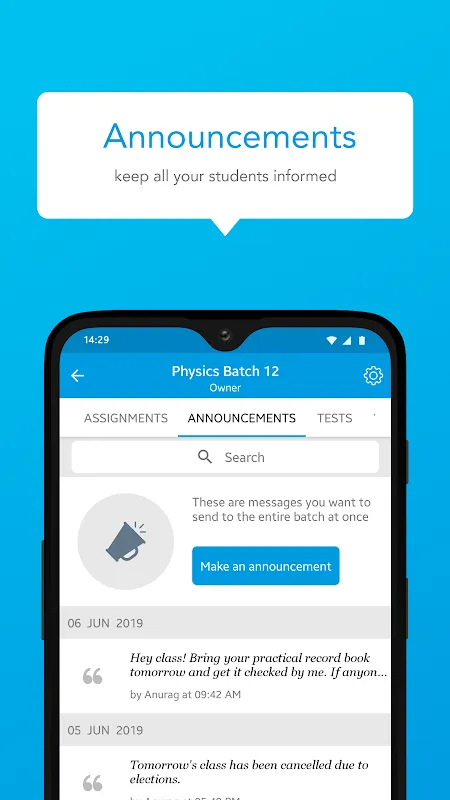
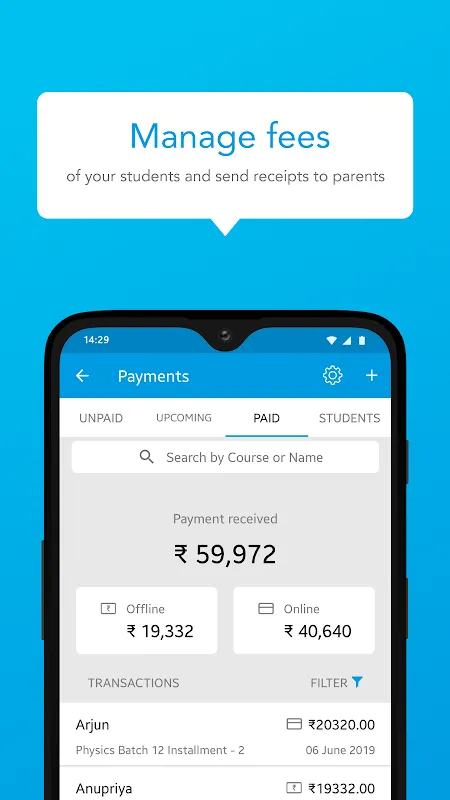
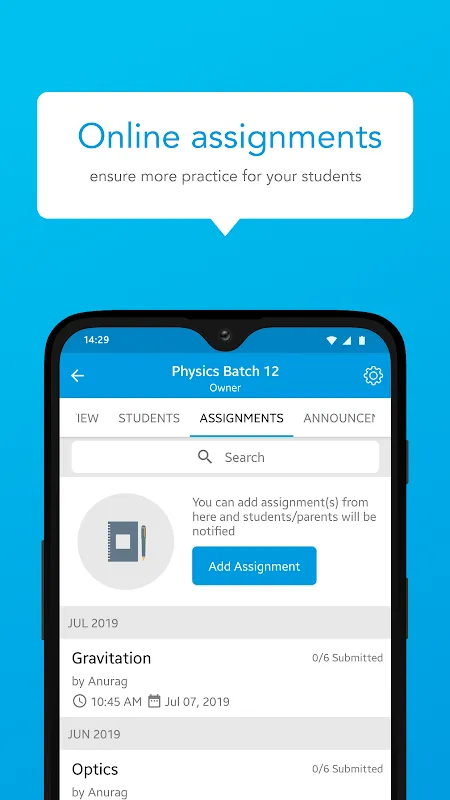
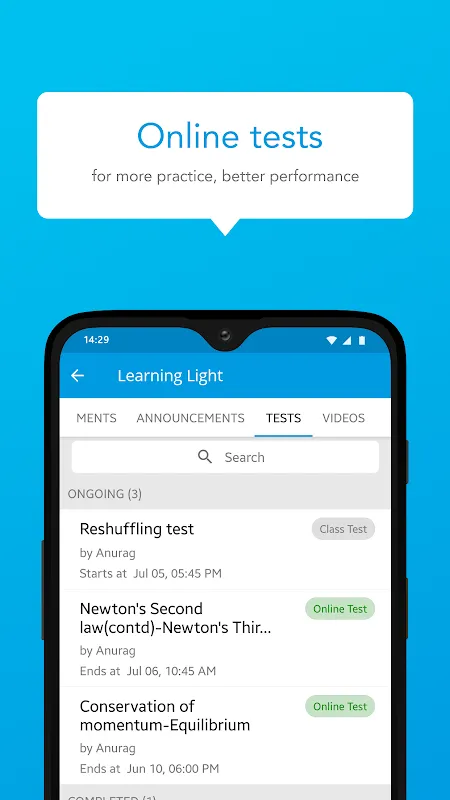
Desperate for cybersecurity skills after a phishing scam nearly compromised my company's client database, I discovered Secdroid during a frantic midnight search. That moment felt like finding a digital lifeline - suddenly, complex security concepts transformed into achievable skills through their brilliantly structured lessons. Secdroid isn't just another learning platform; it's my personal cyber-dojo where firewalls become friends and encryption feels like second nature.
Interactive Cyber Labs became my nightly ritual. I remember my hands trembling during my first simulated breach exercise at 2 AM - the adrenaline rush when I successfully isolated the attack vector mirrored real incident response. These virtual environments recreate corporate networks with startling accuracy, letting me practice containment protocols until muscle memory kicks in.
Threat Scenario Library saved me during last quarter's security audit. When our systems faced sophisticated ransomware patterns, I recognized the attack signature from Secdroid's case studies. That gut-punch realization - "I've seen this before!" - allowed me to implement countermeasures before the encryption spread, protecting terabytes of research data.
Community Challenges ignited my competitive spirit. During a weekend capture-the-flag event, I collaborated with a penetration tester from Berlin to crack cryptographic puzzles. The dopamine hit from solving challenges alongside global experts is unmatched - each notification of a solved module feels like earning a digital badge of honor.
Tuesday mornings now start with coffee and Micro-Learning Modules. While commuting, I digest bite-sized lessons on zero-trust architecture through vivid infographics. These condensed sessions stick better than university lectures - I often catch myself mentally auditing colleagues' access controls during meetings.
The Career Path Customization feature reshaped my professional trajectory. After inputting my sysadmin background, it recommended specializing in cloud security with tailored AWS labs. Three months later, I confidently negotiated a 30% salary increase by demonstrating precisely those skills during my performance review.
My only frustration surfaces during mobile learning - complex network diagrams sometimes require zooming on smaller screens. Yet this minor inconvenience vanishes when I recall how Secdroid's Offline Threat Libraries helped me diagnose an airport WiFi attack during a flight delay. That ability to transform dead time into defense training is priceless.
For cybersecurity professionals and anxious beginners alike, Secdroid delivers what textbooks cannot: the visceral confidence that comes from repeatedly outsmarting digital threats in safe simulations. It transforms abstract vulnerabilities into tangible victories - whether you're protecting family devices or enterprise networks.
Keywords: cybersecurity, ethical hacking, network defense, data protection, interactive learning