cybersecurity 2025-11-06T02:32:24Z
-
 Rain lashed against my apartment window as I hunched over a flickering laptop, fingers trembling over a half-finished network vulnerability report. That cursed Cisco certification mock exam had just gutted me - 58% flashing in crimson shame. My coffee tasted like burnt regrets. For weeks, I'd been grinding through pre-recorded lectures where monotone instructors droned about encryption protocols like they were reciting obituaries. The isolation was physical; shoulders knotted, eyes sandpapered f
Rain lashed against my apartment window as I hunched over a flickering laptop, fingers trembling over a half-finished network vulnerability report. That cursed Cisco certification mock exam had just gutted me - 58% flashing in crimson shame. My coffee tasted like burnt regrets. For weeks, I'd been grinding through pre-recorded lectures where monotone instructors droned about encryption protocols like they were reciting obituaries. The isolation was physical; shoulders knotted, eyes sandpapered f -
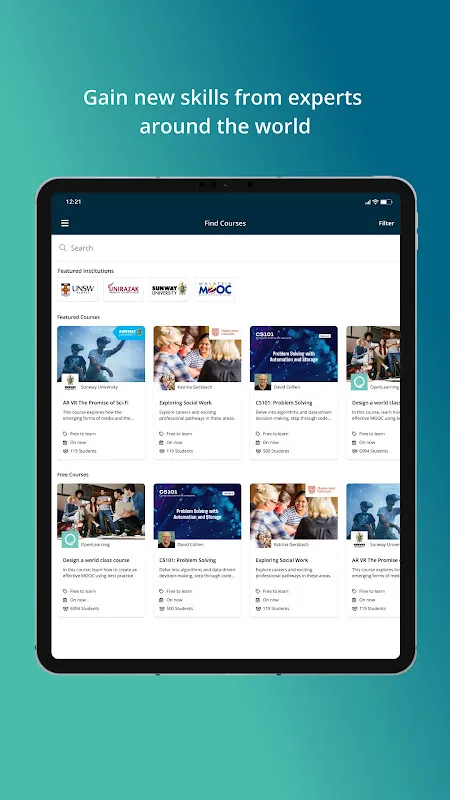
 Pocket Prep IT & CybersecurityUnlock thousands of IT & Cybersecurity certification exam practice questions and mock exams for the CompTIA Security+, ISC2 CISSP, Cisco CCNA, CompTIA A+, CompTIA Network+, and more with Pocket Prep, the largest provider of mobile test prep for professional certificatio
Pocket Prep IT & CybersecurityUnlock thousands of IT & Cybersecurity certification exam practice questions and mock exams for the CompTIA Security+, ISC2 CISSP, Cisco CCNA, CompTIA A+, CompTIA Network+, and more with Pocket Prep, the largest provider of mobile test prep for professional certificatio -
 NOMA iQWelcome to NOMA iQ, the smart home solution that is simple to use and with DataGuardTM cybersecurity you can trust.CONTROL YOUR NOMA iQ PRODUCTS ALL IN ONE APPThe NOMA iQ app is quick and easy to set up and incorporates smart prompts for guided learning. Added depth of control is also available for more advanced users. This app was designed to conveniently allow its users to light, power, and maximize the comfort of their home all in one app for seamless control of your home.With NOMA iQ'
NOMA iQWelcome to NOMA iQ, the smart home solution that is simple to use and with DataGuardTM cybersecurity you can trust.CONTROL YOUR NOMA iQ PRODUCTS ALL IN ONE APPThe NOMA iQ app is quick and easy to set up and incorporates smart prompts for guided learning. Added depth of control is also available for more advanced users. This app was designed to conveniently allow its users to light, power, and maximize the comfort of their home all in one app for seamless control of your home.With NOMA iQ' -
 Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we
Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we -
 Black Hat EventsBlack Hat Events are the most technical and relevant information security conferences and trainings in the world. Providing attendees with the very latest in information security research, development, and trends, Black Hat Events bring the global InfoSec community together to share ideas, learn from experts, and network with peers, practitioners, researchers, and solutions providers from around the globe. The Black Hat Events portfolio includes all Black Hat global events, as we
Black Hat EventsBlack Hat Events are the most technical and relevant information security conferences and trainings in the world. Providing attendees with the very latest in information security research, development, and trends, Black Hat Events bring the global InfoSec community together to share ideas, learn from experts, and network with peers, practitioners, researchers, and solutions providers from around the globe. The Black Hat Events portfolio includes all Black Hat global events, as we -
 The acrid smell of burnt coffee filled my home office as panic tightened its grip around my throat. My fingers trembled over the keyboard, watching helplessly as cryptic error messages multiplied across three different screens. My son's gaming rig flashed crimson warnings about unauthorized bitcoin miners while my personal laptop displayed ransomware countdown timers in mocking neon green. Each device screamed its own security emergency in a dissonant chorus of digital despair, turning my mornin
The acrid smell of burnt coffee filled my home office as panic tightened its grip around my throat. My fingers trembled over the keyboard, watching helplessly as cryptic error messages multiplied across three different screens. My son's gaming rig flashed crimson warnings about unauthorized bitcoin miners while my personal laptop displayed ransomware countdown timers in mocking neon green. Each device screamed its own security emergency in a dissonant chorus of digital despair, turning my mornin -
 Rain lashed against my apartment windows like a thousand tiny hackers probing for vulnerabilities. I'd just spent eight hours reviewing firewall logs – real-world cybersecurity that felt less like digital warfare and more like watching paint dry on server racks. My coffee had gone cold three times, each reheating a sad ritual mirroring the monotony of threat alerts blinking across dual monitors. That's when the notification appeared: "Your underground botnet awaits deployment." Not on my work da
Rain lashed against my apartment windows like a thousand tiny hackers probing for vulnerabilities. I'd just spent eight hours reviewing firewall logs – real-world cybersecurity that felt less like digital warfare and more like watching paint dry on server racks. My coffee had gone cold three times, each reheating a sad ritual mirroring the monotony of threat alerts blinking across dual monitors. That's when the notification appeared: "Your underground botnet awaits deployment." Not on my work da -
 SecureLogSecureLog continuously analyzes your online activities and sends you instant notifications whenever there is an important update. With its advanced graphing features and user-friendly interface, you can easily monitor your digital presence and receive detailed reports. Stay informed about every significant change with real-time alerts, giving you full control over your online activities. Managing your online world has never been easier or safer with SecureLog!Privacy Policy: https://sit
SecureLogSecureLog continuously analyzes your online activities and sends you instant notifications whenever there is an important update. With its advanced graphing features and user-friendly interface, you can easily monitor your digital presence and receive detailed reports. Stay informed about every significant change with real-time alerts, giving you full control over your online activities. Managing your online world has never been easier or safer with SecureLog!Privacy Policy: https://sit -
 Simplilearn: Online LearningWith more than 400 certificate courses taught by around 2000+ expert trainers, Simplilearn is a leading online learning platform that provides professional certification courses in various fields such as Artificial Intelligence, Digital Marketing, Cloud Computing, Project
Simplilearn: Online LearningWith more than 400 certificate courses taught by around 2000+ expert trainers, Simplilearn is a leading online learning platform that provides professional certification courses in various fields such as Artificial Intelligence, Digital Marketing, Cloud Computing, Project -
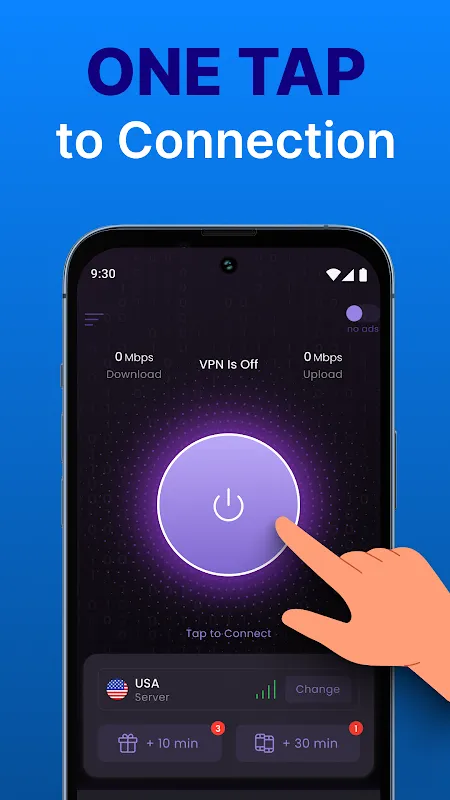 Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo
Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo -
 NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/
NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/ -
 TunnelBear VPNTunnelBear VPN. Privacy. For everyone. TunnelBear is an easy-to-use VPN app that helps you browse privately and securely from anywhere. With just one tap, TunnelBear changes your IP address and encrypts your browsing data, protecting it from online threats. It\xe2\x80\x99s so simple, e
TunnelBear VPNTunnelBear VPN. Privacy. For everyone. TunnelBear is an easy-to-use VPN app that helps you browse privately and securely from anywhere. With just one tap, TunnelBear changes your IP address and encrypts your browsing data, protecting it from online threats. It\xe2\x80\x99s so simple, e -
 I still remember the chill that ran down my spine when I opened my email that Tuesday morning. There it was—a confirmation for a high-end laptop purchase from a retailer I’d never heard of, charged to my credit card. My heart hammered against my ribs, and my fingers trembled as I fumbled to call my bank. The representative’s calm voice did little to soothe the panic bubbling inside me. It was my first brush with digital fraud, and it left me feeling exposed, as if someone had picked the lock to
I still remember the chill that ran down my spine when I opened my email that Tuesday morning. There it was—a confirmation for a high-end laptop purchase from a retailer I’d never heard of, charged to my credit card. My heart hammered against my ribs, and my fingers trembled as I fumbled to call my bank. The representative’s calm voice did little to soothe the panic bubbling inside me. It was my first brush with digital fraud, and it left me feeling exposed, as if someone had picked the lock to -
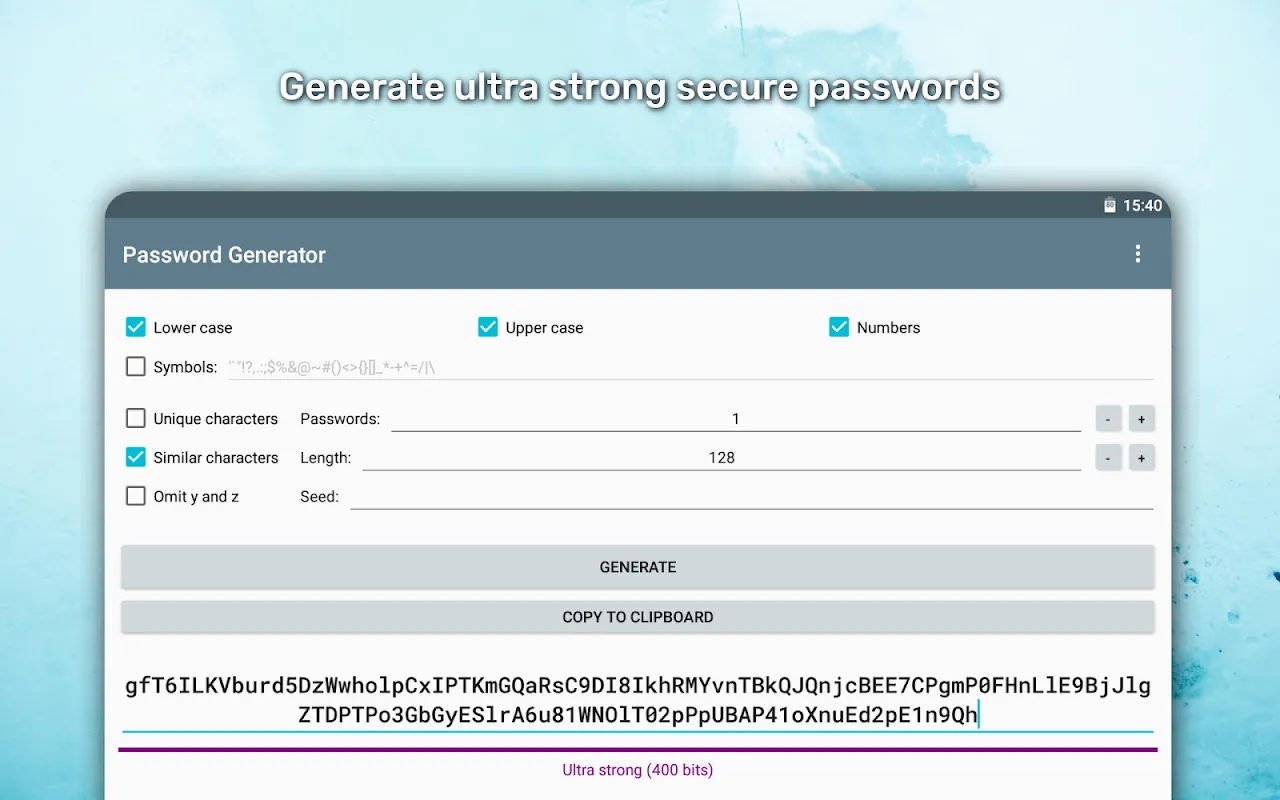 Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu
Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu -
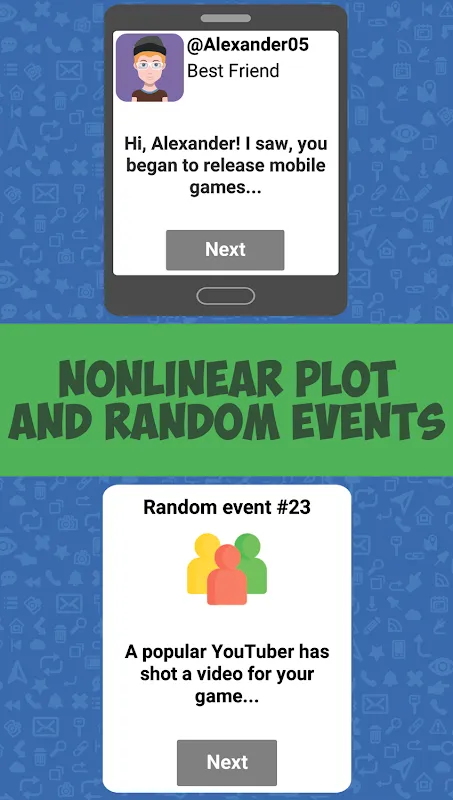
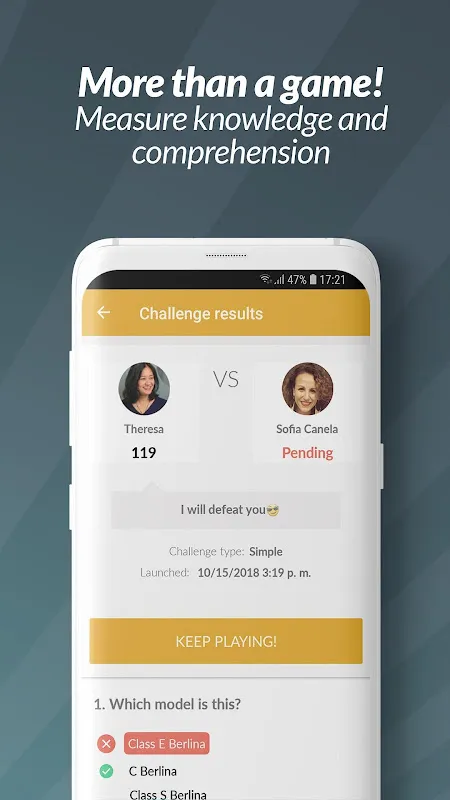 The fluorescent lights hummed overhead as I slumped in another soul-crushing training session, watching colleagues covertly check phones beneath the table. Our compliance officer droned through GDPR regulations like a metronome set to funeral tempo. Then the HR director burst in waving her tablet - "We're trying something new today!" My eyes rolled so hard I saw my own brain. Gamification? Please. I'd suffered through enough cringe-worthy corporate "fun" to know this would be another patronizing
The fluorescent lights hummed overhead as I slumped in another soul-crushing training session, watching colleagues covertly check phones beneath the table. Our compliance officer droned through GDPR regulations like a metronome set to funeral tempo. Then the HR director burst in waving her tablet - "We're trying something new today!" My eyes rolled so hard I saw my own brain. Gamification? Please. I'd suffered through enough cringe-worthy corporate "fun" to know this would be another patronizing -
 TrackIP - Track any IP AddressTrack IP is a free and user-friendly tool that allows you to search and track any IP address in the world. With our easy-to-use app, you can quickly and accurately locate any IP address and get detailed information about its location, including the city, country, region, and ZIP code. Whether you're a professional network administrator or a casual internet user, Track IP is the perfect tool for finding and tracking IP addresses with ease and speed.Features :Copy, Sh
TrackIP - Track any IP AddressTrack IP is a free and user-friendly tool that allows you to search and track any IP address in the world. With our easy-to-use app, you can quickly and accurately locate any IP address and get detailed information about its location, including the city, country, region, and ZIP code. Whether you're a professional network administrator or a casual internet user, Track IP is the perfect tool for finding and tracking IP addresses with ease and speed.Features :Copy, Sh -
 Safehouse VPN & MobileSecuritySafehouse is a mobile application designed to enhance online privacy and security for users. This app, formerly known as Bodyguard Mobile Security, offers a variety of features that help protect personal data and ensure a safe browsing experience. Safehouse is available
Safehouse VPN & MobileSecuritySafehouse is a mobile application designed to enhance online privacy and security for users. This app, formerly known as Bodyguard Mobile Security, offers a variety of features that help protect personal data and ensure a safe browsing experience. Safehouse is available -
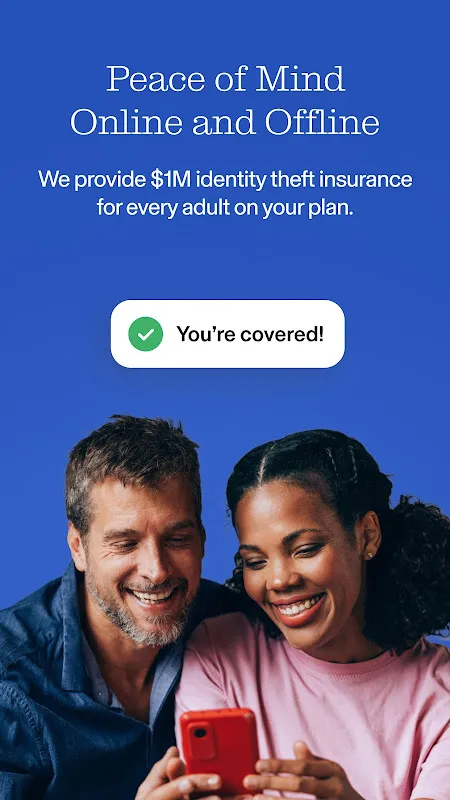
 CFC ResponseThe CFC incident response app gives you the ability to instantly notify our incident response team of a cyber event. The app includes a tailored threat intelligence feed, direct access to our world-class cyber incident response team via the 'Ask the expert' functionality, and a number of tools to help you protect your business against cyber attacks.Enhanced features include:\xc2\xb7 Fast and detailed instant reporting of live cyber incidents to the cyber claims team;\xc2\xb7 Bespoke
CFC ResponseThe CFC incident response app gives you the ability to instantly notify our incident response team of a cyber event. The app includes a tailored threat intelligence feed, direct access to our world-class cyber incident response team via the 'Ask the expert' functionality, and a number of tools to help you protect your business against cyber attacks.Enhanced features include:\xc2\xb7 Fast and detailed instant reporting of live cyber incidents to the cyber claims team;\xc2\xb7 Bespoke

