encrypted monitoring 2025-11-17T00:44:05Z
-
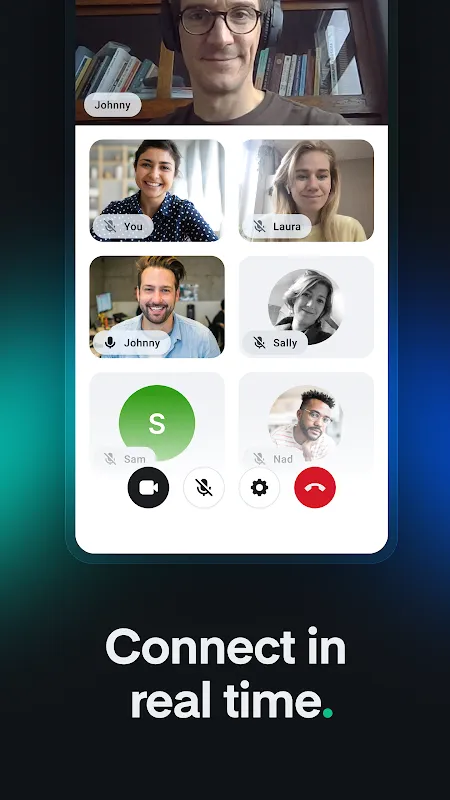 I remember the icy dread crawling up my spine when targeted ads started mocking me. There it was - the exact hiking boot I'd photographed for my dying father's bucket list trip, plastered across every platform after I'd shared it via mainstream messengers. That night, I tore through privacy forums like a madwoman, fingers trembling against my keyboard until dawn's pale light revealed Element X. The promise of true data sovereignty felt like finding an unbreakable vault in a world of cardboard lo
I remember the icy dread crawling up my spine when targeted ads started mocking me. There it was - the exact hiking boot I'd photographed for my dying father's bucket list trip, plastered across every platform after I'd shared it via mainstream messengers. That night, I tore through privacy forums like a madwoman, fingers trembling against my keyboard until dawn's pale light revealed Element X. The promise of true data sovereignty felt like finding an unbreakable vault in a world of cardboard lo -
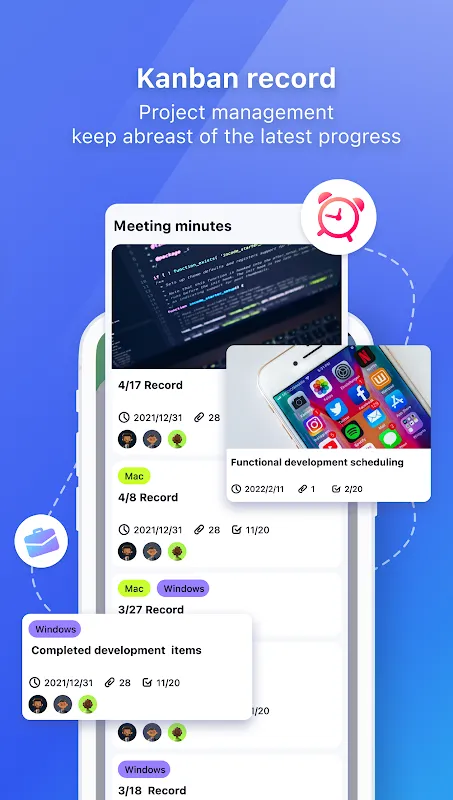 Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv.
Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv. -
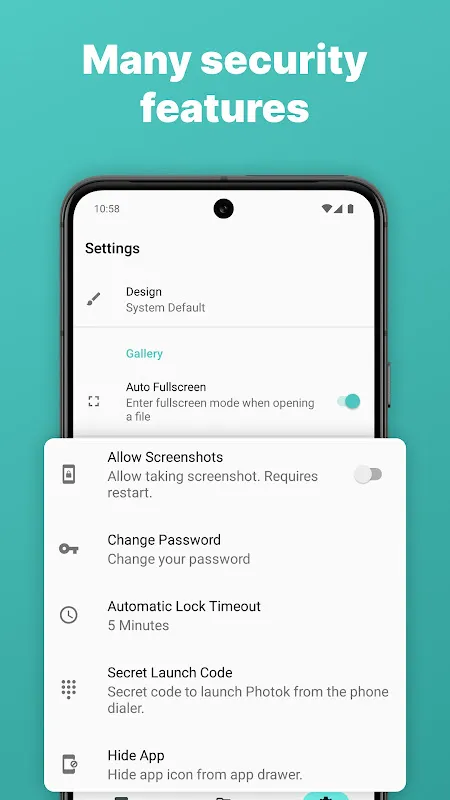 The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima
The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima -
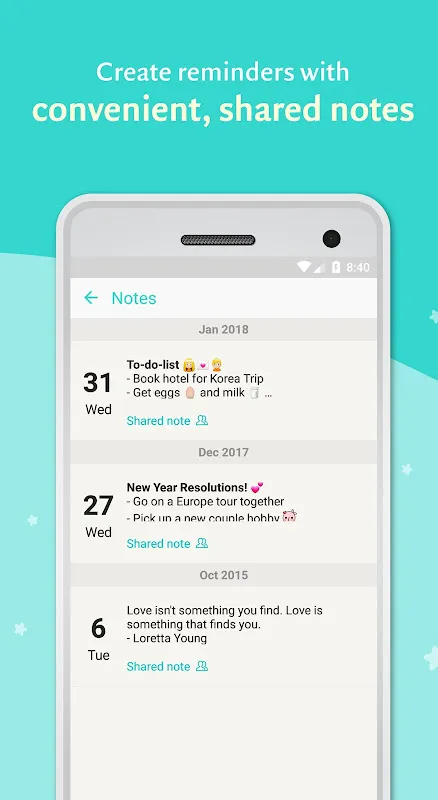 Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw
Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw -
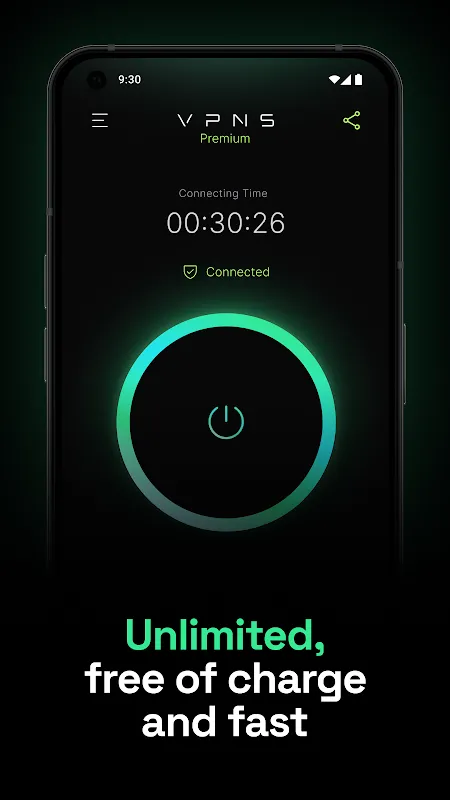 Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious
Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious -
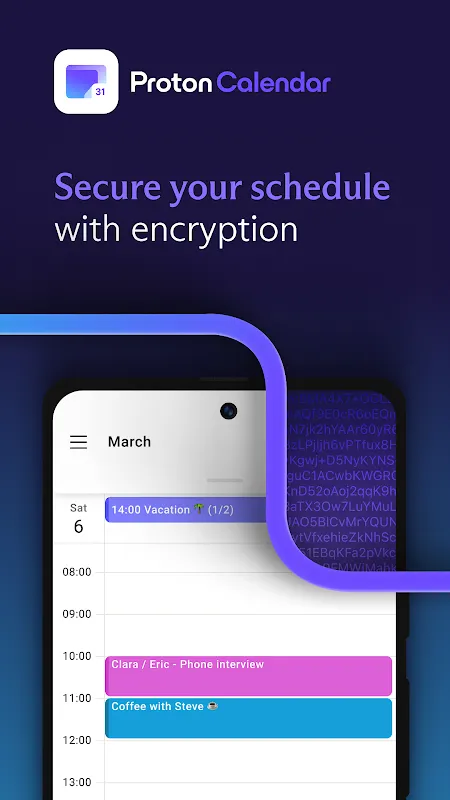 The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality.
The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality. -
 Rain lashed against the Istanbul airport windows as I hunched over my laptop, fingers trembling. That Pulitzer-chasing exposé on my screen? Worthless if intercepted. Public Wi-Fi networks here felt like digital minefields - every byte transmitted might as well be broadcast on Times Square billboards. I'd witnessed a colleague's career implode when state-sponsored hackers intercepted his research in Minsk. Now history threatened to repeat itself with this breaking story about offshore shell compa
Rain lashed against the Istanbul airport windows as I hunched over my laptop, fingers trembling. That Pulitzer-chasing exposé on my screen? Worthless if intercepted. Public Wi-Fi networks here felt like digital minefields - every byte transmitted might as well be broadcast on Times Square billboards. I'd witnessed a colleague's career implode when state-sponsored hackers intercepted his research in Minsk. Now history threatened to repeat itself with this breaking story about offshore shell compa -
 Rain lashed against the cafe window as I frantically swiped through my gallery, stomach churning. There it was - yesterday's street art photo, innocently shared online, now broadcasting the exact alley where I'd met my whistleblower source. The embedded GPS coordinates glared back like digital betrayal. In that humid panic, I finally understood how metadata turns cameras into snitches.
Rain lashed against the cafe window as I frantically swiped through my gallery, stomach churning. There it was - yesterday's street art photo, innocently shared online, now broadcasting the exact alley where I'd met my whistleblower source. The embedded GPS coordinates glared back like digital betrayal. In that humid panic, I finally understood how metadata turns cameras into snitches. -
 Rain lashed against the Bangkok guesthouse window as my fingers trembled over the keyboard. Three days. Seventy-two hours since the local government flipped the kill switch on international news portals, and my investigative piece about cross-border data trafficking was trapped in digital purgatory. Each "connection timed out" error felt like a padlock snapping shut. That's when I remembered the whisper from a cybersecurity contact: "If you truly own nothing, at least own your tunnel." The Clic
Rain lashed against the Bangkok guesthouse window as my fingers trembled over the keyboard. Three days. Seventy-two hours since the local government flipped the kill switch on international news portals, and my investigative piece about cross-border data trafficking was trapped in digital purgatory. Each "connection timed out" error felt like a padlock snapping shut. That's when I remembered the whisper from a cybersecurity contact: "If you truly own nothing, at least own your tunnel." The Clic -
 SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o
SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o -
 The fluorescent hum of the server room felt louder than usual that Tuesday night as I stared at the intrusion detection alerts flashing crimson across three monitors. My palms left damp streaks on the keyboard - some script kiddie had bypassed our legacy chat system like it was tissue paper. Client contracts, architectural schematics, everything vulnerable. That's when my fingers flew to Rocket.Chat's desktop icon, the self-hosted version we'd migrated to just weeks prior.
The fluorescent hum of the server room felt louder than usual that Tuesday night as I stared at the intrusion detection alerts flashing crimson across three monitors. My palms left damp streaks on the keyboard - some script kiddie had bypassed our legacy chat system like it was tissue paper. Client contracts, architectural schematics, everything vulnerable. That's when my fingers flew to Rocket.Chat's desktop icon, the self-hosted version we'd migrated to just weeks prior. -
 That gut-twisting ping echoed at 3 AM again—another Slack notification lighting up my phone like a burglar alarm. I’d been here before: hunched over my laptop in the suffocating dark, heart jackhammering against my ribs as I imagined client contracts bleeding into hacker forums. Last year’s breach cost me six figures and a reputation I’d built over a decade. Now, handling merger blueprints for a biotech startup, every message felt like tossing confidential documents into a public dumpster. My fi
That gut-twisting ping echoed at 3 AM again—another Slack notification lighting up my phone like a burglar alarm. I’d been here before: hunched over my laptop in the suffocating dark, heart jackhammering against my ribs as I imagined client contracts bleeding into hacker forums. Last year’s breach cost me six figures and a reputation I’d built over a decade. Now, handling merger blueprints for a biotech startup, every message felt like tossing confidential documents into a public dumpster. My fi -
 The metallic taste of fear flooded my mouth when my therapist's office called. "Your online research triggered our security alerts," the receptionist whispered. My fingertips turned icy as I realized my midnight searches about dissociative disorders weren't private - they'd become corporate commodities. That night I tore through privacy forums until dawn, desperation souring my throat, until I found it: OrNET. Not a browser. A digital panic room.
The metallic taste of fear flooded my mouth when my therapist's office called. "Your online research triggered our security alerts," the receptionist whispered. My fingertips turned icy as I realized my midnight searches about dissociative disorders weren't private - they'd become corporate commodities. That night I tore through privacy forums until dawn, desperation souring my throat, until I found it: OrNET. Not a browser. A digital panic room. -
 Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp
Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp -
 That third flat white was buzzing through my veins when I spotted the attachment icon blinking on my phone - right before hitting send on a proposal containing acquisition targets. Public coffee shop Wi-Fi suddenly felt like broadcasting on Times Square billboards. My thumb hovered over the screen, slick with cold sweat as I imagined competitors intercepting those unencrypted figures. Every notification chime from neighboring laptops sounded like a data breach alarm.
That third flat white was buzzing through my veins when I spotted the attachment icon blinking on my phone - right before hitting send on a proposal containing acquisition targets. Public coffee shop Wi-Fi suddenly felt like broadcasting on Times Square billboards. My thumb hovered over the screen, slick with cold sweat as I imagined competitors intercepting those unencrypted figures. Every notification chime from neighboring laptops sounded like a data breach alarm. -
 Truple - Online AccountabilityWith Truple you can virtually "peek" over your child's shoulder & course-correct as needed. Whether its pornography, sexting, cyber-bullying, violence or excessive screen time, Truple will help you detect it early so you can prevent and fix issues before they turn into
Truple - Online AccountabilityWith Truple you can virtually "peek" over your child's shoulder & course-correct as needed. Whether its pornography, sexting, cyber-bullying, violence or excessive screen time, Truple will help you detect it early so you can prevent and fix issues before they turn into -
 Flussonic WatcherMobile client for real time access to Flussonic Watcher video surveillanceIn this app you can:* Watch live video from IP cameras with the ultra low latency and secure TLS encryption* Browse camera's archive at any permitted depth* View your cameras on the map* View your cameras in t
Flussonic WatcherMobile client for real time access to Flussonic Watcher video surveillanceIn this app you can:* Watch live video from IP cameras with the ultra low latency and secure TLS encryption* Browse camera's archive at any permitted depth* View your cameras on the map* View your cameras in t -
 EseeCloud(IP Pro, VR Cam)Only support installation and use after Android system 5.1EseeCloud(IP Pro, VR Cam) is a simple, stylish, user-friendly and powerful mobile video surveillance software. We are committed to continuously improving our video processing technology and video innovation technology, and providing global security products, professional industry solutions and superior services to continuously create greater practical value for our customers.
EseeCloud(IP Pro, VR Cam)Only support installation and use after Android system 5.1EseeCloud(IP Pro, VR Cam) is a simple, stylish, user-friendly and powerful mobile video surveillance software. We are committed to continuously improving our video processing technology and video innovation technology, and providing global security products, professional industry solutions and superior services to continuously create greater practical value for our customers. -
 E-SAN VPNWhat are the capabilities of our E-SAN VPN application?\xe2\x80\xa2 There are a variety of servers to choose from.\xe2\x80\xa2 Can access our application at any time.\xe2\x80\xa2 Access and we will not record your usage history.\xe2\x80\xa2 Access content on restricted websites.* Why use th
E-SAN VPNWhat are the capabilities of our E-SAN VPN application?\xe2\x80\xa2 There are a variety of servers to choose from.\xe2\x80\xa2 Can access our application at any time.\xe2\x80\xa2 Access and we will not record your usage history.\xe2\x80\xa2 Access content on restricted websites.* Why use th
