Wickr Enterprise: Military-Grade Encrypted Collaboration for Critical Business Communications
During a high-stakes merger negotiation, my palms sweat as I type confidential figures into our legacy chat platform. That sinking feeling vanished when our IT department deployed Wickr Enterprise. Suddenly, sensitive discussions felt like whispers in a vault—utterly contained yet effortlessly accessible across our global team. This isn’t just another messaging app; it’s an armored vehicle for corporate intelligence, designed exclusively for organizations prioritizing operational secrecy above all.
Self-Hosted Private Network became my sanctuary. The moment our administrator provisioned my device, I felt the weight lift—no more VPN juggling or fearing cloud vulnerabilities. Our servers house everything, and that physical control manifests as psychological relief during midnight crisis calls. When competitors suffered breaches last quarter, our team exchanged knowing glances; our data remained untouched behind its digital moat.
Using Multilayered Encryption feels like sealing documents in titanium envelopes. I recall sending blueprints to our Berlin office during a transit layover. Watching the dual-padlock icon appear gave me the same assurance as hearing a safe click shut. Even public Wi-Fi risks dissolve—each character gets scrambled through multiple cryptographic layers before transmission.
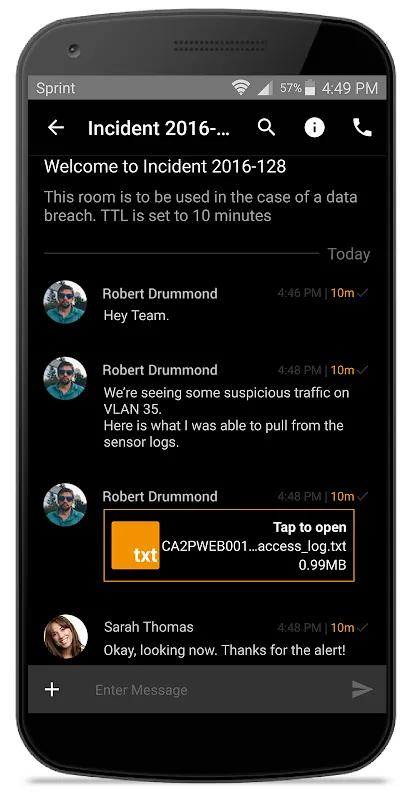
Ephemeral Messaging transformed how we handle sensitive projects. Setting a 24-hour lifespan for acquisition strategy threads means I no longer lie awake wondering about digital footprints. Last Tuesday, when my CEO accidentally pasted credentials into a room? Watching them evaporate after sixty seconds felt like witnessing evidence burn in a fireplace—controlled destruction at its finest.
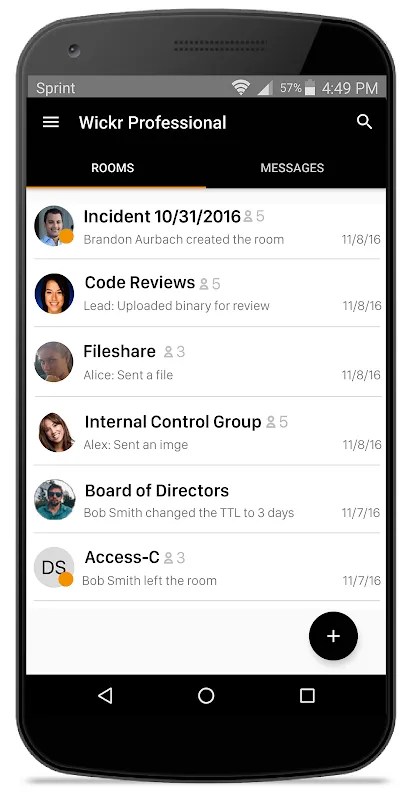
Secure Project Rooms reshaped our workflow. Creating a room for patent development was seamless; invitation controls ensured only R&D leads entered. What stunned me was discovering hidden utility: during investor demos, we now share prototypes directly within rooms. Seeing colleagues annotate 3D model files without ever downloading them? That’s when I grasped how deeply security was woven into collaboration.
Contact Verification answered my deepest paranoia. After manually confirming my CFO’s identity badge, that green shield icon became my compass. Last month, when a spoofed account mimicked our counsel, the missing verification badge stopped me mid-type. My knuckles whitened realizing how close we came to disaster—now I instinctively check before sending even "good morning."
Pre-dawn scenarios test true mettle. Picture 3 AM in your home office: rain pelts windows while you decrypt Q4 reports on your tablet. Muscle memory guides you—swipe, fingerprint scan, instant access. No frantic password resets. Just encrypted spreadsheets glowing under lamplight as wind howls outside. Or during cross-continental flights, when turbulence rattles tray tables yet your encrypted video conference with intelligence officers streams uninterrupted—that’s infrastructure transcending convenience, becoming operational lifeline.
The brilliance? Launch speed rivals texting apps—critical when arbitrage windows slam shut. Message searches feel psychic; typing "breach protocol" instantly surfaces every relevant file and thread across years. But friction exists: onboarding requires IT coordination, and ephemerality’s double-edged sword means no message recovery. I once lost vital notes after misjudging timer settings—a security triumph, yet a user’s groan moment. Still, for defense contractors drafting field operatives or pharmaceutical firms sharing trial data? These tradeoffs pale against the fortress it provides.
Keywords: enterprise encryption, secure collaboration, ephemeral messaging, private network, contact verification