encryption technology 2025-11-05T17:46:05Z
-
 The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore.
The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore. -
 Information Technology Act\xe2\x80\x98Information Technology Act 2000 (IT Act)\xe2\x80\x99 is the Best IT Act learning App with latest Amendments. It is a free and offline app providing detail Section-wise and Chapter-wise Legal Information of IT Act of India.The Information Technology Act, 2000 (al
Information Technology Act\xe2\x80\x98Information Technology Act 2000 (IT Act)\xe2\x80\x99 is the Best IT Act learning App with latest Amendments. It is a free and offline app providing detail Section-wise and Chapter-wise Legal Information of IT Act of India.The Information Technology Act, 2000 (al -
 World Wide TechnologyMany companies talk about business and technology outcomes. We do it. Want to see how?Whether you're connecting on the go with our engineers and application developers or bringing your team to the World Wide Technology Advanced Technology Center (ATC) for hands-on learning, the
World Wide TechnologyMany companies talk about business and technology outcomes. We do it. Want to see how?Whether you're connecting on the go with our engineers and application developers or bringing your team to the World Wide Technology Advanced Technology Center (ATC) for hands-on learning, the -
 AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil
AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil -
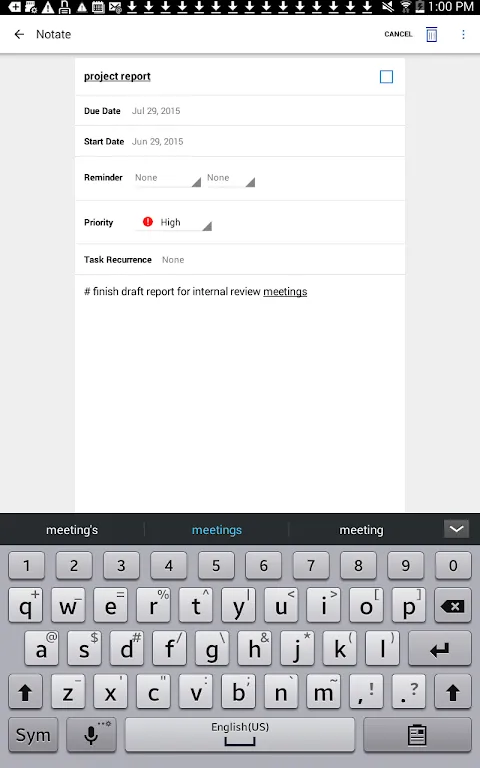 Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor
Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor -
 SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o
SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o -
 eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa
eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa -
 Rain lashed against the bus window as we crawled through Jakarta's flooded streets, each kilometer feeling like an eternity. My phone buzzed relentlessly - news alerts about collapsed bridges upstream, families stranded on rooftops, emergency crews overwhelmed. That familiar knot of helplessness tightened in my chest; the kind where you want to physically reach through the screen and pull people from rising waters. Fumbling with my e-wallet apps felt pointless - which organizations were actually
Rain lashed against the bus window as we crawled through Jakarta's flooded streets, each kilometer feeling like an eternity. My phone buzzed relentlessly - news alerts about collapsed bridges upstream, families stranded on rooftops, emergency crews overwhelmed. That familiar knot of helplessness tightened in my chest; the kind where you want to physically reach through the screen and pull people from rising waters. Fumbling with my e-wallet apps felt pointless - which organizations were actually -
 Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res
Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res -
 Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f
Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f -
 Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m
Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m -
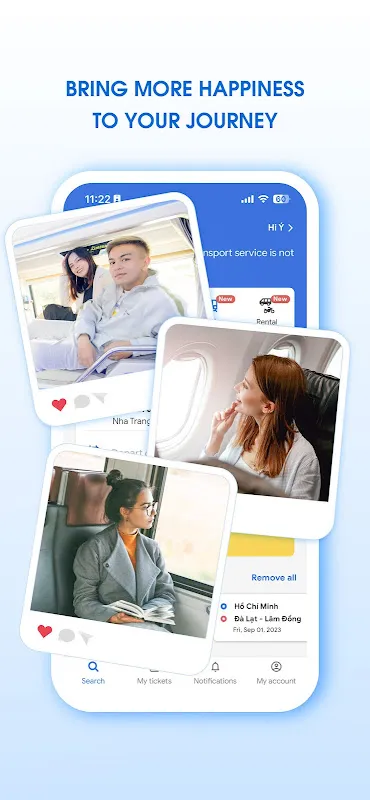 It all started with a frantic phone call from my mother. Her voice was shaky, laced with that particular brand of worry that only family emergencies can evoke. My grandfather had fallen ill back in Da Nang, and I needed to get there from Ho Chi Minh City—yesterday. Panic set in immediately. My mind raced through the usual options: flights were exorbitantly priced last-minute, trains were fully booked, and buses? The thought of navigating the chaotic bus stations, haggling with touts, and praying
It all started with a frantic phone call from my mother. Her voice was shaky, laced with that particular brand of worry that only family emergencies can evoke. My grandfather had fallen ill back in Da Nang, and I needed to get there from Ho Chi Minh City—yesterday. Panic set in immediately. My mind raced through the usual options: flights were exorbitantly priced last-minute, trains were fully booked, and buses? The thought of navigating the chaotic bus stations, haggling with touts, and praying -
 That metallic taste of panic flooded my mouth as I stared at the disaster unfolding in our operations center. Paperwork avalanched off desks, radios crackled with overlapping emergency calls, and Miguel's voice cracked through the chaos: "The downtown bank's HVAC just died during their investor meeting!" My fingers trembled while grabbing three different clipboards - maintenance logs, client history, technician dispatch - all hopelessly out of sync. That's when I remembered the app I'd sideloade
That metallic taste of panic flooded my mouth as I stared at the disaster unfolding in our operations center. Paperwork avalanched off desks, radios crackled with overlapping emergency calls, and Miguel's voice cracked through the chaos: "The downtown bank's HVAC just died during their investor meeting!" My fingers trembled while grabbing three different clipboards - maintenance logs, client history, technician dispatch - all hopelessly out of sync. That's when I remembered the app I'd sideloade -
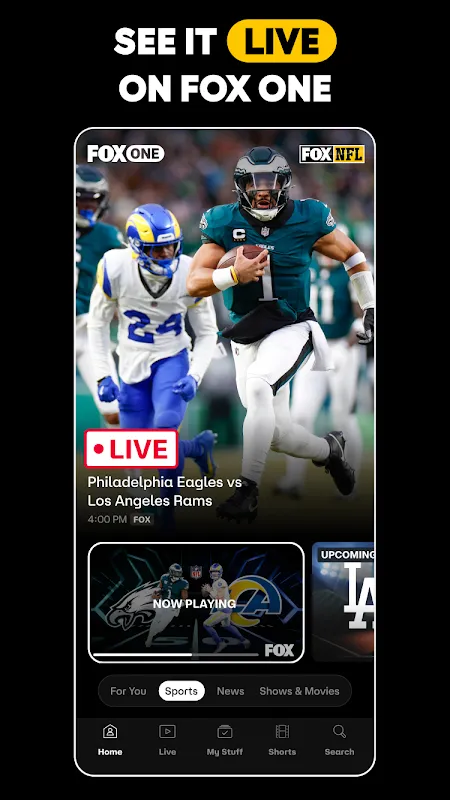 It was a typical Tuesday evening, the kind where exhaustion clings to your bones like damp clothing. I'd just wrapped up a grueling ten-hour workday, my eyes burning from staring at spreadsheets, and all I craved was to collapse on my couch and lose myself in something mindless. But tonight was different – tonight was game night. The city's basketball team was playing a crucial playoff match, and I'd promised myself I wouldn't miss a second. The problem? My usual method of wa
It was a typical Tuesday evening, the kind where exhaustion clings to your bones like damp clothing. I'd just wrapped up a grueling ten-hour workday, my eyes burning from staring at spreadsheets, and all I craved was to collapse on my couch and lose myself in something mindless. But tonight was different – tonight was game night. The city's basketball team was playing a crucial playoff match, and I'd promised myself I wouldn't miss a second. The problem? My usual method of wa -
 In the digital age, technology is influencing people's lives in unprecedented ways, and the realm of religious beliefs is no exception. Mymandir, an app developed by an Indian company, stands as a prime example of integrating modern technology with traditional Hindu practices. It offers a conven
In the digital age, technology is influencing people's lives in unprecedented ways, and the realm of religious beliefs is no exception. Mymandir, an app developed by an Indian company, stands as a prime example of integrating modern technology with traditional Hindu practices. It offers a conven -
 EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me
EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me -
 Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp
Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp -
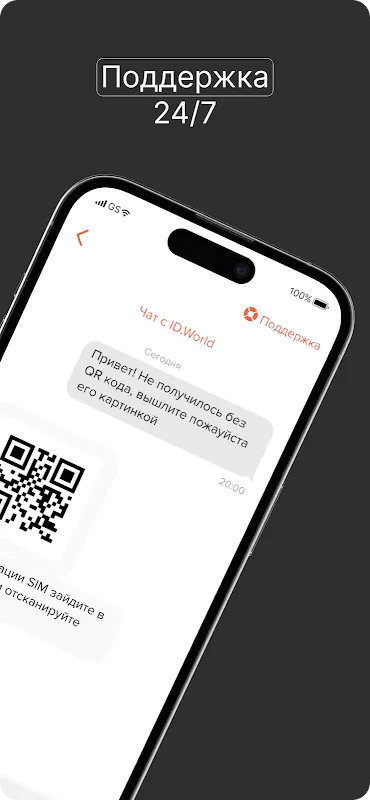 Monsoon mud sucked at my boots as I squinted through downpour-streaked car windows, cursing my profession for the hundredth time that month. There I was – stranded in some godforsaken village with three SIM registrations due by sunset and a leather-bound ledger already warping from humidity. My fingers trembled not from cold, but from raw panic: one smudged entry in that cursed notebook meant regulatory fines exceeding my weekly pay. That's when rainwater seeped through my satchel, triggering a
Monsoon mud sucked at my boots as I squinted through downpour-streaked car windows, cursing my profession for the hundredth time that month. There I was – stranded in some godforsaken village with three SIM registrations due by sunset and a leather-bound ledger already warping from humidity. My fingers trembled not from cold, but from raw panic: one smudged entry in that cursed notebook meant regulatory fines exceeding my weekly pay. That's when rainwater seeped through my satchel, triggering a -
 Rain lashed against my studio window like angry fists when the ransomware notification flashed. My entire freelance portfolio—years of architectural visualizations—locked behind that pulsing red skull icon. I remember the sour tang of panic rising in my throat as I frantically disconnected the NAS, fingers trembling against cold metal. That cursed email attachment from "Client_Revision.zip" had detonated silently while I'd been tweaking lighting gradients on a Barcelona penthouse render. For thr
Rain lashed against my studio window like angry fists when the ransomware notification flashed. My entire freelance portfolio—years of architectural visualizations—locked behind that pulsing red skull icon. I remember the sour tang of panic rising in my throat as I frantically disconnected the NAS, fingers trembling against cold metal. That cursed email attachment from "Client_Revision.zip" had detonated silently while I'd been tweaking lighting gradients on a Barcelona penthouse render. For thr -
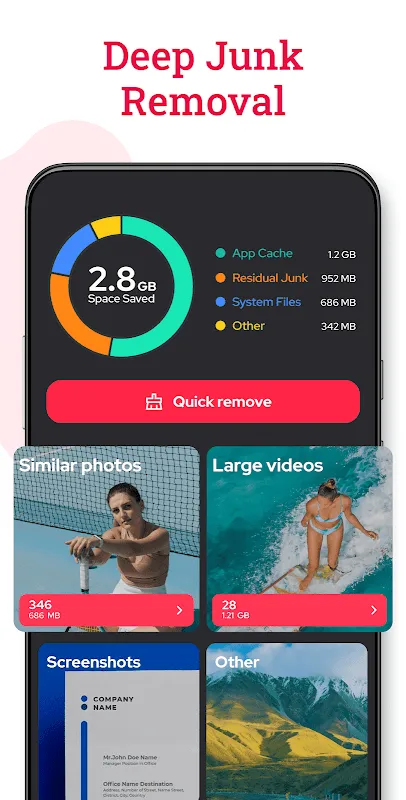 It was a typical Tuesday at the local café, the hum of espresso machines and chatter filling the air as I scrolled through my phone, reminiscing over vacation photos from Bali. Suddenly, a colleague leaned over my shoulder, his eyes darting across the screen. "Wow, those are some intimate shots!" he chuckled, and my heart plummeted. In that split second, I realized how vulnerable my digital life was—years of personal moments, from silly selfies to confidential work documents, all accessible with
It was a typical Tuesday at the local café, the hum of espresso machines and chatter filling the air as I scrolled through my phone, reminiscing over vacation photos from Bali. Suddenly, a colleague leaned over my shoulder, his eyes darting across the screen. "Wow, those are some intimate shots!" he chuckled, and my heart plummeted. In that split second, I realized how vulnerable my digital life was—years of personal moments, from silly selfies to confidential work documents, all accessible with