Dead Drops and Digital Shields
Dead Drops and Digital Shields
Rain lashed against the safehouse window as my fingers trembled over the burner phone. Outside, regime patrols swept the blacked-out streets hunting for dissidents like me. The memory card in my palm contained identities of hidden families - coordinates that meant life or death. My usual encrypted channels had been compromised last week when a single mistyped PGP key turned a rescue mission into a funeral procession. Tonight's transmission couldn't fail. When I tapped the unassuming blue icon - Egress - its encryption wrapped around my message like Kevlar weaving itself in real-time. No complex key exchanges, no agonizing wait while algorithms churned. Just a swift swipe and the gut-punch relief watching those double padlocks snap shut before transmission.
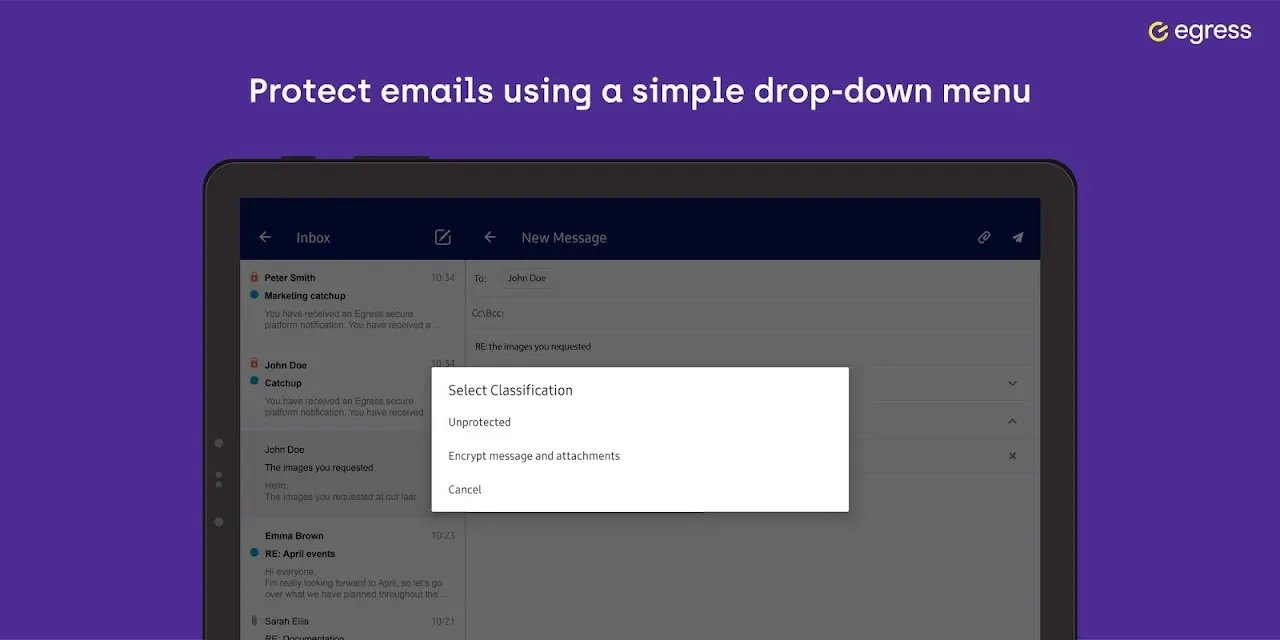
The Ghost in the Machine
What makes this armor so unnervingly light? Underneath that minimalist interface lies military-grade AES-256 encryption that executes locally on-device before data touches any network. Unlike those clunky legacy systems requiring manual key exchanges, Egress uses dynamic session keys generated per message that self-destruct after decryption. I learned this the hard way when interrogators grabbed my colleague's phone in Minsk - finding only cryptographic confetti where sensitive manifests should've been. Yet this technical marvel has its thorns. Try sending high-res intel photos during a signal-blackout and watch your battery hemorrhage 20% in minutes as the app wrestles with on-device media encryption. There's visceral terror in seeing your power bar bleed crimson while boots echo in the stairwell.
Silence in the Static
Last Tuesday proved why metadata kills more effectively than bullets. My team had been rotating through three encrypted mail services, yet regime trackers kept triangulating our safehouses through sender-receiver patterns. Enter Egress' metadata stripping - it doesn't just encrypt content but vaporizes the digital footprints around it. No IP trails, no geographic breadcrumbs. When I sent evacuation plans from that moving truck in Cherkasy, the recipient saw only a blank geographic canvas. This isn't just privacy; it's active camouflage. Still, I curse its stubborn refusal to auto-delete messages after read receipts. Found myself manually purging threads at 3AM, bleary-eyed and jumpy - every uncleared message feeling like an unsecured landmine in our operation.
That pouring night in Odessa, as I huddled behind dumpsters transmitting extraction points, Egress' real genius struck me. Not in its enterprise-level security protocols, but in its merciless efficiency. While patrol flashlights swept the alley, I managed to encrypt-drop six coordinates in under 90 seconds - each wrapped in unique cryptographic layers faster than I could wipe rainwater from the screen. Earlier that year, similar transmissions took fifteen agonizing minutes with other tools. Minutes where comrades died. Yet for all its life-saving speed, I'll never forgive how its "urgent message" notification once blared full volume during a checkpoint search. Some flaws cut deeper than code.
The Weight of Trust
True security tools reveal their character during collapse. When Russian jammers flooded our district last month, every "secure" app choked except Egress' fallback to TLS 1.3 tunneling. Watching it reroute through three obfuscated nodes while other platforms showed dead icons felt like witnessing digital necromancy. Its zero-trust architecture means even app developers can't access my keys - a revelation after learning our previous provider had government backdoors. But this fortress mentality exacts a toll. I've spent nights drilling grandmothers on its authentication steps, watching their eyes glaze over at certificate pinning explanations. Sometimes security feels like building an impenetrable vault... then realizing you've locked the keys inside with civilians still trapped.
Three weeks ago, as artillery shook our basement command post, I finally understood this app's brutal poetry. While plaster dust snowed onto our laptops, the team lead transmitted final stand coordinates through Egress with two shattered fingers. No passcode - just facial recognition scanning through blood and grime. Later, survivors confirmed the message's SHA-256 hash matched perfectly despite the chaos. Yet I still rage at its lack of emergency duress codes. That moment when armed police demand your unlock? Either martyrdom or betrayal - no middle ground. Perfection remains lethally elusive.
Tonight the rain has stopped. Somewhere beyond these walls, families breathe freely because encrypted data moved faster than tyranny's grasp. I trace the app's icon - this pocket-sized bastion that cost us nothing but demands everything in return. Its end-to-end encryption isn't just technology; it's the digital equivalent of whispering secrets into a thunderstorm. But tomorrow I'll switch to temporary burners again, because no armor stays impenetrable forever. Not in this game. Not when human error remains the weakest cipher.
Keywords:Egress Secure Mail,news,encryption,data privacy,secure communication









