The Coffee Shop Intruder
The Coffee Shop Intruder
My fingers trembled against the ceramic mug as I watched Dave from accounting flip through my unlocked phone. That smug grin stretching across his face felt like physical violation - he'd snatched it while I was ordering, claiming he "just wanted to check the time." Through the espresso machine's hiss, I heard my Instagram notifications pinging. AppLock Ultimate Privacy Shield activated exactly 1.7 seconds later, blacking out the screen with a fingerprint prompt I knew he couldn't bypass.
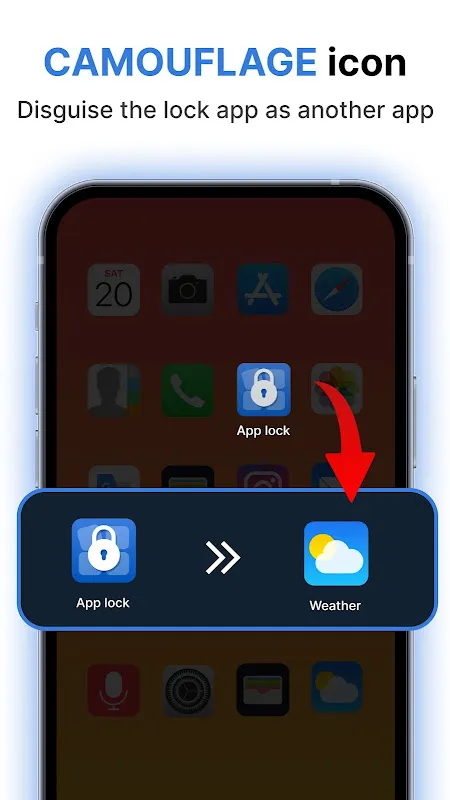
Three months earlier, I wouldn't have this digital bodyguard. I'd learned the hard way when my ex "accidentally" scrolled through my therapy journal during brunch. That cold dread pooling in my stomach - knowing someone violated thoughts I'd never shared aloud - became my breaking point. Research led me to AppLock's military-grade encryption protocols, but what sold me was the decoy feature: create fake error messages when intruders attempt access. The app doesn't just lock doors; it builds labyrinths.
Back in the coffee shop, Dave's smirk vanished as the screen demanded biometric verification. He jabbed angrily at the home button while I calmly stirred my latte. Underneath that simple lock screen, AppLock was executing multiple security layers: first scanning for brute-force attempts, then activating front-camera surveillance. What Dave didn't see was the timestamped evidence piling up in my encrypted vault - every failed fingerprint attempt documented alongside his flustered expression.
Setting up the shield felt like conducting digital surgery. The app's advanced menu revealed terrifying vulnerabilities I never considered: apps with permission to access my microphone even when closed, dormant background processes leaking location data. AppLock's permission autopsy became my revelation - it doesn't just block entry points but seals architectural cracks in Android's framework. Though initially overwhelmed by options like "fake crash reports" and "invisible lock patterns," I soon appreciated how granular control could be. My banking app now requires both facial recognition and a PIN, while my photo gallery triggers decoy error messages for anyone but me.
Watching Dave surrender my phone felt sweeter than the caramel drizzle on my coffee. "Broken screen?" he lied, avoiding my stare. I swiped open seamlessly, the app instantly disabling perimeter defenses as it recognized my thumbprint. That satisfying vibration - three short pulses signaling "threat neutralized" - released tension from my shoulders I hadn't realized I'd carried. Later, reviewing the intrusion log felt cathartic: timestamps, screenshots, even a 10-second audio clip capturing Dave's frustrated muttering. This wasn't just security; it was justice.
Not every feature sings perfectly. The stealth mode occasionally fights with my phone's OS updates, requiring tedious reconfigurations. And god help you if you forget your master pattern - account recovery involves jumping through more hoops than a CIA background check. But when I discovered Dave had been snooping through colleagues' devices for months, I silently emailed HR the evidence bundle AppLock compiled. Watching him pack his desk the next week, I realized this wasn't just an app. It's a silent revolution against digital voyeurism, one encrypted layer at a time.
Keywords:AppLock Ultimate Privacy Shield,news,digital privacy invasion,encryption protocols,stealth security systems









