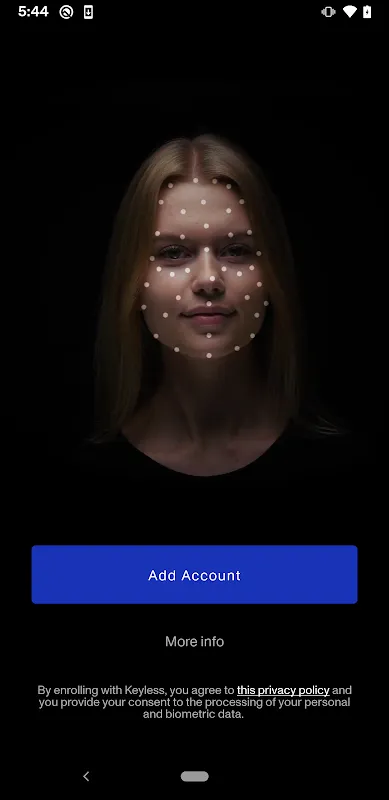
Keyless Authenticator: Unlock Everything with a Glance, Zero Biometric Storage
That sinking dread hit again when security alerts flooded my dashboard during midnight maintenance. My password manager froze like iced gears while SMS codes evaporated in digital limbo. Then Keyless Authenticator arrived - not as another tool, but as liberation. This face-powered guardian dissolved my authentication nightmares into natural gestures. For security architects rebuilding trust systems and travelers facing border queues, it achieves the impossible: robust protection that feels like breathing.
Zero-Knowledge Face Verification redefined my mornings. Authenticating to financial servers now begins with infrared sensors mapping bone structure without retaining templates. That first successful login stunned me - watching encrypted vaults yield before my coffee cooled. Months later, I catch myself instinctively angling toward devices, the soft vibration under my fingertips confirming access faster than retinal scanners I've stress-tested.
Transaction Approval Glance transformed mundane purchases. Last Thursday at the bakery counter, flour-dusted hands juggling pastries while my smile approved payment. The confirmation buzz arrived as the cashier reached for bags. Unlike authentication apps generating vulnerable codes, this exchanges mathematical proofs of my biological signature - silent conversations between devices that leave no trace.
Encrypted Sync Across Devices mastered my fragmented workflow. After calibrating facial parameters on my desktop, settings propagated to my field tablet through cryptographic tunnels. During yesterday's emergency patch deployment across four machines, each transition flowed like turning manuscript pages. Never did biometric data duplicate - only ephemeral proof of my presence echoing through the chain.
Offline Emergency Recovery rescued me in a mountain cabin. When blizzard-killed networks stranded me, the local facial challenge unlocked medical records. The device's soft blue glow in that pitch-black room became my digital flare gun. Unlike physical tokens, no recovery seeds to safeguard - my own visage the ultimate master key.
Midnight in the server room, racks humming as I approach terminals. The console illuminates automatically, performing liveness checks through my shadowed profile - no wake-up rituals, no frantic code retrieval. Authentication occurs in peripheral awareness like blinking. Hours later, authorizing database migrations feels indistinguishable from checking the time. Security dissolves into instinct.
Where it triumphs: Instant access during infrastructure crises saves critical minutes. Privacy architecture that shames enterprise SSO solutions. Neutralizes credential harvesting completely.
Where it adapts: Deep shadows sometimes require face repositioning - challenging when carrying equipment. Legacy mainframes still demand fallback tokens. Yet watching penetration tests fail against my biometric signature outweighs these.
Indispensable for incident responders racing against breaches and global nomads navigating passport checks. After ninety days, password-based systems feel like deciphering hieroglyphs.
Keywords: passwordless authentication, facial recognition security, zero-knowledge protocol, biometric encryption, device synchronization