encryption protocols 2025-10-25T05:22:25Z
-
 The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore.
The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore. -
 Cold fluorescent lights hummed above the empty nurses' station as I pressed my forehead against the glass partition. Maria's chart felt like lead in my hands - recurrent cervical carcinoma with bizarre metastasis patterns that defied textbook presentations. Down the hall, her husband slept curled in a vinyl chair while her vitals danced dangerously on the monitor. Every resident's nightmare: being the lone physician on night shift when standard protocols crumble. My pager vibrated - lab results
Cold fluorescent lights hummed above the empty nurses' station as I pressed my forehead against the glass partition. Maria's chart felt like lead in my hands - recurrent cervical carcinoma with bizarre metastasis patterns that defied textbook presentations. Down the hall, her husband slept curled in a vinyl chair while her vitals danced dangerously on the monitor. Every resident's nightmare: being the lone physician on night shift when standard protocols crumble. My pager vibrated - lab results -
 AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil
AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil -
 Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor
Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor -
 SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o
SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o -
 eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa
eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa -
 Rain lashed against the conference room windows as my phone screamed with an unfamiliar alarm - a pulsing crimson light from the OBLO hub app I'd half-forgotten after setup. That primal sound sliced through my jetlag fog. Flood detected basement east zone. My stomach dropped. Three thousand miles away, pipes were bursting inside walls I couldn't touch.
Rain lashed against the conference room windows as my phone screamed with an unfamiliar alarm - a pulsing crimson light from the OBLO hub app I'd half-forgotten after setup. That primal sound sliced through my jetlag fog. Flood detected basement east zone. My stomach dropped. Three thousand miles away, pipes were bursting inside walls I couldn't touch. -
 Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res
Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res -
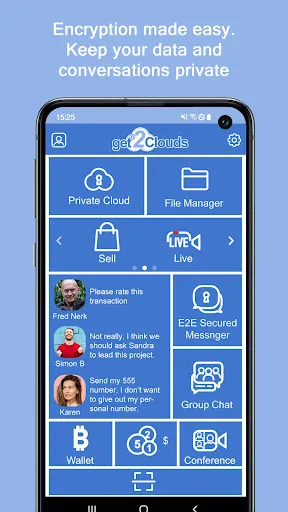 Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f
Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f -
 Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m
Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m -
 V2BoxV2box - V2ray Client is a VPN Internet network proxy , Supports multiple proxy protocols, such as Shadowsocks, V2ray, Vmess, vless, Trojan, SSH, Hysteria, Ping TunnelFeatures:- Support for adding custom servers proxy (Shadowsocks, v2ray, trojan,vless,vmess)- Support Reality (xray)- Support Hysteria / Hysteria2- Support Ping Tunnel- Support vless vision- Support utls- Support SSH- Support V2ray / Xray Subscription Link- Support JSON V2ray- Multiple encryption protocol support, AES-128-GCM, A
V2BoxV2box - V2ray Client is a VPN Internet network proxy , Supports multiple proxy protocols, such as Shadowsocks, V2ray, Vmess, vless, Trojan, SSH, Hysteria, Ping TunnelFeatures:- Support for adding custom servers proxy (Shadowsocks, v2ray, trojan,vless,vmess)- Support Reality (xray)- Support Hysteria / Hysteria2- Support Ping Tunnel- Support vless vision- Support utls- Support SSH- Support V2ray / Xray Subscription Link- Support JSON V2ray- Multiple encryption protocol support, AES-128-GCM, A -
 Rain lashed against the coffee shop window as I hunched over my laptop, the acidic smell of burnt espresso mixing with my rising panic. Deadline in 30 minutes, and here I was trapped - needing to email client contracts through this sketchy public WiFi that just flashed "UNSECURED NETWORK" in blood-red letters. My thumb hovered over the send button like a detonator, imagining hackers intercepting years of confidential negotiations. That's when I remembered the shield in my pocket: TrymeVPN.
Rain lashed against the coffee shop window as I hunched over my laptop, the acidic smell of burnt espresso mixing with my rising panic. Deadline in 30 minutes, and here I was trapped - needing to email client contracts through this sketchy public WiFi that just flashed "UNSECURED NETWORK" in blood-red letters. My thumb hovered over the send button like a detonator, imagining hackers intercepting years of confidential negotiations. That's when I remembered the shield in my pocket: TrymeVPN. -
 My Tunnel ProxyExperience the pinnacle of online security and privacy with "My Tunnel Proxy," your all-in-one VPN app designed to safeguard your digital life. With support for OpenVPN, SSH, and UDP protocols, we've crafted the perfect solution for users seeking top-tier protection without compromising on speed or ease of use.\xf0\x9f\x9b\xa1\xef\xb8\x8f Unparalleled SecurityMy Tunnel Proxy employs cutting-edge encryption techniques to shield your internet traffic from prying eyes. Whether you're
My Tunnel ProxyExperience the pinnacle of online security and privacy with "My Tunnel Proxy," your all-in-one VPN app designed to safeguard your digital life. With support for OpenVPN, SSH, and UDP protocols, we've crafted the perfect solution for users seeking top-tier protection without compromising on speed or ease of use.\xf0\x9f\x9b\xa1\xef\xb8\x8f Unparalleled SecurityMy Tunnel Proxy employs cutting-edge encryption techniques to shield your internet traffic from prying eyes. Whether you're -
 Rain lashed against my cabin windows as I frantically swiped between four different messaging apps, each blinking with urgent notifications from scattered family members. Grandma's flight was delayed, my sister's car broke down in a thunderstorm, and Dad's health alerts were pinging simultaneously across my phone, tablet, and laptop. That chaotic Tuesday night last July, I realized our fragmented communication was more than inconvenient—it was dangerous. My fingers trembled trying to coordinate
Rain lashed against my cabin windows as I frantically swiped between four different messaging apps, each blinking with urgent notifications from scattered family members. Grandma's flight was delayed, my sister's car broke down in a thunderstorm, and Dad's health alerts were pinging simultaneously across my phone, tablet, and laptop. That chaotic Tuesday night last July, I realized our fragmented communication was more than inconvenient—it was dangerous. My fingers trembled trying to coordinate -
 XY VPN - Security Proxy VPNXY VPN is a stable VPN! Stable and worldwide internet privacy and security VPN app for all Android users.Features:\xe2\x98\x86 Choose an application that uses VPN (requires Android 5.0+)\xe2\x98\x86 Smart selection server\xe2\x98\x86 No registration or configuration is required\xe2\x98\x86 No other permissions requiredWhy trust and choose XY VPN?1. Provide safe protection for privacy and security- Military-grade AES 128-bit encryption to secure WiFi hotspots.- IPsec p
XY VPN - Security Proxy VPNXY VPN is a stable VPN! Stable and worldwide internet privacy and security VPN app for all Android users.Features:\xe2\x98\x86 Choose an application that uses VPN (requires Android 5.0+)\xe2\x98\x86 Smart selection server\xe2\x98\x86 No registration or configuration is required\xe2\x98\x86 No other permissions requiredWhy trust and choose XY VPN?1. Provide safe protection for privacy and security- Military-grade AES 128-bit encryption to secure WiFi hotspots.- IPsec p -
 I remember the clammy dread creeping up my neck in that Barcelona café last summer. My fingers hovered over the login button for my investment portfolio as the public Wi-Fi icon mocked me with its false promise of convenience. As a freelance cybersecurity consultant, I knew better than anyone how exposed I was – every keystroke potentially laid bare to digital pickpockets. That’s when I fumbled for VPN Proxy Master, my thumb jabbing the screen like a panic button. The instant green shield icon f
I remember the clammy dread creeping up my neck in that Barcelona café last summer. My fingers hovered over the login button for my investment portfolio as the public Wi-Fi icon mocked me with its false promise of convenience. As a freelance cybersecurity consultant, I knew better than anyone how exposed I was – every keystroke potentially laid bare to digital pickpockets. That’s when I fumbled for VPN Proxy Master, my thumb jabbing the screen like a panic button. The instant green shield icon f -
 Rain lashed against the coffee shop windows as I frantically tapped my credit card details into the payment portal. That sketchy public Wi-Fi suddenly felt like broadcasting my financial life to every hacker in a five-block radius. Sweat prickled my neck when the page froze mid-transaction - that heart-stopping moment when you realize you're digitally naked in a crowded room. I'd heard about VPNs, but always dismissed them as sluggish privacy blankets for paranoids.
Rain lashed against the coffee shop windows as I frantically tapped my credit card details into the payment portal. That sketchy public Wi-Fi suddenly felt like broadcasting my financial life to every hacker in a five-block radius. Sweat prickled my neck when the page froze mid-transaction - that heart-stopping moment when you realize you're digitally naked in a crowded room. I'd heard about VPNs, but always dismissed them as sluggish privacy blankets for paranoids. -
 Rain lashed against the café window in Istanbul as my fingers turned icy around the phone. Deadline in 90 minutes, and my client's secure portal laughed at me with mocking red letters: ACCESS DENIED. Turkish firewalls had declared war on my journalism assignment. Sweat trickled down my collar despite the AC's hum. That's when I stabbed the crimson circle on my screen – military-grade encryption flaring to life like a shield. Suddenly, London servers blinked open, my fingers flying across keyboar
Rain lashed against the café window in Istanbul as my fingers turned icy around the phone. Deadline in 90 minutes, and my client's secure portal laughed at me with mocking red letters: ACCESS DENIED. Turkish firewalls had declared war on my journalism assignment. Sweat trickled down my collar despite the AC's hum. That's when I stabbed the crimson circle on my screen – military-grade encryption flaring to life like a shield. Suddenly, London servers blinked open, my fingers flying across keyboar -
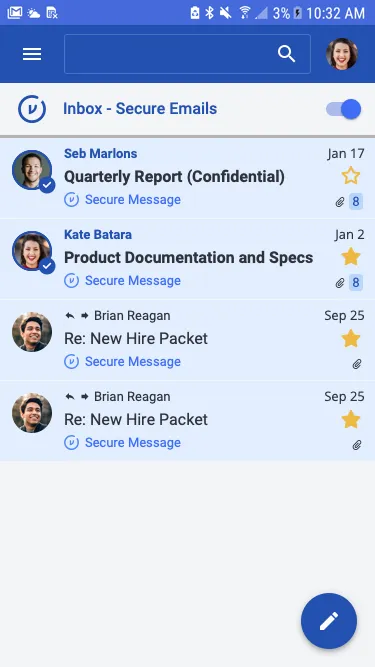 That third flat white was buzzing through my veins when I spotted the attachment icon blinking on my phone - right before hitting send on a proposal containing acquisition targets. Public coffee shop Wi-Fi suddenly felt like broadcasting on Times Square billboards. My thumb hovered over the screen, slick with cold sweat as I imagined competitors intercepting those unencrypted figures. Every notification chime from neighboring laptops sounded like a data breach alarm.
That third flat white was buzzing through my veins when I spotted the attachment icon blinking on my phone - right before hitting send on a proposal containing acquisition targets. Public coffee shop Wi-Fi suddenly felt like broadcasting on Times Square billboards. My thumb hovered over the screen, slick with cold sweat as I imagined competitors intercepting those unencrypted figures. Every notification chime from neighboring laptops sounded like a data breach alarm. -
 Rain lashed against the café window as I hunched over my laptop in Kreuzberg, the sour taste of panic rising in my throat. My German SIM card had died mid-negotiation, leaving me stranded with public Wi-Fi while finalizing a contract that could make or break my freelance career. Every exposed packet on this network felt like broadcasting my financial details to hackers. Then I remembered the shield I'd installed weeks prior - that unassuming app with the fingerprint logo. One tap ignited a crypt
Rain lashed against the café window as I hunched over my laptop in Kreuzberg, the sour taste of panic rising in my throat. My German SIM card had died mid-negotiation, leaving me stranded with public Wi-Fi while finalizing a contract that could make or break my freelance career. Every exposed packet on this network felt like broadcasting my financial details to hackers. Then I remembered the shield I'd installed weeks prior - that unassuming app with the fingerprint logo. One tap ignited a crypt