wilderness. My index finger hovered then stabbed at the icon: a grappling hook coiled like a viper.
The fluorescent lights of the airport gate hummed like angry bees, casting a sickly glow on rows of plastic chairs bolted to the floor. I slumped deeper into the unforgiving seatback, flight delay notifications mocking me from the departures screen. That's when muscle memory took over—thumb sliding across cold glass, hunting for distraction in the digital wilderness. My index finger hovered then stabbed at the icon: a grappling hook coiled like a viper. -
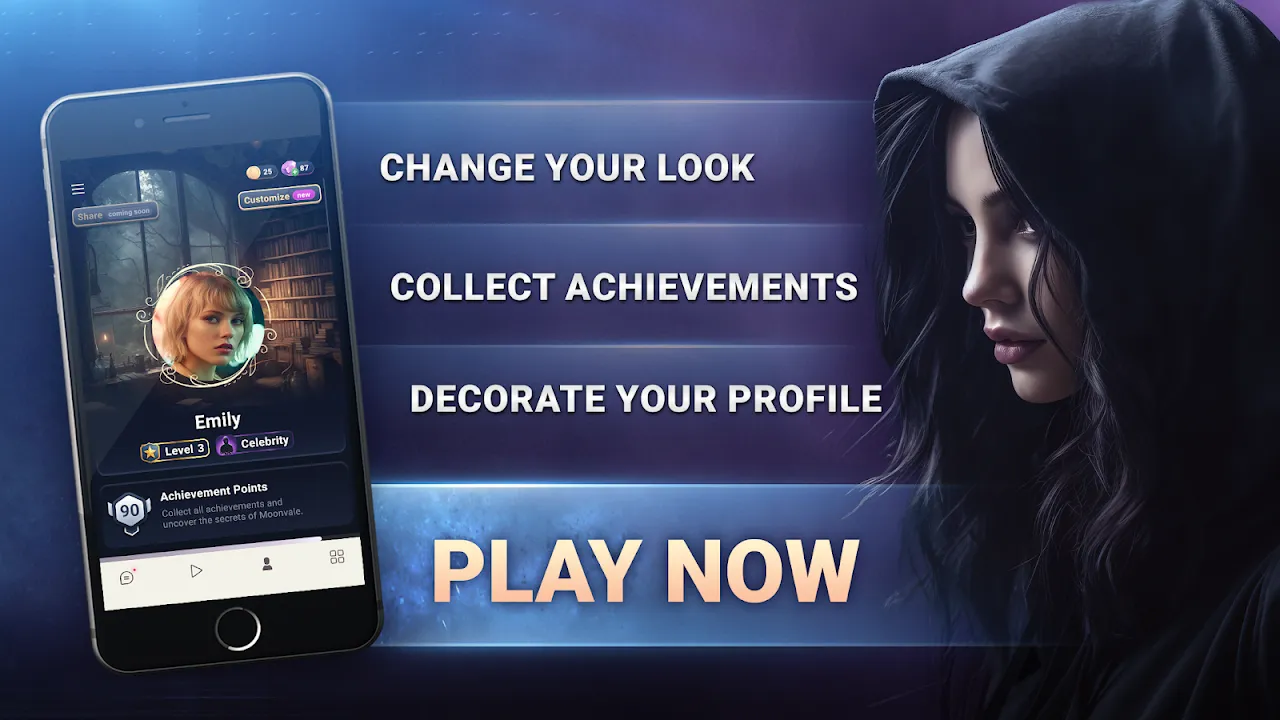
 MOONVALE - Detective StoryEmbark on a thrilling journey to unravel a genuine criminal case filled with mystery, hidden secrets, love and romance \xf0\x9f\x94\xaa\xe2\x9d\xa4\xef\xb8\x8f\xf0\x9f\x94\x8e. Immerse yourself in a modern murder mystery adventure that feels entirely lifelike! Challenge you
MOONVALE - Detective StoryEmbark on a thrilling journey to unravel a genuine criminal case filled with mystery, hidden secrets, love and romance \xf0\x9f\x94\xaa\xe2\x9d\xa4\xef\xb8\x8f\xf0\x9f\x94\x8e. Immerse yourself in a modern murder mystery adventure that feels entirely lifelike! Challenge you -
 Popup Ads Detector And RemoverAre you tired of the annoying pop-up ads that randomly appear on your screen and you don't know which app is causing the popup ads ? This app will help you find the app that is showing the popup ads on your phone\xe2\xad\x90\xef\xb8\x8f Here is how to use it :1 - Turn
Popup Ads Detector And RemoverAre you tired of the annoying pop-up ads that randomly appear on your screen and you don't know which app is causing the popup ads ? This app will help you find the app that is showing the popup ads on your phone\xe2\xad\x90\xef\xb8\x8f Here is how to use it :1 - Turn -
 I Am SecurityYour main task is to identify who can enter the club and who can't. Guests will line up, and you must decide if they are allowed in based on certain criteria. Some guests might try to sneak in with prohibited items, and it's up to you to find these hidden objects. Use a range of tools,
I Am SecurityYour main task is to identify who can enter the club and who can't. Guests will line up, and you must decide if they are allowed in based on certain criteria. Some guests might try to sneak in with prohibited items, and it's up to you to find these hidden objects. Use a range of tools, -
 Lie Detector PrankPolygraph Lie Detector is an application that simulates can detect lies through by examining the following physical changes in the body of the person being interrogated:- Pulse- Skin Conductivity- RespirationJust hold your finger on the detector and speak or think something. The App will give you the truth or lie!Disclaimer: This application is just a prank, a fun game and it is not a real life lie detector (polygraph). This is for Entertainment Purposes!More
Lie Detector PrankPolygraph Lie Detector is an application that simulates can detect lies through by examining the following physical changes in the body of the person being interrogated:- Pulse- Skin Conductivity- RespirationJust hold your finger on the detector and speak or think something. The App will give you the truth or lie!Disclaimer: This application is just a prank, a fun game and it is not a real life lie detector (polygraph). This is for Entertainment Purposes!More -
 RGB Color DetectorBest App to Detect and Pick Colors! Capture Millions of Shades from Any Image# Color DetectorUse your camera to snap a photo, or select an image from your gallery to identify vibrant colors within.Achieve extreme precision, detecting each pixel's hue.Access a variety of color formats and conversions: RGB, CMYK, HSV, HTML, HEX, and HSL.#\xc2\xa0Saved ColorSave vivid colors to your phone for future creativity.Ignite inspiration with our curated color lists, including web colors,
RGB Color DetectorBest App to Detect and Pick Colors! Capture Millions of Shades from Any Image# Color DetectorUse your camera to snap a photo, or select an image from your gallery to identify vibrant colors within.Achieve extreme precision, detecting each pixel's hue.Access a variety of color formats and conversions: RGB, CMYK, HSV, HTML, HEX, and HSL.#\xc2\xa0Saved ColorSave vivid colors to your phone for future creativity.Ignite inspiration with our curated color lists, including web colors, -
 Elector - Election ManagementThe future of the elections is already here!\xe2\x9c\x94Support on computer and apps\xe2\x9c\x94 Update votes in a simple way\xe2\x9c\x94 Real-time statistical analysis\xe2\x9c\x94 Reliability and stability\xe2\x9c\x94 User friendly\xe2\x9c\x94\xe2\x9c\x94 Characteristic written from the fieldThe characterization was written by staff members and experienced campaign managers who cumulatively passed dozens of election campaigns. We cut the advantages, exams what was m
Elector - Election ManagementThe future of the elections is already here!\xe2\x9c\x94Support on computer and apps\xe2\x9c\x94 Update votes in a simple way\xe2\x9c\x94 Real-time statistical analysis\xe2\x9c\x94 Reliability and stability\xe2\x9c\x94 User friendly\xe2\x9c\x94\xe2\x9c\x94 Characteristic written from the fieldThe characterization was written by staff members and experienced campaign managers who cumulatively passed dozens of election campaigns. We cut the advantages, exams what was m -
 Motion Detector A.I.Motion Detection A.I. is a home security camera app that uses advanced artificial intelligent algorithms to detect motion. on detection it can: sound alarm, save a picture, record video or all that. use it to keep an eye on your home, pet or office.new CameraX engine:https://youtu.be/HMlo6vC-MKchttps://youtube.com/shorts/DC_0eVi_N60https://youtube.com/shorts/Z-Q_CALYSiwhttps://youtu.be/xLurXveIR70https://youtube.com/shorts/L65d7W0kNpohttps://youtube.com/shorts/etuoA7yTIPgals
Motion Detector A.I.Motion Detection A.I. is a home security camera app that uses advanced artificial intelligent algorithms to detect motion. on detection it can: sound alarm, save a picture, record video or all that. use it to keep an eye on your home, pet or office.new CameraX engine:https://youtu.be/HMlo6vC-MKchttps://youtube.com/shorts/DC_0eVi_N60https://youtube.com/shorts/Z-Q_CALYSiwhttps://youtu.be/xLurXveIR70https://youtube.com/shorts/L65d7W0kNpohttps://youtube.com/shorts/etuoA7yTIPgals -
 All Objects DetectorAll Objects Detector free app for android will detect All devices like Mouse Computer and etc. infrared camera, so do not wait download this All Objects detector app for android now. The Radiation meter show possibility of Objects devices. people are searching for application to find like this application.
All Objects DetectorAll Objects Detector free app for android will detect All devices like Mouse Computer and etc. infrared camera, so do not wait download this All Objects detector app for android now. The Radiation meter show possibility of Objects devices. people are searching for application to find like this application. -
 Anti Spy Detector: Anti HackAnti Spy Detector is a mobile application designed to protect users from spyware, malware, and hacking attempts. This app, known simply as Anti Spy, provides a suite of tools to ensure the security of sensitive information on Android devices. Users can download Anti Spy t
Anti Spy Detector: Anti HackAnti Spy Detector is a mobile application designed to protect users from spyware, malware, and hacking attempts. This app, known simply as Anti Spy, provides a suite of tools to ensure the security of sensitive information on Android devices. Users can download Anti Spy t -
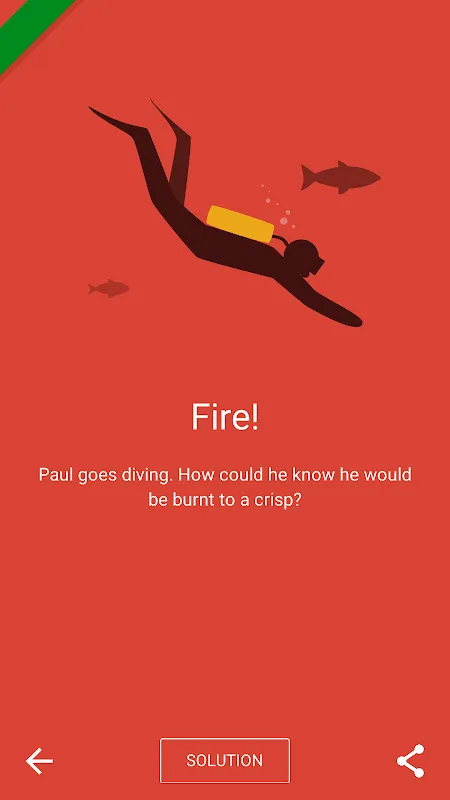 Rain lashed against the lakeside cabin windows as our board game pieces slid across warped cardboard. My brother tossed the dice in disgust when thunder drowned out Aunt Carol's storytelling attempt for the third time. Power had been out for hours, and that familiar restless tension thickened the air until Emma pulled her phone from a damp fleece pocket. "Remember that creepy app I mentioned?" The blue glow illuminated her mischievous grin as she loaded Dark Stories. What followed wasn't just en
Rain lashed against the lakeside cabin windows as our board game pieces slid across warped cardboard. My brother tossed the dice in disgust when thunder drowned out Aunt Carol's storytelling attempt for the third time. Power had been out for hours, and that familiar restless tension thickened the air until Emma pulled her phone from a damp fleece pocket. "Remember that creepy app I mentioned?" The blue glow illuminated her mischievous grin as she loaded Dark Stories. What followed wasn't just en -
 I was drowning in indecision at the bookstore, fingertips tracing the embossed cover of a novel I'd craved for months. The $28.99 price tag glared back like an accusation - was this hardback really worth skipping lunch for three days? My thumb instinctively found the app icon before my brain caught up, that little camera symbol now wired into my shopping reflexes. When the red scanning laser flickered to life, it felt like cracking open a secret vault.
I was drowning in indecision at the bookstore, fingertips tracing the embossed cover of a novel I'd craved for months. The $28.99 price tag glared back like an accusation - was this hardback really worth skipping lunch for three days? My thumb instinctively found the app icon before my brain caught up, that little camera symbol now wired into my shopping reflexes. When the red scanning laser flickered to life, it felt like cracking open a secret vault. -
 The fluorescent lights of the emergency room hummed like angry bees as I slumped in a plastic chair, my knuckles white around a lukewarm coffee cup. Twelve hours into my wife's labor, trapped in sterile limbo between panic and exhaustion, I craved mental escape more than oxygen. That's when my thumb instinctively stabbed at the detective adventure icon – a split-second decision that yanked me from hospital purgatory into the fog-drenched streets of Victorian London.
The fluorescent lights of the emergency room hummed like angry bees as I slumped in a plastic chair, my knuckles white around a lukewarm coffee cup. Twelve hours into my wife's labor, trapped in sterile limbo between panic and exhaustion, I craved mental escape more than oxygen. That's when my thumb instinctively stabbed at the detective adventure icon – a split-second decision that yanked me from hospital purgatory into the fog-drenched streets of Victorian London. -
 Qibla Direction - Prayer TimesAl Quran: Qibla Direction a sacred app for Muslims, Holy Quran: Qibla Compass supports religious practices with features like 15-line Holy Quran Offline reading, making it easier to learn and recite the Al Quran Kareem. This Quran Sharif: Qibla Finder app serves as a reminder to remember Allah everywhere, keeping you connected with the Al Quran and strengthening your faith at all times.Connected with your ultimate Al Quran: Qibla Direction, Prayer Times that's your
Qibla Direction - Prayer TimesAl Quran: Qibla Direction a sacred app for Muslims, Holy Quran: Qibla Compass supports religious practices with features like 15-line Holy Quran Offline reading, making it easier to learn and recite the Al Quran Kareem. This Quran Sharif: Qibla Finder app serves as a reminder to remember Allah everywhere, keeping you connected with the Al Quran and strengthening your faith at all times.Connected with your ultimate Al Quran: Qibla Direction, Prayer Times that's your

