encryption protocols 2025-10-25T16:32:59Z
-
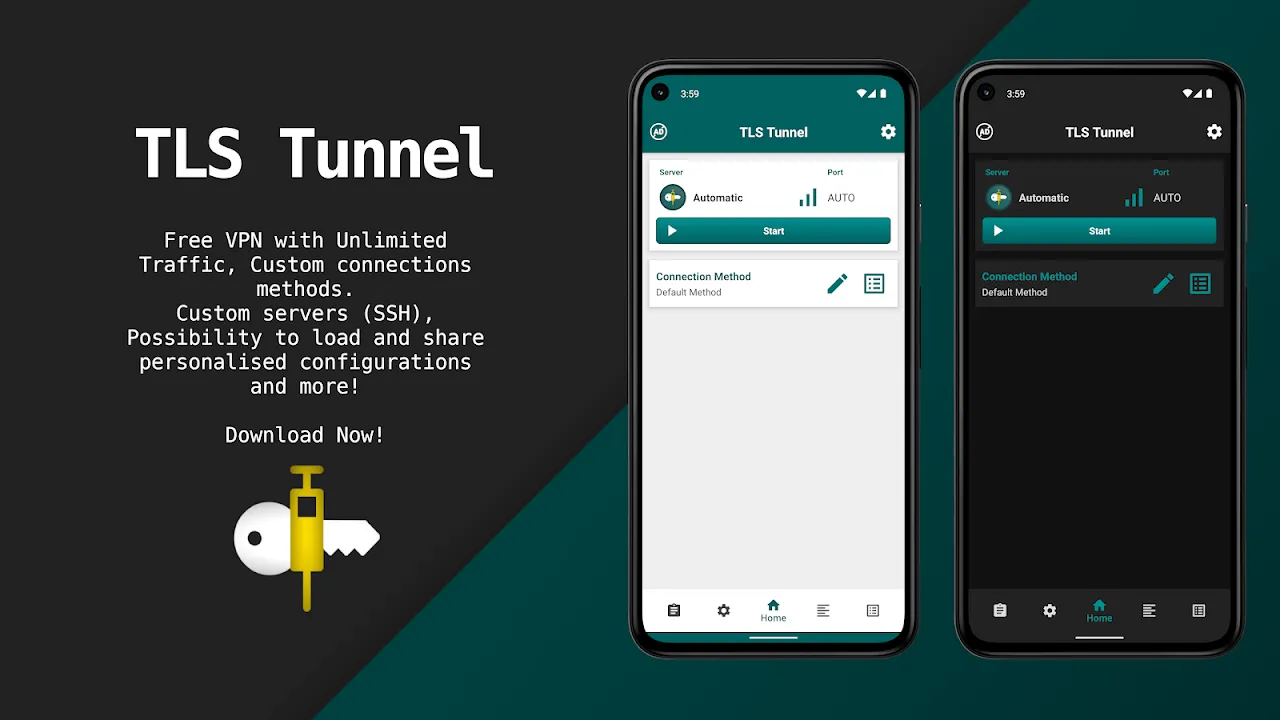 Rain lashed against the hotel window like angry fingertips tapping glass as I hunched over my laptop in Budapest, my knuckles white around a cold espresso cup. Government firewalls had just slaughtered my access to whistleblower documents – twenty hours of investigative work evaporating before deadline. That's when I remembered the neon-green shield icon buried in my apps folder. One tap on TLS Tunnel's military-grade encryption and suddenly, the digital barricades dissolved like sugar in hot wa
Rain lashed against the hotel window like angry fingertips tapping glass as I hunched over my laptop in Budapest, my knuckles white around a cold espresso cup. Government firewalls had just slaughtered my access to whistleblower documents – twenty hours of investigative work evaporating before deadline. That's when I remembered the neon-green shield icon buried in my apps folder. One tap on TLS Tunnel's military-grade encryption and suddenly, the digital barricades dissolved like sugar in hot wa -
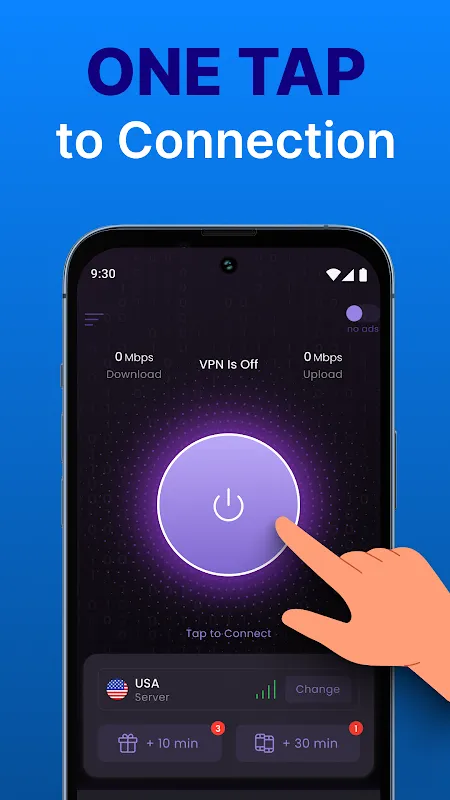 Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo
Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo -
 Rain lashed against the science building windows like marbles thrown by an angry god when the ammonia alarm shrieked. My palms instantly slicked with cold sweat as I sprinted down corridor B - not toward the chemical spill, but toward my office where one device held salvation. Three months prior, I'd mocked our IT director for insisting we adopt Stay Informed's encrypted broadcast system. Now, fumbling with keys while acrid fumes stung my nostrils, that skepticism felt like arrogance carved in i
Rain lashed against the science building windows like marbles thrown by an angry god when the ammonia alarm shrieked. My palms instantly slicked with cold sweat as I sprinted down corridor B - not toward the chemical spill, but toward my office where one device held salvation. Three months prior, I'd mocked our IT director for insisting we adopt Stay Informed's encrypted broadcast system. Now, fumbling with keys while acrid fumes stung my nostrils, that skepticism felt like arrogance carved in i -
 Turbo VPN - Secure VPN ProxyTurbo VPN is a free and unlimited VPN proxy application designed to provide users with a secure and private internet experience. This app allows users to access various web and app resources with ease while ensuring anonymity and security during online activities. Turbo V
Turbo VPN - Secure VPN ProxyTurbo VPN is a free and unlimited VPN proxy application designed to provide users with a secure and private internet experience. This app allows users to access various web and app resources with ease while ensuring anonymity and security during online activities. Turbo V -
 EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me
EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me -
 Rain lashed against the coffee shop window as I hunched over my laptop, desperation souring my third espresso. The archival footage from Belgrade's National Museum - crucial for my documentary on Balkan folk traditions - remained locked behind cruel geo-fences. Every refresh mocked me with that icy "content unavailable in your region" notification, each pixelated denial tightening my shoulders into knots. My fingers trembled not from caffeine but from the helpless rage of intellectual captivity,
Rain lashed against the coffee shop window as I hunched over my laptop, desperation souring my third espresso. The archival footage from Belgrade's National Museum - crucial for my documentary on Balkan folk traditions - remained locked behind cruel geo-fences. Every refresh mocked me with that icy "content unavailable in your region" notification, each pixelated denial tightening my shoulders into knots. My fingers trembled not from caffeine but from the helpless rage of intellectual captivity, -
 Rain lashed against the café window like prison bars as my fingers trembled over the keyboard. Three hours. That's how long I'd been trapped in this digital purgatory, my investigative report on pharmaceutical corruption frozen at 98% upload. Outside, state-sponsored internet filters choked the city's bandwidth, turning what should've been a 30-second transfer into a soul-crushing limbo. Each failed attempt felt like a boot heel grinding my press credentials into dust. That's when I remembered t
Rain lashed against the café window like prison bars as my fingers trembled over the keyboard. Three hours. That's how long I'd been trapped in this digital purgatory, my investigative report on pharmaceutical corruption frozen at 98% upload. Outside, state-sponsored internet filters choked the city's bandwidth, turning what should've been a 30-second transfer into a soul-crushing limbo. Each failed attempt felt like a boot heel grinding my press credentials into dust. That's when I remembered t -
 Psiphon ProPsiphon Pro is a virtual private network (VPN) application designed to provide users with secure and unrestricted access to the internet. Available for the Android platform, Psiphon Pro allows individuals to browse the web freely while protecting their online privacy. By downloading Psiph
Psiphon ProPsiphon Pro is a virtual private network (VPN) application designed to provide users with secure and unrestricted access to the internet. Available for the Android platform, Psiphon Pro allows individuals to browse the web freely while protecting their online privacy. By downloading Psiph -
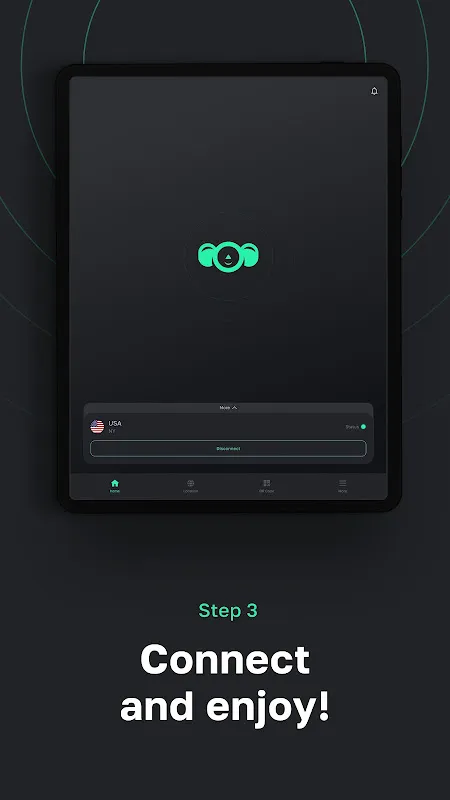 The smell of burnt espresso beans mixed with my rising panic as I stared at the café's sketchy Wi-Fi network. My client's confidential contracts sat open on-screen – financial details that could sink both our careers if intercepted. Sweat trickled down my neck as I imagined hackers swarming like digital piranhas. That's when I fumbled for 4ebur.net VPN, my fingers trembling on the phone. The military-grade encryption kicked in before I finished my first shaky breath, wrapping my data in layers o
The smell of burnt espresso beans mixed with my rising panic as I stared at the café's sketchy Wi-Fi network. My client's confidential contracts sat open on-screen – financial details that could sink both our careers if intercepted. Sweat trickled down my neck as I imagined hackers swarming like digital piranhas. That's when I fumbled for 4ebur.net VPN, my fingers trembling on the phone. The military-grade encryption kicked in before I finished my first shaky breath, wrapping my data in layers o -
 Rain lashed against the café windows in Istanbul's Grand Bazaar as I hunched over my laptop, sweat mixing with the steam rising from my untouched çay. My editor's deadline screamed in red font while the "connection insecure" browser warning mocked me. That public Wi-Fi felt like broadcasting my research notes to every hacker in the souk - until my thumb found the compass icon. With one tap, TrymeVPN spun my data into encrypted confetti, scattering it through Swiss servers before reassembling saf
Rain lashed against the café windows in Istanbul's Grand Bazaar as I hunched over my laptop, sweat mixing with the steam rising from my untouched çay. My editor's deadline screamed in red font while the "connection insecure" browser warning mocked me. That public Wi-Fi felt like broadcasting my research notes to every hacker in the souk - until my thumb found the compass icon. With one tap, TrymeVPN spun my data into encrypted confetti, scattering it through Swiss servers before reassembling saf -
 The acidic tang of stale coffee burned my throat as I hunched over my laptop at gate 37. Outside, Munich Airport's lights blurred through rain-smeared glass while my cursor pulsed over the "Submit Proposal" button. One click to secure the contract that would save my startup. One click that refused to happen. Geo-blocked flashed like a death sentence - the client's server rejecting my location. Sweat prickled beneath my collar as departure announcements mocked my 47-minute deadline. This wasn't j
The acidic tang of stale coffee burned my throat as I hunched over my laptop at gate 37. Outside, Munich Airport's lights blurred through rain-smeared glass while my cursor pulsed over the "Submit Proposal" button. One click to secure the contract that would save my startup. One click that refused to happen. Geo-blocked flashed like a death sentence - the client's server rejecting my location. Sweat prickled beneath my collar as departure announcements mocked my 47-minute deadline. This wasn't j -
 Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp
Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp -
 The smell of burnt espresso beans mixed with dread as I hunched over my laptop at Café de Flore. My fingers hovered above the login button for my client's financial portal when the public Wi-Fi notification flashed like a burglar's flashlight. Sweat prickled my neck - this contract could make or break my freelance career, yet here I was about to send sensitive data through digital sewer pipes. Then I remembered the blue shield icon on my homescreen. One tap. Suddenly, the invisible armor of mili
The smell of burnt espresso beans mixed with dread as I hunched over my laptop at Café de Flore. My fingers hovered above the login button for my client's financial portal when the public Wi-Fi notification flashed like a burglar's flashlight. Sweat prickled my neck - this contract could make or break my freelance career, yet here I was about to send sensitive data through digital sewer pipes. Then I remembered the blue shield icon on my homescreen. One tap. Suddenly, the invisible armor of mili -
 VPN Gate ClientVPN Gate Client is an application that allows your device to find and connect to free VPN servers owned by volunteers worldwide through the VPN Gate project. Once it is connected, your device's connection data will go through the server your device is connected to.This app allows you to find and sort the list of servers available with the protocol OpenVPN TCP, OpenVPN UDP, or SSTP.This app also allows you to add any server you like to your favorite list and connect to our dedicate
VPN Gate ClientVPN Gate Client is an application that allows your device to find and connect to free VPN servers owned by volunteers worldwide through the VPN Gate project. Once it is connected, your device's connection data will go through the server your device is connected to.This app allows you to find and sort the list of servers available with the protocol OpenVPN TCP, OpenVPN UDP, or SSTP.This app also allows you to add any server you like to your favorite list and connect to our dedicate -
 Rain lashed against my apartment window when the notification chimed – a calendar alert for my sister's abortion consultation. My blood froze. We'd only discussed it yesterday via a mainstream messenger. Now this? I hurled my phone onto the couch like radioactive waste. That moment crystallized my digital vulnerability: our conversations were commodities, mined and sold while we pretended encryption meant safety.
Rain lashed against my apartment window when the notification chimed – a calendar alert for my sister's abortion consultation. My blood froze. We'd only discussed it yesterday via a mainstream messenger. Now this? I hurled my phone onto the couch like radioactive waste. That moment crystallized my digital vulnerability: our conversations were commodities, mined and sold while we pretended encryption meant safety. -
 Rain lashed against Milan Central Station's glass roof as I huddled near a charging station, my laptop balanced precariously on my knees. That client proposal couldn't wait - 87 pages of financial forecasts and acquisition strategies due in 40 minutes. My fingers trembled hitting "connect" to the station's free network. Within seconds, a pop-up appeared: "Your device may be compromised." Ice shot through my veins imagining corporate spies lurking in the digital shadows of this transit hub.
Rain lashed against Milan Central Station's glass roof as I huddled near a charging station, my laptop balanced precariously on my knees. That client proposal couldn't wait - 87 pages of financial forecasts and acquisition strategies due in 40 minutes. My fingers trembled hitting "connect" to the station's free network. Within seconds, a pop-up appeared: "Your device may be compromised." Ice shot through my veins imagining corporate spies lurking in the digital shadows of this transit hub. -
 Amnezia VPNFree open-source software for creating a personal VPN on your virtual server, as well as for connecting to VPN services from Amnezia, such as:Amnezia Free \xe2\x80\x93 a free VPN for accessing public resources in Iran, Russia, Myanmar, and Kyrgyzstan.Amnezia Premium \xe2\x80\x93 a paid VP
Amnezia VPNFree open-source software for creating a personal VPN on your virtual server, as well as for connecting to VPN services from Amnezia, such as:Amnezia Free \xe2\x80\x93 a free VPN for accessing public resources in Iran, Russia, Myanmar, and Kyrgyzstan.Amnezia Premium \xe2\x80\x93 a paid VP -
 Rain lashed against my home office window as midnight approached, the blue glow of my laptop highlighting trembling fingers. Mortgage refinancing documents lay scattered like betrayal letters across my desk. Sending them via standard email felt like shouting my social security number in a crowded train station. That familiar acid reflux burned my throat - financial vulnerability distilled into physical pain. The Digital Handshake
Rain lashed against my home office window as midnight approached, the blue glow of my laptop highlighting trembling fingers. Mortgage refinancing documents lay scattered like betrayal letters across my desk. Sending them via standard email felt like shouting my social security number in a crowded train station. That familiar acid reflux burned my throat - financial vulnerability distilled into physical pain. The Digital Handshake -
 Rain lashed against the hospital windows as I frantically searched my bag for my mother's medication list. Her sudden dizzy spell during dinner had sent us racing to ER, and now doctors needed her full history - blood thinners, allergy triggers, that experimental heart protocol from last summer. My fingers trembled as I dumped crumpled pharmacy receipts onto the vinyl seat. Then I remembered: three weeks prior, I'd grudgingly digitized her medical chaos into JioHealthHub. With one tap, her entir
Rain lashed against the hospital windows as I frantically searched my bag for my mother's medication list. Her sudden dizzy spell during dinner had sent us racing to ER, and now doctors needed her full history - blood thinners, allergy triggers, that experimental heart protocol from last summer. My fingers trembled as I dumped crumpled pharmacy receipts onto the vinyl seat. Then I remembered: three weeks prior, I'd grudgingly digitized her medical chaos into JioHealthHub. With one tap, her entir
