Encrypted Security 2025-10-30T11:48:18Z
-
 Citizen Security-GavaAppM7 is a citizen and urban security application that the Police or Guardia Urbana of your municipality makes available to you to IMPROVE YOUR PERSONAL SAFETY in any situation of risk or danger.Main functions of the AppM7:EMERGENCY CALLS AND MESSAGES: Sending your location for immediate location and tracking. New: Widgets: It is not necessary to open the AppM7 to send an emergency.SEND INCIDENTS: To the Local Police or Guardia Urbana of the attached municipalities, with the
Citizen Security-GavaAppM7 is a citizen and urban security application that the Police or Guardia Urbana of your municipality makes available to you to IMPROVE YOUR PERSONAL SAFETY in any situation of risk or danger.Main functions of the AppM7:EMERGENCY CALLS AND MESSAGES: Sending your location for immediate location and tracking. New: Widgets: It is not necessary to open the AppM7 to send an emergency.SEND INCIDENTS: To the Local Police or Guardia Urbana of the attached municipalities, with the -
 Trustd Mobile SecurityTrustd detects malicious apps, dangerous WiFi networks and protects against scam websites and SMS phishing attacks. No tracking. No ads. We fight for your privacy.+++Trustd is a free mobile security and privacy app built in the UK by cybersecurity specialists. The app alerts you when suspicious behaviour is detected on your phone. Trustd uses AI to detect even brand new malicious app behaviour, phishing scams and vulnerable WiFi networks so you\xe2\x80\x99re protected in re
Trustd Mobile SecurityTrustd detects malicious apps, dangerous WiFi networks and protects against scam websites and SMS phishing attacks. No tracking. No ads. We fight for your privacy.+++Trustd is a free mobile security and privacy app built in the UK by cybersecurity specialists. The app alerts you when suspicious behaviour is detected on your phone. Trustd uses AI to detect even brand new malicious app behaviour, phishing scams and vulnerable WiFi networks so you\xe2\x80\x99re protected in re -
 Citizen Security-EspluguesAppM7 is a citizen and urban security application that the Police or Guardia Urbana of your municipality makes available to you to IMPROVE YOUR PERSONAL SAFETY in any situation of risk or danger.Main functions of the AppM7:EMERGENCY CALLS AND MESSAGES: Sending your location for immediate location and tracking. New: Widgets: It is not necessary to open the AppM7 to send an emergency.SEND INCIDENTS: To the Local Police or Guardia Urbana of the attached municipalities, wit
Citizen Security-EspluguesAppM7 is a citizen and urban security application that the Police or Guardia Urbana of your municipality makes available to you to IMPROVE YOUR PERSONAL SAFETY in any situation of risk or danger.Main functions of the AppM7:EMERGENCY CALLS AND MESSAGES: Sending your location for immediate location and tracking. New: Widgets: It is not necessary to open the AppM7 to send an emergency.SEND INCIDENTS: To the Local Police or Guardia Urbana of the attached municipalities, wit -
 ESET Endpoint SecurityProtect your organization's smartphones and tablets with next-level security. ESET Endpoint Security eliminates malware and phishing, protects your data in case of theft, and provides application control and other advanced features. The solution is compatible with ESET's MDM via the ESET PROTECT management console. Please note that this is a business application that requires an active ESET account. For more information, contact your IT department or visit the ESET website.
ESET Endpoint SecurityProtect your organization's smartphones and tablets with next-level security. ESET Endpoint Security eliminates malware and phishing, protects your data in case of theft, and provides application control and other advanced features. The solution is compatible with ESET's MDM via the ESET PROTECT management console. Please note that this is a business application that requires an active ESET account. For more information, contact your IT department or visit the ESET website. -
 Security Camera CZTurn your old smartphone or tablet into online monitoring camera. This app is exclusively designed for parental monitoring, monitoring of your property or pets. This app offers many functions and all features are FREE!This application enables to record detected motions as HD videos or as images in high resolution. Resolution of images isn't limited.All features are FREE:Smart motion detection.Exceptional resistance to false alarms.Live HD video and video recording.Two way talk-
Security Camera CZTurn your old smartphone or tablet into online monitoring camera. This app is exclusively designed for parental monitoring, monitoring of your property or pets. This app offers many functions and all features are FREE!This application enables to record detected motions as HD videos or as images in high resolution. Resolution of images isn't limited.All features are FREE:Smart motion detection.Exceptional resistance to false alarms.Live HD video and video recording.Two way talk- -
 Malwarebytes Mobile SecurityYour Ultimate Mobile Guardian \xf0\x9f\x9b\xa1\xef\xb8\x8fStop Threats in their Tracks \xf0\x9f\x95\xb5\xef\xb8\x8f\xe2\x80\x8d\xe2\x99\x80\xef\xb8\x8fNEW! Scam Guard: Stop scammers in their tracks with instant advice. Just upload text or a screenshot and get real-time gu
Malwarebytes Mobile SecurityYour Ultimate Mobile Guardian \xf0\x9f\x9b\xa1\xef\xb8\x8fStop Threats in their Tracks \xf0\x9f\x95\xb5\xef\xb8\x8f\xe2\x80\x8d\xe2\x99\x80\xef\xb8\x8fNEW! Scam Guard: Stop scammers in their tracks with instant advice. Just upload text or a screenshot and get real-time gu -
 ZoneAlarm Mobile SecurityZoneAlarm Mobile Security is an antivirus application designed to provide protection for mobile devices against various security threats. Developed by Check Point, a leader in cybersecurity, ZoneAlarm Mobile Security incorporates advanced technology to safeguard data and pri
ZoneAlarm Mobile SecurityZoneAlarm Mobile Security is an antivirus application designed to provide protection for mobile devices against various security threats. Developed by Check Point, a leader in cybersecurity, ZoneAlarm Mobile Security incorporates advanced technology to safeguard data and pri -
 I Am SecurityYour main task is to identify who can enter the club and who can't. Guests will line up, and you must decide if they are allowed in based on certain criteria. Some guests might try to sneak in with prohibited items, and it's up to you to find these hidden objects. Use a range of tools,
I Am SecurityYour main task is to identify who can enter the club and who can't. Guests will line up, and you must decide if they are allowed in based on certain criteria. Some guests might try to sneak in with prohibited items, and it's up to you to find these hidden objects. Use a range of tools, -
 TotalAV Mobile SecurityTotalAV Mobile Security is a mobile application designed to provide comprehensive protection for Android devices. This app offers a range of features aimed at enhancing security and privacy while browsing the web and using various applications. Users can download TotalAV Mobil
TotalAV Mobile SecurityTotalAV Mobile Security is a mobile application designed to provide comprehensive protection for Android devices. This app offers a range of features aimed at enhancing security and privacy while browsing the web and using various applications. Users can download TotalAV Mobil -
 Bitdefender Mobile SecurityBitdefender Mobile Security & Antivirus delivers industry-leading protection for your Android phone or tablet. It safeguards against viruses, malware, and online threats, all while keeping your personal data safe\xe2\x80\x94and with minimal battery impact.Get the best prot
Bitdefender Mobile SecurityBitdefender Mobile Security & Antivirus delivers industry-leading protection for your Android phone or tablet. It safeguards against viruses, malware, and online threats, all while keeping your personal data safe\xe2\x80\x94and with minimal battery impact.Get the best prot -
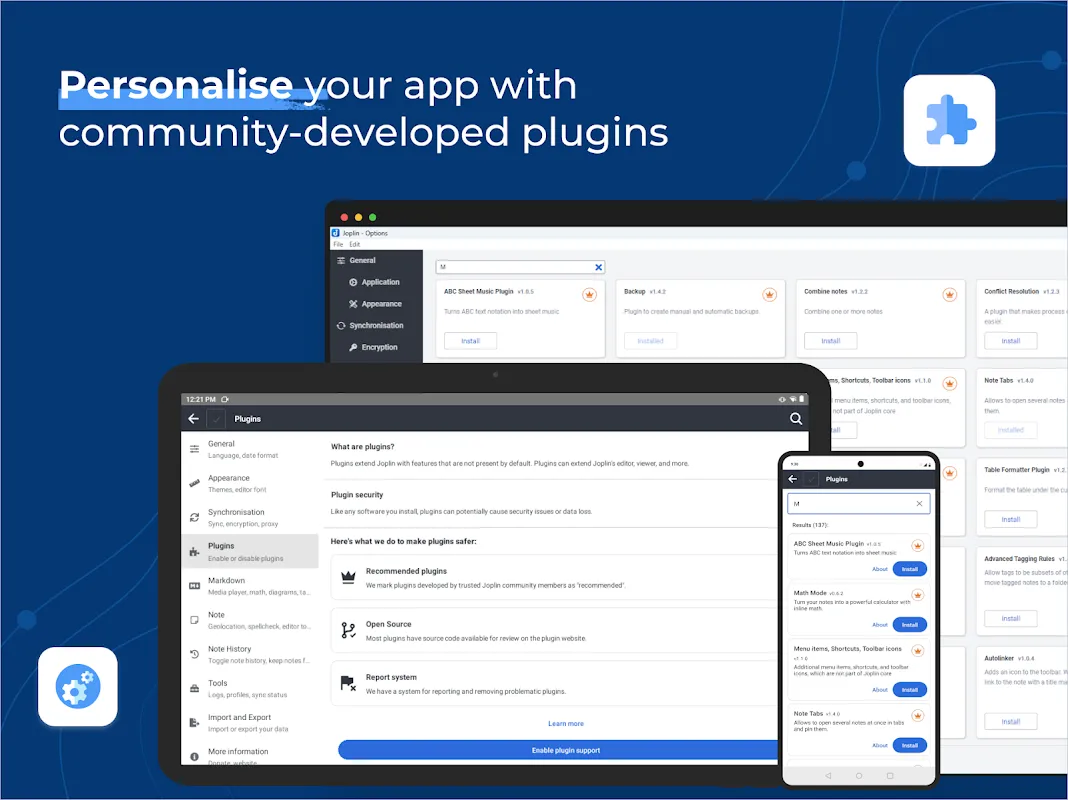 I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a
I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a -
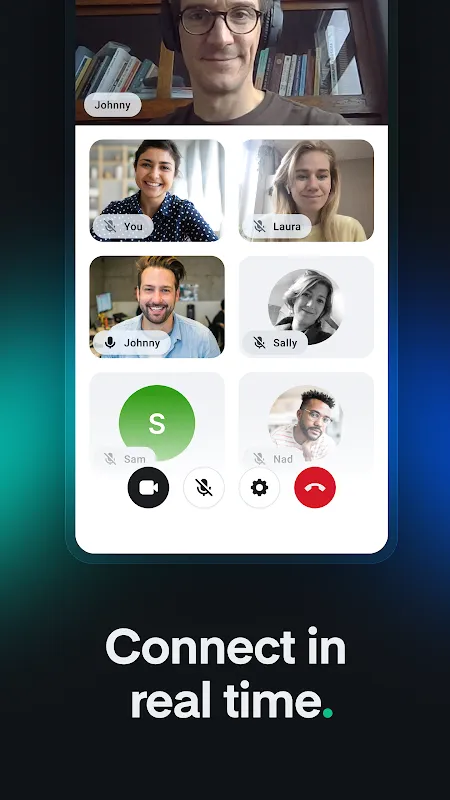 I remember the icy dread crawling up my spine when targeted ads started mocking me. There it was - the exact hiking boot I'd photographed for my dying father's bucket list trip, plastered across every platform after I'd shared it via mainstream messengers. That night, I tore through privacy forums like a madwoman, fingers trembling against my keyboard until dawn's pale light revealed Element X. The promise of true data sovereignty felt like finding an unbreakable vault in a world of cardboard lo
I remember the icy dread crawling up my spine when targeted ads started mocking me. There it was - the exact hiking boot I'd photographed for my dying father's bucket list trip, plastered across every platform after I'd shared it via mainstream messengers. That night, I tore through privacy forums like a madwoman, fingers trembling against my keyboard until dawn's pale light revealed Element X. The promise of true data sovereignty felt like finding an unbreakable vault in a world of cardboard lo -
 Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv.
Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv. -
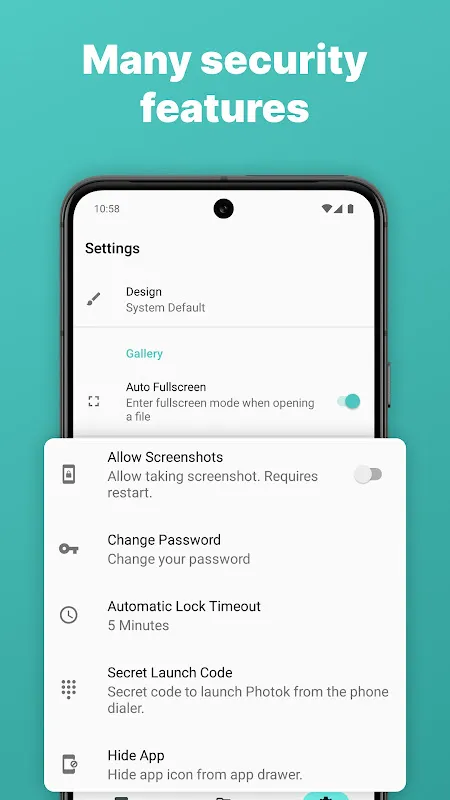 The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima
The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima -
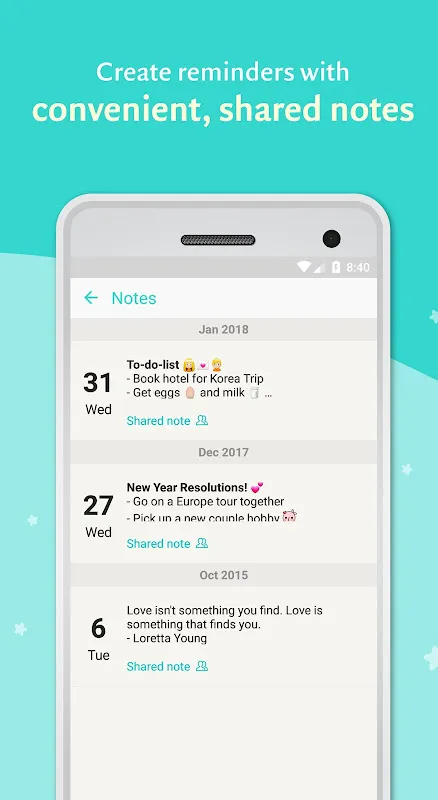 Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw
Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw -
 Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious
Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious -
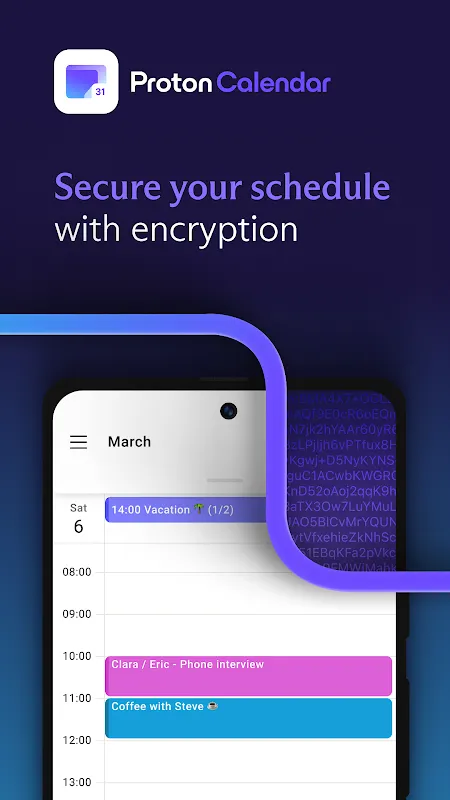 The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality.
The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality. -
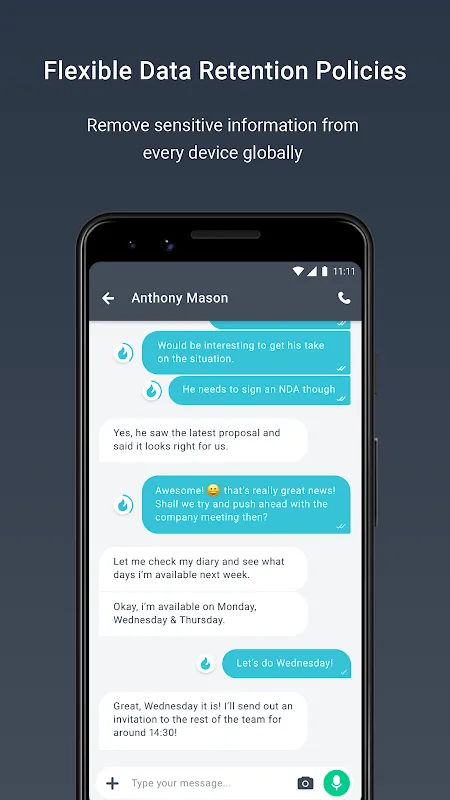 It was 3 AM, and the glow of my laptop screen was the only light in the silent office, casting shadows that seemed to whisper of impending doom. I had been chasing a phantom data breach for weeks, my nerves frayed like old rope, and every notification from our team's messaging app felt like a potential tripwire. As the head of cybersecurity for a mid-sized financial advisory firm, I was drowning in paranoia—until our IT director slid a new device across my desk with a single app installed: SaltI
It was 3 AM, and the glow of my laptop screen was the only light in the silent office, casting shadows that seemed to whisper of impending doom. I had been chasing a phantom data breach for weeks, my nerves frayed like old rope, and every notification from our team's messaging app felt like a potential tripwire. As the head of cybersecurity for a mid-sized financial advisory firm, I was drowning in paranoia—until our IT director slid a new device across my desk with a single app installed: SaltI -
 Midnight oil burned through my retinas as Slack's "message failed to send" error mocked our NDA-bound project. Panic tasted metallic when our client's prototype specs vanished during a Berlin-Tokyo handoff. That proprietary black box felt like collaborating through prison bars. Then our CTO muttered Rocket.Chat Experimental – three words that rewired our chaos.
Midnight oil burned through my retinas as Slack's "message failed to send" error mocked our NDA-bound project. Panic tasted metallic when our client's prototype specs vanished during a Berlin-Tokyo handoff. That proprietary black box felt like collaborating through prison bars. Then our CTO muttered Rocket.Chat Experimental – three words that rewired our chaos.
