Digital Wolves at the Cafe Door
Digital Wolves at the Cafe Door
The smell of burnt espresso beans and the clatter of keyboards surrounded me at St. Oberholz that Tuesday. My Berlin work ritual – laptop open, research tabs bleeding across the screen – shattered when a notification blinked: "Login attempt blocked: Minsk, Belarus." Ice shot through my veins. Public Wi-Fi had always been a necessary evil, but this? This felt like a pickpocket slipping fingers into my digital ribs while I sipped latte art. My hands shook scrolling through the logs. Three attempts in ten minutes. Someone was hunting.
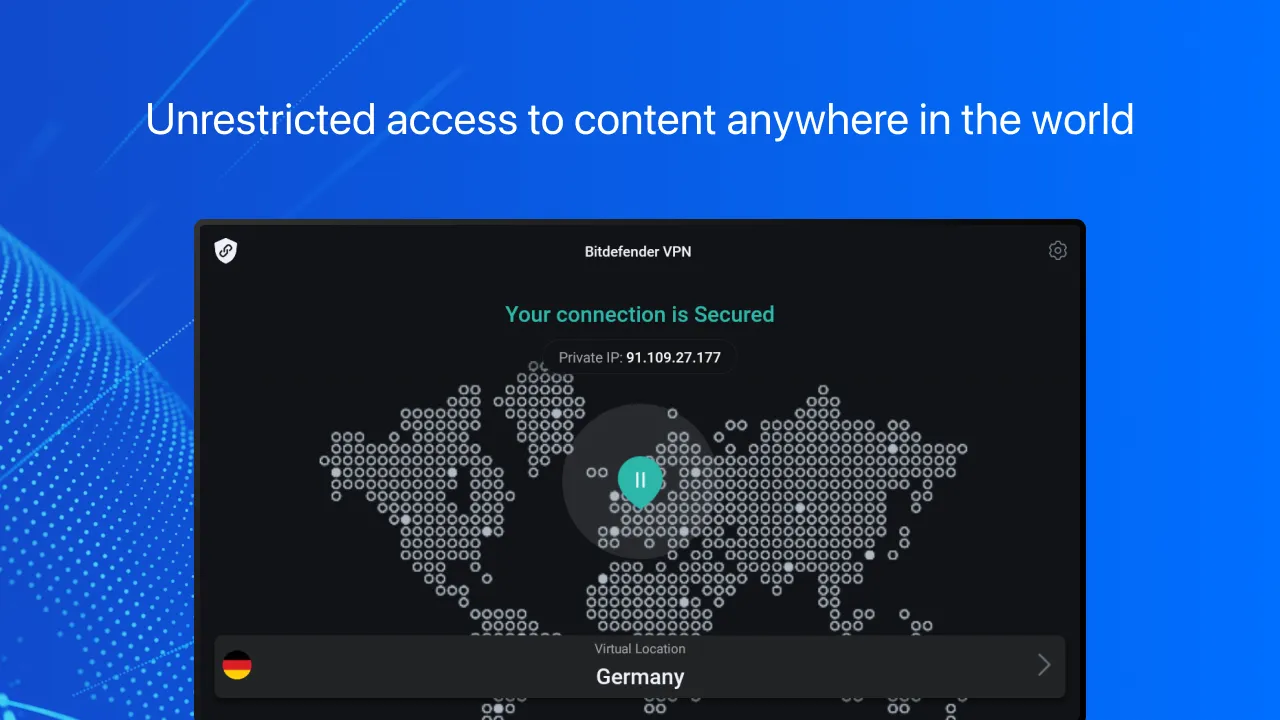
That's when Bitdefender's encrypted lifeline became more than an app icon. I jammed my thumb on the toggle, watching the interface morph from idle gray to aggressive green. Instantaneous. No spinning wheel of doom, no "connecting..." purgatory. Just a visceral thunk in my gut as the shield slammed down. Suddenly my panic tunnel-vision cleared enough to notice the cafe's surveillance camera above me, its red LED blinking like a predator's eye. Were they watching? Mapping keystrokes? I traced the VPN's kill-switch setting with sweaty fingers – that beautiful failsafe guaranteeing my data would vaporize if the connection flickered. Not a single byte would escape.
What followed wasn't just protection; it was revelation. As I dove into server locations, I realized Bitdefender's magic wasn't wizardry but WireGuard protocol – that lean, mean tunneling engine operating at kernel level. While other VPNs bog down devices with bureaucratic layers, this thing moved data like a ghost train. I tested it mid-crisis: fired up a 4K documentary stream while running a vulnerability scan. Zero lag. The speedometer feature showed 89Mbps down – 98% of my bare connection speed. How? No TCP overhead. Just raw UDP packets wrapped in cryptographic armor, screaming through the pipes. I laughed out loud when the Berlin server I'd manually selected responded in 8ms. Nearby enough to taste the currywurst.
But the real gut-punch came weeks later. Back home, my "smart" TV started serving ads for hiking boots after I'd researched trails near Berchtesgaden. Coincidence? Bullshit. I unleashed Bitdefender's ad-blocking DNS like a scalpel. Watching those invasive banners dissolve felt like power-washing grime off my digital life. The app's Threat Prevention feature became my silent sentry – catching cryptojackers trying to hijack my browser for Monero mining, vaporizing malware-hosting domains before they loaded. Each blocked threat felt personal. Vindictive.
Yet perfection? Hell no. The mobile interface occasionally treats my thumbs like elephant trunks – hitting the tiny server list arrow requires surgeon precision. And their "unlimited devices" promise? Try explaining that to my ancient Kindle Paperwhite. Configuration requires a networking degree they assume everyone has. But when I discovered their RAM-only servers? That rage evaporated. No hard drives. Every session wiped on reboot. Even if authorities seized their hardware, they'd get digital dust. That's anonymity you can feel in your bones.
Now? I wear this VPN like a second skin. At airports, I smirk watching travelers blindly accept sketchy Wi-Fi terms. In meetings, I discreetly flip servers when competitors get too nosy about my screen. It's not paranoia – it's hearing the lock click on a bank vault holding your memories, conversations, naked selfies. Bitdefender didn't just secure my connection; it rewired my instincts. I used to see public networks as convenience. Now I see them as crime scenes waiting to happen – and I walk through every one armored in 256-bit encryption, leaving no footprints.
Keywords:Bitdefender VPN,news,public WiFi security,WireGuard protocol,RAM-only servers








