Shizuku: Unlocking Android's Hidden Gates
Shizuku: Unlocking Android's Hidden Gates
That cursed Thursday morning still burns in my memory - my hands trembling over a development build while system-level permissions mocked me. I'd spent three nights reverse-engineering notification channels when Android 13's new restrictions slammed the door. Every prototype crashed with vicious SecurityException errors that felt like personal insults. Rooting the test device wasn't an option - not with banking apps and corporate emails on it - yet without SYSTEM_ALERT_WINDOW permissions, my entire workflow was bricked. The keyboard imprinted on my forehead where I'd slumped in defeat, smelling burnt coffee and despair.
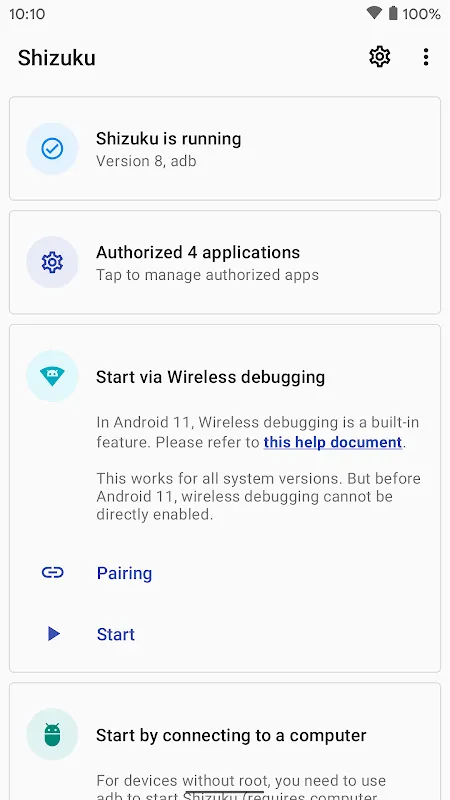
Reddit threads blurred before my sleep-deprived eyes when someone mentioned "ADB magic without root compromises". Skepticism warred with desperation as I typed the terminal commands: adb shell sh /sdcard/Android/data/moe.shizuku.privileged.api/start.sh. When the Shizuku notification materialized - that minimalist white circle on purple - my breath hitched. Suddenly, App Ops granted me permission control like a locksmith handing over master keys. I actually laughed aloud when Greenify hibernated system apps with surgical precision, the RAM counter climbing like a liberated prisoner.
But euphoria met reality at 3 AM when Android's aggressive memory management killed Shizuku's background service mid-debugging. The sudden permission revocation felt like betrayal - my own device sabotaging me. That's when I discovered the brutal poetry of its design: Shizuku doesn't fight the system but hijacks its plumbing. By binding to ADB's debug socket, it creates a privileged tunnel where apps whisper requests through a secondary user-space daemon. No root exploits, no bootloader unlocks - just cleverly repurposed developer pathways. The realization hit me while reinitializing via wireless debugging: This wasn't hacking; it was diplomatic negotiation with the OS.
My love-hate relationship crystallized during the Android 14 beta. Shizuku's v13.1.0 update handled Scoped Storage changes beautifully, yet every reboot demanded re-enabling through ADB like some digital penance. I'd curse the ritual while simultaneously marveling at how it transformed my tablet into a Frankenstein's monster of functionality - IceBox freezing bloatware, Sensor Disabler killing accidental rotations, all without touching the kernel. The contradiction defined it: simultaneously fragile as a house of cards and revolutionary as a skeleton key.
What truly haunts me is the ethical unease. That first time I accessed UsageStats without root, I felt like I'd discovered government secrets. Shizuku exposes Android's dirty secret: how much power remains accessible if you know which backdoors to jiggle. Yet this power demands constant vigilance - one mistyped ADB command could brick devices. I've developed muscle memory for the startup sequence, fingers dancing across terminals with the reverence of a safecracker. The relief when the service initializes never fades; it's digital morphine for permission headaches.
Now when junior developers ask about testing privileged intents, I demonstrate Shizuku with theatrical flair - watching their eyes widen as I toggle Airplane mode programmatically on an unrooted Pixel. But I always warn them about the price: the persistent notification, the reboot rituals, the terrifying moment when Android Security patches might close this loophole forever. We're dancing in a narrow beam of light between Google's intentions and Android's latent capabilities, and Shizuku remains our flickering torch in the darkness.
Keywords:Shizuku,news,ADB permissions,Android development,system-level access









