Automated Security 2025-11-05T10:53:01Z
-

\xe3\x82\xa6\xe3\x82\xa7\xe3\x83\xab\xe3\x82\xb9\xe3\x83\x8a\xe3\x83\x93\xe3\x81\xa7\xe5\x85\xa8\xe8
\xe3\x82\xa6\xe3\x82\xa7\xe3\x83\xab\xe3\x82\xb9\xe3\x83\x8a\xe3\x83\x93\xe3\x81\xa7\xe5\x85\xa8\xe8\x87\xaa\xe5\x8b\x95\xe3\x81\xae\xe8\xb3\x87\xe7\x94\xa3\xe9\x81\x8b\xe7\x94\xa8\xe3\x82\x92\xe2\x96\xa0 Robo-advisor with over 1.4 trillion yen in assets under management (\xe2\x80\xbb1) and 430,000 -
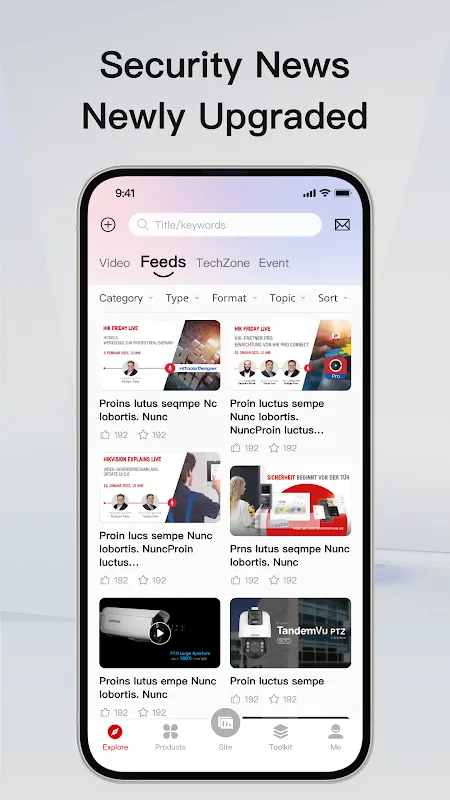 The alarm panel screamed at 3 AM - that shrill, relentless beeping that turns your stomach to ice. Three client sites flashed critical alerts simultaneously as rainwater seeped into server rooms. My fingers fumbled across three different monitoring apps, each with contradictory data. One showed offline cameras at the pharmaceutical warehouse while another insisted everything was operational. Sweat soaked my collar as I imagined stolen narcotics and lawsuits. That's when my laptop died. In the su
The alarm panel screamed at 3 AM - that shrill, relentless beeping that turns your stomach to ice. Three client sites flashed critical alerts simultaneously as rainwater seeped into server rooms. My fingers fumbled across three different monitoring apps, each with contradictory data. One showed offline cameras at the pharmaceutical warehouse while another insisted everything was operational. Sweat soaked my collar as I imagined stolen narcotics and lawsuits. That's when my laptop died. In the su -
 Rain lashed against the windows like frozen nails, the kind of storm that makes you question every creak and groan in an old house. I’d just buried myself under blankets when my phone erupted—not a ring, but a shrill, mechanical scream from the security app monitoring my aunt’s vacant rental property three states away. Another alert followed, then another. Three properties, all blaring intrusion alarms simultaneously. My throat tightened. This wasn’t just false alarms; it felt coordinated. I fum
Rain lashed against the windows like frozen nails, the kind of storm that makes you question every creak and groan in an old house. I’d just buried myself under blankets when my phone erupted—not a ring, but a shrill, mechanical scream from the security app monitoring my aunt’s vacant rental property three states away. Another alert followed, then another. Three properties, all blaring intrusion alarms simultaneously. My throat tightened. This wasn’t just false alarms; it felt coordinated. I fum -
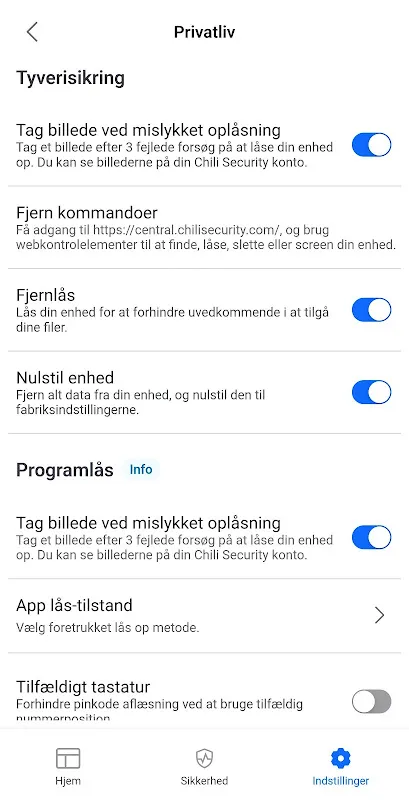 That heart-stopping moment when my phone buzzed with a "Bank of America" alert at 3 AM still haunts me. Sweaty palms gripping the device as a polished login screen demanded my credentials to "stop suspicious activity." Logic screamed scam but sleep-deprived panic nearly won - until a tiny green shield icon flared in the corner. Chili Security's silent interception of that phishing trap didn't just protect my savings; it salvaged my trust in technology itself.
That heart-stopping moment when my phone buzzed with a "Bank of America" alert at 3 AM still haunts me. Sweaty palms gripping the device as a polished login screen demanded my credentials to "stop suspicious activity." Logic screamed scam but sleep-deprived panic nearly won - until a tiny green shield icon flared in the corner. Chili Security's silent interception of that phishing trap didn't just protect my savings; it salvaged my trust in technology itself. -
 My cheeks still burn remembering that university open day disaster. I'd volunteered for bag checks, eager to help - until a chirpy grandmother sailed past my station with knitting needles protruding from her tote like antennae. "Oh, just my arthritis grips, dear!" she smiled while campus police later confiscated them beside the chemistry lab. That humiliation clung like cheap cologne as I downloaded I Am Security at 3 AM, vowing never to be fooled again.
My cheeks still burn remembering that university open day disaster. I'd volunteered for bag checks, eager to help - until a chirpy grandmother sailed past my station with knitting needles protruding from her tote like antennae. "Oh, just my arthritis grips, dear!" she smiled while campus police later confiscated them beside the chemistry lab. That humiliation clung like cheap cologne as I downloaded I Am Security at 3 AM, vowing never to be fooled again. -
 Thinventory KonnectKonnect\xe2\x84\xa2 allows you to identify and access Thinventory App Boxes easily and quickly. The hi-tech Bluetooth-enabled Smart Boxes require no keys and no pin numbers, you just need the Konnect\xe2\x84\xa2 app. Once registered, Konnect\xe2\x84\xa2 will enable you to view all
Thinventory KonnectKonnect\xe2\x84\xa2 allows you to identify and access Thinventory App Boxes easily and quickly. The hi-tech Bluetooth-enabled Smart Boxes require no keys and no pin numbers, you just need the Konnect\xe2\x84\xa2 app. Once registered, Konnect\xe2\x84\xa2 will enable you to view all -
 Ita\xc3\xba Empresas: Conta PJIta\xc3\xba Empresas is a corporate banking application designed specifically for businesses, allowing users to manage their financial activities efficiently. This app, available for the Android platform, offers various features aimed at simplifying business operations.
Ita\xc3\xba Empresas: Conta PJIta\xc3\xba Empresas is a corporate banking application designed specifically for businesses, allowing users to manage their financial activities efficiently. This app, available for the Android platform, offers various features aimed at simplifying business operations. -
 DOG VPN- VPN Free Hotspot Proxy & Wi-Fi SecurityDOG VPN is a fast and secure virtual private network application designed for Android devices. This app provides users with a reliable way to connect to the internet while maintaining their privacy and security. DOG VPN is also recognized for its abili
DOG VPN- VPN Free Hotspot Proxy & Wi-Fi SecurityDOG VPN is a fast and secure virtual private network application designed for Android devices. This app provides users with a reliable way to connect to the internet while maintaining their privacy and security. DOG VPN is also recognized for its abili -
 Cart\xc3\xa3o de Cr\xc3\xa9dito: nov\xc3\xbccardMeet the nov\xc3\xbccard, the credit card for those who think about the future.The nov\xc3\xbccard is a reliable card, with no annual fees, no bureaucracy and full of exclusive benefits that make a difference in your daily life.With it, you can automat
Cart\xc3\xa3o de Cr\xc3\xa9dito: nov\xc3\xbccardMeet the nov\xc3\xbccard, the credit card for those who think about the future.The nov\xc3\xbccard is a reliable card, with no annual fees, no bureaucracy and full of exclusive benefits that make a difference in your daily life.With it, you can automat -
 Rain lashed against the train window as we jolted through the Swiss Alps, turning the scenery into a watercolor blur. I gripped my BlackBerry tighter, knuckles white. On the screen glowed a draft of our pharmaceutical patent submission – 87 pages of research that could tank our IPO if leaked prematurely. My CEO's frantic email blinked in my notifications: "FDA found discrepancies in Appendix B. Fix before Zurich meeting in 3 hours." Every public Wi-Fi network at these rural stations felt like a
Rain lashed against the train window as we jolted through the Swiss Alps, turning the scenery into a watercolor blur. I gripped my BlackBerry tighter, knuckles white. On the screen glowed a draft of our pharmaceutical patent submission – 87 pages of research that could tank our IPO if leaked prematurely. My CEO's frantic email blinked in my notifications: "FDA found discrepancies in Appendix B. Fix before Zurich meeting in 3 hours." Every public Wi-Fi network at these rural stations felt like a -
 That sinking feeling hit me halfway through my Lisbon trip – an overdue utility bill notification flashed on my phone while I sipped espresso in a sun-drenched café. My hands went clammy; back home, banks were closed for hours. Panic tightened my chest until I fumbled for my phone and tapped the familiar icon. Biometric authentication recognized my frantic fingerprint in milliseconds, flooding the screen with a clean dashboard where pending payments glowed like warning lights. One swipe, a confi
That sinking feeling hit me halfway through my Lisbon trip – an overdue utility bill notification flashed on my phone while I sipped espresso in a sun-drenched café. My hands went clammy; back home, banks were closed for hours. Panic tightened my chest until I fumbled for my phone and tapped the familiar icon. Biometric authentication recognized my frantic fingerprint in milliseconds, flooding the screen with a clean dashboard where pending payments glowed like warning lights. One swipe, a confi -
 Ivanti Mobile@WorkIvanti's Mobile@Work securely connects your Android and WearOS device to your company network so that you can easily access email and other work resources.Best Technology\xe2\x98\x86 Purpose-built for Mobile IT with millions of users globally\xe2\x98\x86 Complete separation of corp
Ivanti Mobile@WorkIvanti's Mobile@Work securely connects your Android and WearOS device to your company network so that you can easily access email and other work resources.Best Technology\xe2\x98\x86 Purpose-built for Mobile IT with millions of users globally\xe2\x98\x86 Complete separation of corp -
 Codeproof MDM for AndroidCodeproof is an Enterprise Mobility Management (EMM) solution for Android devices that offers a range of features designed to enhance mobile device security and management. This app is focused on providing businesses with the tools they need to monitor and manage their mobile assets effectively. Organizations can download Codeproof for Android to implement policies and protect their data.The app supports both Device Owner and Profile Owner modes of Android Enterprise, al
Codeproof MDM for AndroidCodeproof is an Enterprise Mobility Management (EMM) solution for Android devices that offers a range of features designed to enhance mobile device security and management. This app is focused on providing businesses with the tools they need to monitor and manage their mobile assets effectively. Organizations can download Codeproof for Android to implement policies and protect their data.The app supports both Device Owner and Profile Owner modes of Android Enterprise, al -
 TP-Link TapoTP-Link Tapo is a smart home app designed to manage and control Tapo smart devices from various locations. This application is available for the Android platform, enabling users to download TP-Link Tapo and seamlessly set up their smart devices. The app provides a user-friendly interface
TP-Link TapoTP-Link Tapo is a smart home app designed to manage and control Tapo smart devices from various locations. This application is available for the Android platform, enabling users to download TP-Link Tapo and seamlessly set up their smart devices. The app provides a user-friendly interface -
 Rain lashed against the windows as I squinted at my laptop screen, another Zoom call descending into pixelated chaos. Sunlight stabbed through the gap in the blinds, bleaching half my face white while the other half drowned in shadow. "Can you repeat that? The glare's brutal here," I mumbled, fumbling behind me to tug the cord. The ancient Venetian blind clattered like a startled skeleton, dust motes dancing in the sudden beam. In that moment, I hated my windows. Truly, deeply hated them. This w
Rain lashed against the windows as I squinted at my laptop screen, another Zoom call descending into pixelated chaos. Sunlight stabbed through the gap in the blinds, bleaching half my face white while the other half drowned in shadow. "Can you repeat that? The glare's brutal here," I mumbled, fumbling behind me to tug the cord. The ancient Venetian blind clattered like a startled skeleton, dust motes dancing in the sudden beam. In that moment, I hated my windows. Truly, deeply hated them. This w -
 4ebur.net VPN - Fast VPN4ebur.net VPN is a secure, anonymous connection to the Internet.Worried about your privacy? Protect yourself from hackers and enjoy your favorite content on the go with 4ebur.net VPN! We guarantee a fast, secure and private Internet connection so that you remain anonymous onl
4ebur.net VPN - Fast VPN4ebur.net VPN is a secure, anonymous connection to the Internet.Worried about your privacy? Protect yourself from hackers and enjoy your favorite content on the go with 4ebur.net VPN! We guarantee a fast, secure and private Internet connection so that you remain anonymous onl -
 ExpenseOnDemand: Expenses AppPaper based claims or a manual expense claim system is fraught with delays, mistakes and abuse. Detecting fraud is nearly impossible! Employee expense automations, where the mobile phone is leveraged is the answer to ensuring a seamless process with no delays, errors and 100% compliance. And bringing fraud to ZERO! ExpenseOnDemand is a revolutionary 'on-the-go' business expense report app that helps you manage business expenses in the most effective and efficient man
ExpenseOnDemand: Expenses AppPaper based claims or a manual expense claim system is fraught with delays, mistakes and abuse. Detecting fraud is nearly impossible! Employee expense automations, where the mobile phone is leveraged is the answer to ensuring a seamless process with no delays, errors and 100% compliance. And bringing fraud to ZERO! ExpenseOnDemand is a revolutionary 'on-the-go' business expense report app that helps you manage business expenses in the most effective and efficient man -
 Visitor SignInEasyVisitor SignInEasy is an effective application from Splan to manage visitor\xe2\x80\x99s appointments.Splan specializes in providing next generation cloud-based, Mobile technology based visitor management solutions by delivering a uniquely intelligent and fully automated, self-service visitor check-in solution creating a smarter way to manage visitors, employees, vendors, students and events with enhanced security.Splan provides a secure, web based visitor management system for
Visitor SignInEasyVisitor SignInEasy is an effective application from Splan to manage visitor\xe2\x80\x99s appointments.Splan specializes in providing next generation cloud-based, Mobile technology based visitor management solutions by delivering a uniquely intelligent and fully automated, self-service visitor check-in solution creating a smarter way to manage visitors, employees, vendors, students and events with enhanced security.Splan provides a secure, web based visitor management system for -
 Knock on PortsUnlock your server's secret knock!Knock on Ports is the ultimate port knocking client for Android, giving you secure and seamless access to services hidden behind firewalls.Craft custom knock sequences using UDP, TCP, or ICMP packets (IPv4/IPv6 support) to keep your server ports stealthy until the right "knock" unlocks them.Why Knock on Ports?\xe2\x80\xa2 Flexible Sequences: Customize UDP/TCP/ICMP packets, set interpacket delays, and fine-tune TTL/Hop Limit for all protocols.\xe2\x
Knock on PortsUnlock your server's secret knock!Knock on Ports is the ultimate port knocking client for Android, giving you secure and seamless access to services hidden behind firewalls.Craft custom knock sequences using UDP, TCP, or ICMP packets (IPv4/IPv6 support) to keep your server ports stealthy until the right "knock" unlocks them.Why Knock on Ports?\xe2\x80\xa2 Flexible Sequences: Customize UDP/TCP/ICMP packets, set interpacket delays, and fine-tune TTL/Hop Limit for all protocols.\xe2\x -
 The fluorescent lights of the campus library hummed like angry bees as midnight bled into another merciless hour. My right index finger pulsed with a dull ache that had settled deep into the joint after three straight weeks of this torture. Before me, the university’s archaic digital archives demanded ritualistic sacrifice: click a thesis reference, wait seven seconds for the glacial load, hit download, confirm format, repeat. Two hundred thirty-seven times. Each click felt like scraping bone ag
The fluorescent lights of the campus library hummed like angry bees as midnight bled into another merciless hour. My right index finger pulsed with a dull ache that had settled deep into the joint after three straight weeks of this torture. Before me, the university’s archaic digital archives demanded ritualistic sacrifice: click a thesis reference, wait seven seconds for the glacial load, hit download, confirm format, repeat. Two hundred thirty-seven times. Each click felt like scraping bone ag