My Security Blanket Meltdown
My Security Blanket Meltdown
The Istanbul airport lounge hummed with exhausted travelers when my phone suddenly went ice-cold in my palm. Not physically - that would've been simpler - but digitally frozen mid-scroll through vacation photos. My screen flickered like a dying firefly before displaying that gut-punch symbol: a padlock with red lightning bolts. My throat tightened as I imagined Russian ransomware gangs dancing through my device while I sipped lukewarm chai. As a freelance penetration tester, I'd mocked clients for BYOD carelessness, yet here I was with three years of client contracts and passport scans held hostage by what smelled like a zero-day exploit.
Fingers trembling, I downloaded that security app everyone in infosec circles whispered about - the one that supposedly sniffed out kernel-level breaches before they bloomed. Installation felt like performing open-heart surgery on a rollercoaster. Each permission prompt made me wince: "Allow real-time memory scanning?" Yes, even if it devours battery. "Grant vulnerability monitor access?" Absolutely, though it might slow my ancient Pixel to a crawl. The initial scan progress bar inched forward like a condemned prisoner walking the plank while airport Wi-Fi taunted me with 56k modem speeds.
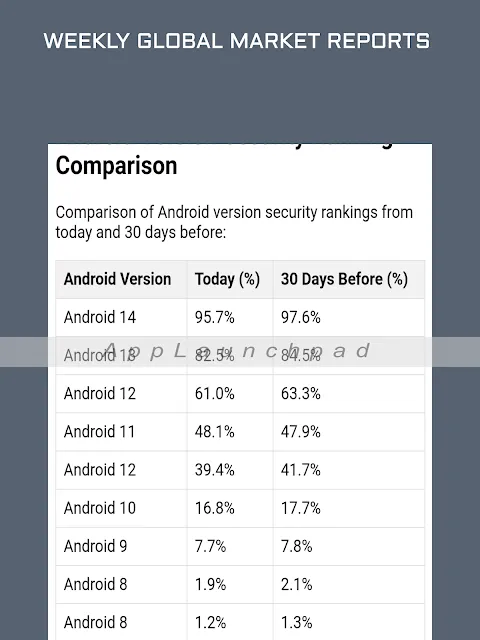
When the results flashed crimson, I nearly dropped my phone into the chai. Not one but three active threats: a privilege escalation attack nesting in my Bluetooth stack, some sketchy overlay malware masquerading as a calculator app, and - most viciously - a fileless exploit living entirely in RAM like a digital ghost. The app visualized them as pulsing red tumors in a 3D model of my Android architecture, making my stomach lurch. That visualization wasn't just pretty UI glitter - it mapped exactly to how Linux kernel vulnerabilities propagate through SELinux contexts. Seeing the attack vector illustrated from init process to compromised system server drove home how brittle mobile security really is beneath the shiny GUI veneer.
Over the next week, I became obsessed with the app's quarantine module. Watching it surgically disentangle malicious processes from legitimate ones felt like witnessing a hostage rescue operation. It didn't just nuke threats; it preserved my banking app's cached credentials while incinerating the keylogger piggybacking on its accessibility permissions. The forensic report revealed the attack originated from a compromised charging station - a risk I'd theoretically known about but practically ignored while desperately juicing up during my layover in Minsk. My hubris tasted more bitter than three-day-old airport coffee.
But let's not paint this as some digital savior fantasy. The app's constant vigilance comes with brutal tradeoffs. My phone now heats up like a griddle during deep scans, and battery life evaporates faster than my faith in human decency when it catches yet another drive-by download attempt from sketchy ad networks. Last Tuesday, it falsely flagged my authenticator app as malware during a time-sensitive crypto transfer, triggering a 15-minute panic attack before manual override. And don't get me started on the update notifications - they arrive with the subtlety of air raid sirens at 3 AM, once literally vibrating off my nightstand.
Yet here's the twisted truth: I've grown perversely fond of these disruptions. That momentary rage when it throttles my gaming performance? It's the price for knowing my device isn't secretly mining Monero for some script kiddie. The false positives? Annoying but reassuring - like an overzealous guard dog that occasionally bites the mailman. When I see it silently block a zero-click exploit via a malformed PNG file, I feel a surge of vindication sharper than any caffeine hit. This app hasn't just protected my data; it's rewired my relationship with technology from naive trust to healthy paranoia. My phone is no longer a magic slab - it's a battlefield, and I finally have a decent trench.
Keywords:Android Exploits,news,mobile security,vulnerability scanner,zero-day protection









