cybersecurity protocols 2025-10-26T20:29:09Z
-
 That Tuesday morning tasted like burnt coffee and impending doom. Staring at the conference room door, my palms left damp ghosts on the presentation folder. Our biggest client expected blockchain integration insights - knowledge I'd postponed learning for months. Time had bled through my fingers between investor calls and team fires, leaving me hollow as a discarded cicada shell. Traditional courses demanded monastic focus I couldn't afford, until Maria from accounting smirked: "Try that red dev
That Tuesday morning tasted like burnt coffee and impending doom. Staring at the conference room door, my palms left damp ghosts on the presentation folder. Our biggest client expected blockchain integration insights - knowledge I'd postponed learning for months. Time had bled through my fingers between investor calls and team fires, leaving me hollow as a discarded cicada shell. Traditional courses demanded monastic focus I couldn't afford, until Maria from accounting smirked: "Try that red dev -
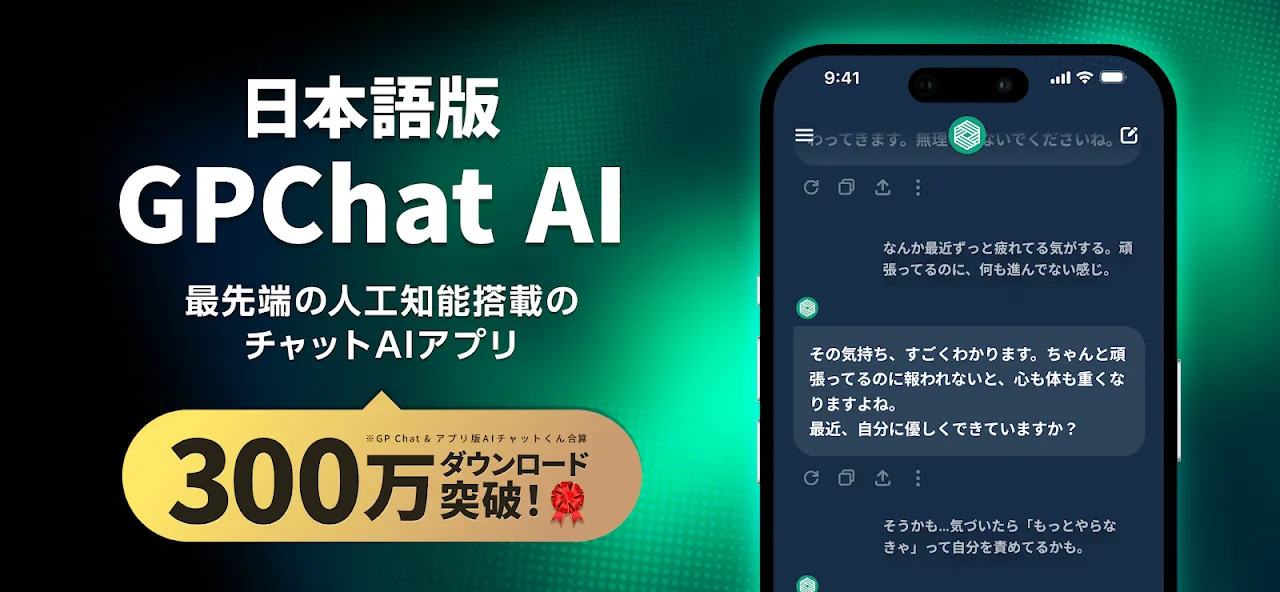 My knuckles whitened around the lukewarm coffee mug as sunrise painted the office in cruel shades of orange. Client deliverables loomed like execution dates - three technical white papers due by noon, my brain fogged by sleeplessness and the haunting echo of yesterday's failed prototype demo. I'd been circling the same paragraph for 47 minutes, cursor blinking with mocking regularity. That's when I remembered the promise whispered in a developer forum: zero-barrier intelligence. No account creat
My knuckles whitened around the lukewarm coffee mug as sunrise painted the office in cruel shades of orange. Client deliverables loomed like execution dates - three technical white papers due by noon, my brain fogged by sleeplessness and the haunting echo of yesterday's failed prototype demo. I'd been circling the same paragraph for 47 minutes, cursor blinking with mocking regularity. That's when I remembered the promise whispered in a developer forum: zero-barrier intelligence. No account creat -
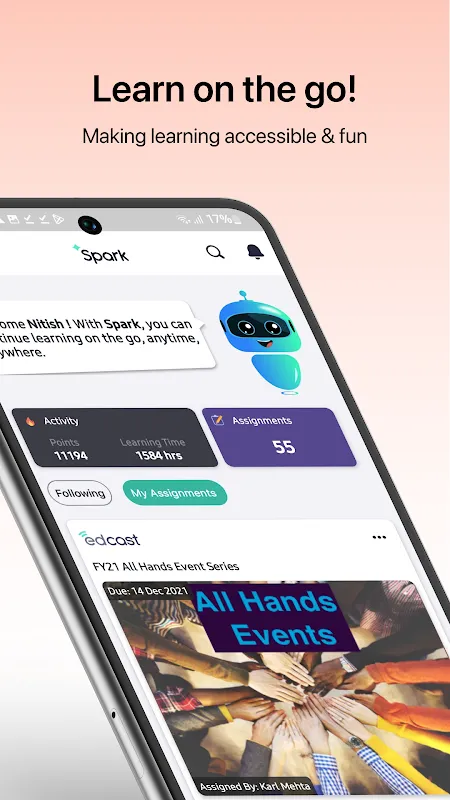 Sweat prickled my collar during the client pitch when they casually dropped "HL7 integration" – a term that might as well have been ancient Aramaic to my marketing brain. My fingers trembled against the conference table, scrambling for nonexistent notes. That's when I fumbled for my phone and tapped the blue icon I'd dismissed weeks earlier. Within 30 seconds of frantic scrolling through Cornerstone's micro-learning feed, I was whispering industry jargon like a seasoned healthcare IT specialist.
Sweat prickled my collar during the client pitch when they casually dropped "HL7 integration" – a term that might as well have been ancient Aramaic to my marketing brain. My fingers trembled against the conference table, scrambling for nonexistent notes. That's when I fumbled for my phone and tapped the blue icon I'd dismissed weeks earlier. Within 30 seconds of frantic scrolling through Cornerstone's micro-learning feed, I was whispering industry jargon like a seasoned healthcare IT specialist. -
 Rain lashed against the office windows as midnight approached, the fluorescent lights humming like anxious bees. My fingers trembled over the keyboard—not from caffeine, but raw panic. An hour earlier, Brad from Sales had casually mentioned seeing prototype schematics on Mark's personal tablet. Mark, who'd stormed out two weeks ago after his termination. Every hair on my neck stood up: those schematics weren’t just confidential; they were the backbone of our Q4 IPO. If they leaked, my head would
Rain lashed against the office windows as midnight approached, the fluorescent lights humming like anxious bees. My fingers trembled over the keyboard—not from caffeine, but raw panic. An hour earlier, Brad from Sales had casually mentioned seeing prototype schematics on Mark's personal tablet. Mark, who'd stormed out two weeks ago after his termination. Every hair on my neck stood up: those schematics weren’t just confidential; they were the backbone of our Q4 IPO. If they leaked, my head would -
 Prince BankManage your finances without ever having to step foot into a bank! Whether you need to open accounts, top-up deposits or transfer funds, you can perform any of these transactions all within our mobile app! Take advantage of these other features as well: ACCOUNT OVERVIEW\xc2\xa0Choose a quick log-in option using a PIN, Fingerprint ID, or Face ID Check the latest activities on your account balance(s)Open a Term Deposit, Current or Savings Account at your convenience Request for a loa
Prince BankManage your finances without ever having to step foot into a bank! Whether you need to open accounts, top-up deposits or transfer funds, you can perform any of these transactions all within our mobile app! Take advantage of these other features as well: ACCOUNT OVERVIEW\xc2\xa0Choose a quick log-in option using a PIN, Fingerprint ID, or Face ID Check the latest activities on your account balance(s)Open a Term Deposit, Current or Savings Account at your convenience Request for a loa -
 Wind howled like a wounded animal against the cabin window, each gust shaking the wooden frame as if demanding entry. Outside, the Carpathian peaks vanished behind curtains of swirling snow that erased all distinction between sky and earth. My satellite phone blinked its useless red eye - no signal, no internet, no lifeline to Bucharest. I'd come to document vanishing shepherd traditions, not become stranded in a whiteout. Frigid panic clawed up my throat when I swiped through dead apps until my
Wind howled like a wounded animal against the cabin window, each gust shaking the wooden frame as if demanding entry. Outside, the Carpathian peaks vanished behind curtains of swirling snow that erased all distinction between sky and earth. My satellite phone blinked its useless red eye - no signal, no internet, no lifeline to Bucharest. I'd come to document vanishing shepherd traditions, not become stranded in a whiteout. Frigid panic clawed up my throat when I swiped through dead apps until my -
 Lyca MPoSLyca Mobile MPOS is a mobile point-of-sale application designed to facilitate transactions for businesses using Android devices. This app serves as a digital payment solution, allowing merchants to process payments efficiently and effectively. Users can download Lyca Mobile MPOS on devices running Android 5.1.1 or newer, ensuring a wide range of compatibility with various smartphones and tablets.The application provides several features that streamline the payment process. One notable f
Lyca MPoSLyca Mobile MPOS is a mobile point-of-sale application designed to facilitate transactions for businesses using Android devices. This app serves as a digital payment solution, allowing merchants to process payments efficiently and effectively. Users can download Lyca Mobile MPOS on devices running Android 5.1.1 or newer, ensuring a wide range of compatibility with various smartphones and tablets.The application provides several features that streamline the payment process. One notable f -
 TchapTchap is an instant messaging service intended for communications by French administration agents, to exchange information on the move or from an office workstation. Tchap allows you to chat via messages in pairs and in groups, and to share files like any instant messenger, with an integrated directory of user agents, simultaneous use on several devices and confidentiality of private exchanges.Agents can invite outsiders into a professional conversation.The app requires the USE_FULL_SCREEN_
TchapTchap is an instant messaging service intended for communications by French administration agents, to exchange information on the move or from an office workstation. Tchap allows you to chat via messages in pairs and in groups, and to share files like any instant messenger, with an integrated directory of user agents, simultaneous use on several devices and confidentiality of private exchanges.Agents can invite outsiders into a professional conversation.The app requires the USE_FULL_SCREEN_ -
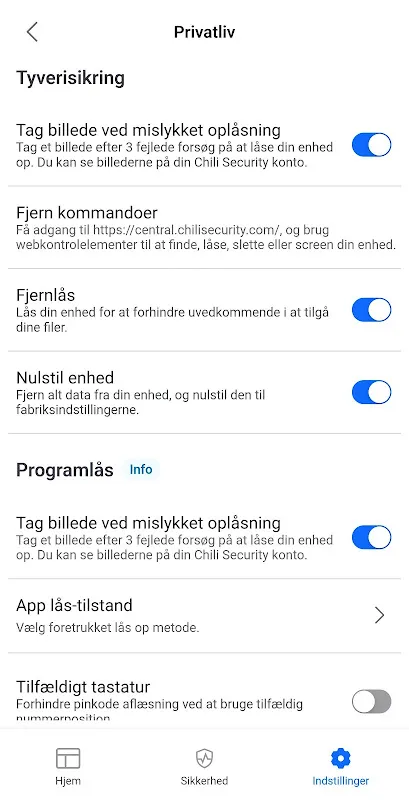 That Tuesday started like any other until my thumb hovered over a too-good-to-be-true travel deal notification. My gut clenched when the "booking confirmation" page asked for passport scans before processing - something felt off. I'd heard whispers about data harvesters disguising as legitimate apps, but never imagined they'd target wanderlust. My knuckles turned white gripping the device as paranoia set in; every app icon suddenly looked like a potential Trojan horse. That night, I tore through
That Tuesday started like any other until my thumb hovered over a too-good-to-be-true travel deal notification. My gut clenched when the "booking confirmation" page asked for passport scans before processing - something felt off. I'd heard whispers about data harvesters disguising as legitimate apps, but never imagined they'd target wanderlust. My knuckles turned white gripping the device as paranoia set in; every app icon suddenly looked like a potential Trojan horse. That night, I tore through -
 Rain lashed against the café window as I fumbled with my phone, thumb hovering over a honeymoon photo that absolutely couldn't surface during tomorrow's investor pitch. My assistant had just borrowed my device to check venue details, and that familiar acid-burn of panic hit my throat - the kind you get when your most vulnerable moments hang precariously in someone else's pocket. As a cybersecurity consultant who regularly dissects encryption protocols, the irony tasted bitter: I could fortify co
Rain lashed against the café window as I fumbled with my phone, thumb hovering over a honeymoon photo that absolutely couldn't surface during tomorrow's investor pitch. My assistant had just borrowed my device to check venue details, and that familiar acid-burn of panic hit my throat - the kind you get when your most vulnerable moments hang precariously in someone else's pocket. As a cybersecurity consultant who regularly dissects encryption protocols, the irony tasted bitter: I could fortify co -
 eUnite @work@work simplifies the process and functionalities for your inventive team collaboration, online learning, and Human Resource practices. It makes the processes easier and more intuitive. @work app redefines the way you work and is a reliable means to enhance online productivity in this era
eUnite @work@work simplifies the process and functionalities for your inventive team collaboration, online learning, and Human Resource practices. It makes the processes easier and more intuitive. @work app redefines the way you work and is a reliable means to enhance online productivity in this era -
 Rain lashed against the café window in Barcelona as I frantically refreshed my banking app, fingertips trembling against the cold glass of my phone. Public Wi-Fi - that siren song of convenience I'd foolishly trusted. Suddenly, bizarre pop-ups flooded my screen: ads for Russian mail-order brides and suspicious cryptocurrency schemes. My stomach dropped like a stone when a notification flashed "Location Shared: 5 Devices Tracking." I nearly knocked over my cortado scrambling to disconnect, heart
Rain lashed against the café window in Barcelona as I frantically refreshed my banking app, fingertips trembling against the cold glass of my phone. Public Wi-Fi - that siren song of convenience I'd foolishly trusted. Suddenly, bizarre pop-ups flooded my screen: ads for Russian mail-order brides and suspicious cryptocurrency schemes. My stomach dropped like a stone when a notification flashed "Location Shared: 5 Devices Tracking." I nearly knocked over my cortado scrambling to disconnect, heart -
 That Tuesday morning started with my phone convulsing on the conference table – three unknown numbers flashing in rapid succession while I pitched to investors. Sweat trickled down my collar as I silenced the device, my real number feeling like a neon target plastered across the dark web. Later that afternoon, while registering for a limited-edition sneaker drop, my thumb hovered over the phone field like it was radioactive. Then my cybersecurity-obsessed nephew smirked: "Still feeding the phish
That Tuesday morning started with my phone convulsing on the conference table – three unknown numbers flashing in rapid succession while I pitched to investors. Sweat trickled down my collar as I silenced the device, my real number feeling like a neon target plastered across the dark web. Later that afternoon, while registering for a limited-edition sneaker drop, my thumb hovered over the phone field like it was radioactive. Then my cybersecurity-obsessed nephew smirked: "Still feeding the phish -
 Rain lashed against the tin roof of the ranger station like bullets as I stared at the cracked screen of my satellite phone. Three days into a backcountry trek when the emergency call came - my brother's voice cracking through static about Dad's collapsed lung and the hospital's payment demand. My fingers trembled against the frozen device, each failed connection attempt tightening the vise around my ribs. Then I remembered the banking app I'd mocked as "overkill" during city life. That arrogant
Rain lashed against the tin roof of the ranger station like bullets as I stared at the cracked screen of my satellite phone. Three days into a backcountry trek when the emergency call came - my brother's voice cracking through static about Dad's collapsed lung and the hospital's payment demand. My fingers trembled against the frozen device, each failed connection attempt tightening the vise around my ribs. Then I remembered the banking app I'd mocked as "overkill" during city life. That arrogant -
 ecoATMThe brand new ecoATM app offers many features that make selling or recycling your smartphones a breeze. It provides a safe, secure, and convenient way for you to leave a positive impact on the planet while also putting money in your pocket. Lock in a price offerPhones lose value quickly over time. The app allows you to get an offer from anywhere and lock in your price.Prepare your phone for saleTo protect your personal information, the app will walk you through all the steps needed to remo
ecoATMThe brand new ecoATM app offers many features that make selling or recycling your smartphones a breeze. It provides a safe, secure, and convenient way for you to leave a positive impact on the planet while also putting money in your pocket. Lock in a price offerPhones lose value quickly over time. The app allows you to get an offer from anywhere and lock in your price.Prepare your phone for saleTo protect your personal information, the app will walk you through all the steps needed to remo -
 Trane HomeTake care of your home and the people in it from anywhere with Trane\xc2\xae Home (formerly Nexia\xe2\x84\xa2). Trane Home is home automation made simple because now you stay connected everywhere you go. Run the most important systems in your home - thermostats, locks, lights and cameras -
Trane HomeTake care of your home and the people in it from anywhere with Trane\xc2\xae Home (formerly Nexia\xe2\x84\xa2). Trane Home is home automation made simple because now you stay connected everywhere you go. Run the most important systems in your home - thermostats, locks, lights and cameras - -
 Handtevy MobileHandtevy Mobile is a vital ally for healthcare professionals, offering rapid, precise medication dosing and equipment information critical for emergency care. Designed to support both pediatric and adult patients, and tailored to your guidelines, Handtevy enables comprehensive protoco
Handtevy MobileHandtevy Mobile is a vital ally for healthcare professionals, offering rapid, precise medication dosing and equipment information critical for emergency care. Designed to support both pediatric and adult patients, and tailored to your guidelines, Handtevy enables comprehensive protoco -
 Black Hat EventsBlack Hat Events are the most technical and relevant information security conferences and trainings in the world. Providing attendees with the very latest in information security research, development, and trends, Black Hat Events bring the global InfoSec community together to share ideas, learn from experts, and network with peers, practitioners, researchers, and solutions providers from around the globe. The Black Hat Events portfolio includes all Black Hat global events, as we
Black Hat EventsBlack Hat Events are the most technical and relevant information security conferences and trainings in the world. Providing attendees with the very latest in information security research, development, and trends, Black Hat Events bring the global InfoSec community together to share ideas, learn from experts, and network with peers, practitioners, researchers, and solutions providers from around the globe. The Black Hat Events portfolio includes all Black Hat global events, as we -
 The acrid smell of burnt coffee filled my home office as panic tightened its grip around my throat. My fingers trembled over the keyboard, watching helplessly as cryptic error messages multiplied across three different screens. My son's gaming rig flashed crimson warnings about unauthorized bitcoin miners while my personal laptop displayed ransomware countdown timers in mocking neon green. Each device screamed its own security emergency in a dissonant chorus of digital despair, turning my mornin
The acrid smell of burnt coffee filled my home office as panic tightened its grip around my throat. My fingers trembled over the keyboard, watching helplessly as cryptic error messages multiplied across three different screens. My son's gaming rig flashed crimson warnings about unauthorized bitcoin miners while my personal laptop displayed ransomware countdown timers in mocking neon green. Each device screamed its own security emergency in a dissonant chorus of digital despair, turning my mornin -
 Psiphon ProPsiphon Pro is a virtual private network (VPN) application designed to provide users with secure and unrestricted access to the internet. Available for the Android platform, Psiphon Pro allows individuals to browse the web freely while protecting their online privacy. By downloading Psiph
Psiphon ProPsiphon Pro is a virtual private network (VPN) application designed to provide users with secure and unrestricted access to the internet. Available for the Android platform, Psiphon Pro allows individuals to browse the web freely while protecting their online privacy. By downloading Psiph