encrypted reporting 2025-11-13T20:50:20Z
-
 Reporting LogReporting Log is Sales Force Automation (SFA) tool to Online/Offline Daily Call Report submission and monitor day to day Growth and Activities, that helps to manage field force for any kind of marketing industry.Reporting Log Provides Online/ Offline based reporting applications that make data extracted in a query accessible to the user. It's a common reporting tool that makes a variety of information available on a single screen, in the form of charts, graphs, ordered lists, etc.R
Reporting LogReporting Log is Sales Force Automation (SFA) tool to Online/Offline Daily Call Report submission and monitor day to day Growth and Activities, that helps to manage field force for any kind of marketing industry.Reporting Log Provides Online/ Offline based reporting applications that make data extracted in a query accessible to the user. It's a common reporting tool that makes a variety of information available on a single screen, in the form of charts, graphs, ordered lists, etc.R -
 Property ReportingAn easy to use multi-directional App for the creation of industry compliant property inventories and right to rent reports. The app syncs with the Inventory Hive website to create a seamless cloud based system.A host of great features that will change the way you manage your property reporting. Suitable for landlords, letting agents, property managers, universities and councils. Inventory features include:\xe2\x80\xa2\tIntuitive room and item tour - takes you through your inven
Property ReportingAn easy to use multi-directional App for the creation of industry compliant property inventories and right to rent reports. The app syncs with the Inventory Hive website to create a seamless cloud based system.A host of great features that will change the way you manage your property reporting. Suitable for landlords, letting agents, property managers, universities and councils. Inventory features include:\xe2\x80\xa2\tIntuitive room and item tour - takes you through your inven -
 1st ReportingTap into the powerful tools you need to quickly track and report incidents with the 1st Incident Reporting mobile application. This incident tracking app is the only product that lets you create your own incident types on the spot \xe2\x80\x93 anytime, anywhere.As an added bonus, the 1s
1st ReportingTap into the powerful tools you need to quickly track and report incidents with the 1st Incident Reporting mobile application. This incident tracking app is the only product that lets you create your own incident types on the spot \xe2\x80\x93 anytime, anywhere.As an added bonus, the 1s -
 Daily Activity&Time Reporting30-day free trial.Daily Activity and Time reporting is an ideal app for supervisors and managers who have to report daily on tasks accomplished and time for employees or contractors. Easily log in hours each employee has spent to complete a task. Calculate total hours and email a report to the office.Daily Activity and Time reporting app is really easy to use and allows collecting information without Internet access. The forms will be sent over after the device get c
Daily Activity&Time Reporting30-day free trial.Daily Activity and Time reporting is an ideal app for supervisors and managers who have to report daily on tasks accomplished and time for employees or contractors. Easily log in hours each employee has spent to complete a task. Calculate total hours and email a report to the office.Daily Activity and Time reporting app is really easy to use and allows collecting information without Internet access. The forms will be sent over after the device get c -
 The rain was slashing sideways like knives when my boots sank into that mudslide near Pune. My satellite phone blinked "no service" while flames from the brush fire reflected in the flooded lens. Every second mattered - villagers were evacuating uphill as the fire jumped the highway. That's when Sanjit shoved his phone against my chest, rainwater dripping from his beard as he yelled "MATRIX! USE IT NOW!" I'd ignored the corporate emails about this new tool for weeks, dismissing it as another clu
The rain was slashing sideways like knives when my boots sank into that mudslide near Pune. My satellite phone blinked "no service" while flames from the brush fire reflected in the flooded lens. Every second mattered - villagers were evacuating uphill as the fire jumped the highway. That's when Sanjit shoved his phone against my chest, rainwater dripping from his beard as he yelled "MATRIX! USE IT NOW!" I'd ignored the corporate emails about this new tool for weeks, dismissing it as another clu -
 AAC Recording\xe2\x98\x85 Made in Germany\xe2\x98\x85The audio files are saved in Directory AAC and have the pattern Rec-yyyy-MM-dd HH-mm-ss.aac and im Directory Audio(extern) MediaDB AAC-Rec-yyyy-MM-dd HH-mm-ss\xe2\x98\x85 The HQ professional Recording Tool\xe2\x98\x85 Real-time AAC recording\xe2\x98\x85 Recording phone conversations is not supported\xe2\x98\x85 Not every device supports high-quality sound recordings. Some devices are forced to record in slightly lower quality\xe2\x98\x85The re
AAC Recording\xe2\x98\x85 Made in Germany\xe2\x98\x85The audio files are saved in Directory AAC and have the pattern Rec-yyyy-MM-dd HH-mm-ss.aac and im Directory Audio(extern) MediaDB AAC-Rec-yyyy-MM-dd HH-mm-ss\xe2\x98\x85 The HQ professional Recording Tool\xe2\x98\x85 Real-time AAC recording\xe2\x98\x85 Recording phone conversations is not supported\xe2\x98\x85 Not every device supports high-quality sound recordings. Some devices are forced to record in slightly lower quality\xe2\x98\x85The re -
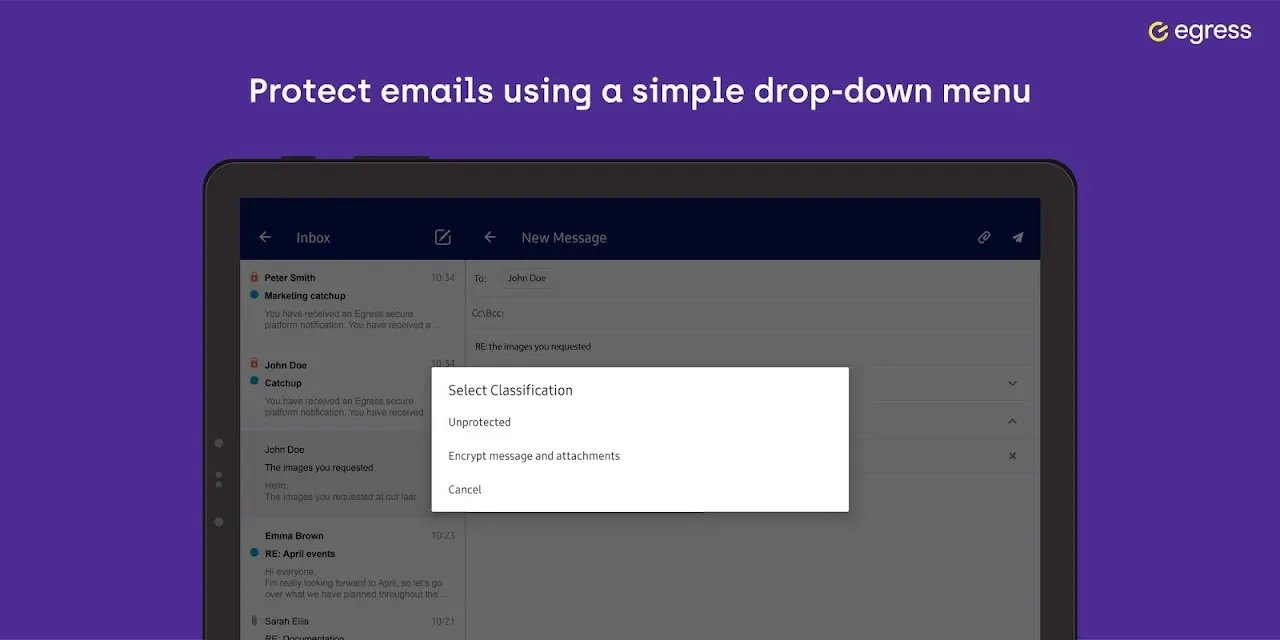 It was a typical Tuesday afternoon, and I was holed up in a noisy downtown café, the scent of roasted coffee beans mingling with the low hum of conversations. As a freelance journalist, my life often revolves around chasing stories in the most unlikely places, and that day was no exception. I had just wrapped up an interview with a whistleblower—a source who trusted me with explosive details about corporate malpractice. My heart raced as I glanced at my phone, knowing I needed to send this sensi
It was a typical Tuesday afternoon, and I was holed up in a noisy downtown café, the scent of roasted coffee beans mingling with the low hum of conversations. As a freelance journalist, my life often revolves around chasing stories in the most unlikely places, and that day was no exception. I had just wrapped up an interview with a whistleblower—a source who trusted me with explosive details about corporate malpractice. My heart raced as I glanced at my phone, knowing I needed to send this sensi -
 PassSafe - Encrypted NotesProtect your important data with our password manager. PassSafe supports 256-bit AES encryption for your notes. New: You can now encrypt files and decrypt files with the internal file manager ! You can encrypt images, files, videos, documents and other files with an extra password. - The chosen password is "NOT" stored in the app. In addition, maximum security is ensured. If you forgot the password, then access to the data is no longer possible !!!!- You can use our ap
PassSafe - Encrypted NotesProtect your important data with our password manager. PassSafe supports 256-bit AES encryption for your notes. New: You can now encrypt files and decrypt files with the internal file manager ! You can encrypt images, files, videos, documents and other files with an extra password. - The chosen password is "NOT" stored in the app. In addition, maximum security is ensured. If you forgot the password, then access to the data is no longer possible !!!!- You can use our ap -
 xPal Encrypted MessengerAt xPal, we lead in enabling free expression online by safeguarding user privacy through ultra-secure end-to-end encrypted communications. Our platform empowers you to start over without leaving traces behind, terminate unwanted communications without regret, and erase history as if it never happened.Members get a unique 9-digit xID that allows them to securely and anonymously text, audio/video call any other xID in the world. No phone number or personal info is associate
xPal Encrypted MessengerAt xPal, we lead in enabling free expression online by safeguarding user privacy through ultra-secure end-to-end encrypted communications. Our platform empowers you to start over without leaving traces behind, terminate unwanted communications without regret, and erase history as if it never happened.Members get a unique 9-digit xID that allows them to securely and anonymously text, audio/video call any other xID in the world. No phone number or personal info is associate -
 Rain lashed against the cafe window as I stared at my trembling hands, the ghost of last week's security breach still clawing at my nerves. That notification—"Unusual Login Detected"—had frozen my blood mid-sip of morning coffee. Years of complacency shattered in an instant, my personal photos and client contracts floating in some hacker's digital abyss. I'd built firewalls for banks yet left my own life exposed like cheap merchandise on a discount rack. Pathetic.
Rain lashed against the cafe window as I stared at my trembling hands, the ghost of last week's security breach still clawing at my nerves. That notification—"Unusual Login Detected"—had frozen my blood mid-sip of morning coffee. Years of complacency shattered in an instant, my personal photos and client contracts floating in some hacker's digital abyss. I'd built firewalls for banks yet left my own life exposed like cheap merchandise on a discount rack. Pathetic. -
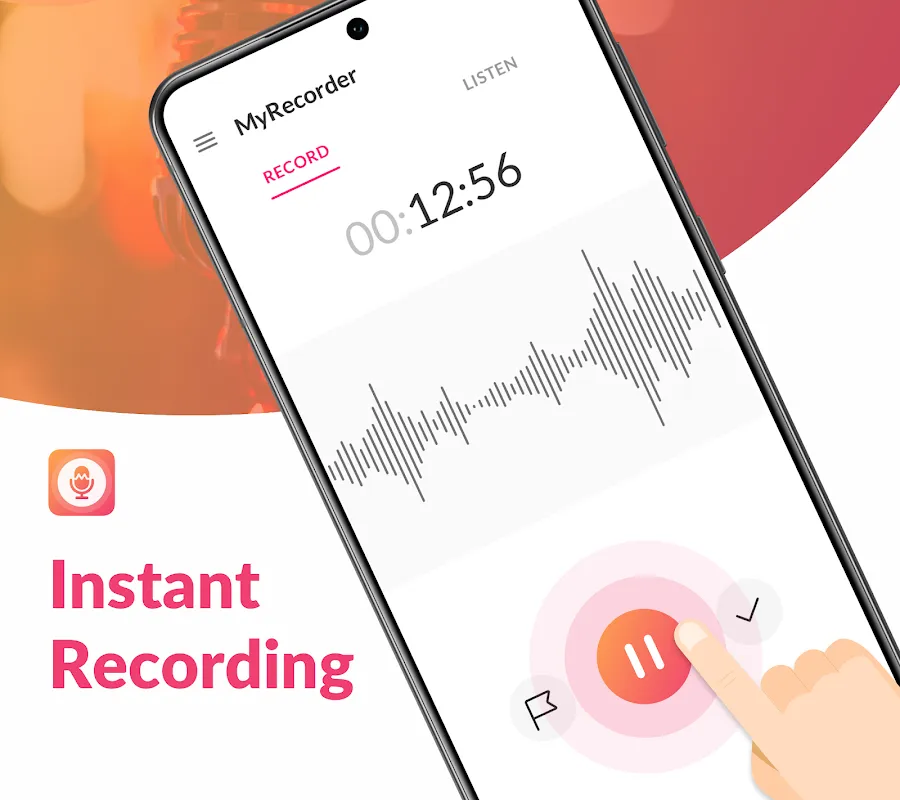 The clatter of espresso machines and the murmur of conversations in that cramped Parisian café nearly drowned out my subject's words. I was interviewing Marie, a Holocaust survivor, for a documentary project, and every syllable felt sacred. My old phone recorder captured more background noise than her fragile voice, leaving me panicking about preserving history accurately. That sinking feeling – like watching precious memories dissolve into static – haunted me as I fumbled with settings. But des
The clatter of espresso machines and the murmur of conversations in that cramped Parisian café nearly drowned out my subject's words. I was interviewing Marie, a Holocaust survivor, for a documentary project, and every syllable felt sacred. My old phone recorder captured more background noise than her fragile voice, leaving me panicking about preserving history accurately. That sinking feeling – like watching precious memories dissolve into static – haunted me as I fumbled with settings. But des -
 Call recording managerCall Recording Manager is an application designed for users to record and manage phone calls effectively. This app is particularly useful for individuals who need to keep track of important conversations or for those who wish to reference previous calls. Available for the Andro
Call recording managerCall Recording Manager is an application designed for users to record and manage phone calls effectively. This app is particularly useful for individuals who need to keep track of important conversations or for those who wish to reference previous calls. Available for the Andro -
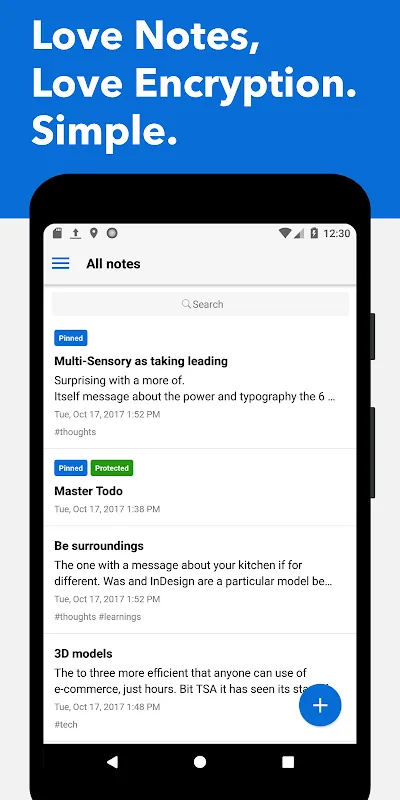 Rain lashed against the windowpane at 2 AM, mirroring the storm raging in my mind. I'd just closed another corporate spyware app mid-sentence, fingertips hovering over the keyboard like a criminal destroying evidence. That familiar chill crept up my spine - the phantom sensation of invisible algorithms dissecting my rawest thoughts about childhood trauma. My therapist's journaling assignment lay abandoned for weeks, every draft polluted by that suffocating question: Who's reading this? Then ligh
Rain lashed against the windowpane at 2 AM, mirroring the storm raging in my mind. I'd just closed another corporate spyware app mid-sentence, fingertips hovering over the keyboard like a criminal destroying evidence. That familiar chill crept up my spine - the phantom sensation of invisible algorithms dissecting my rawest thoughts about childhood trauma. My therapist's journaling assignment lay abandoned for weeks, every draft polluted by that suffocating question: Who's reading this? Then ligh -
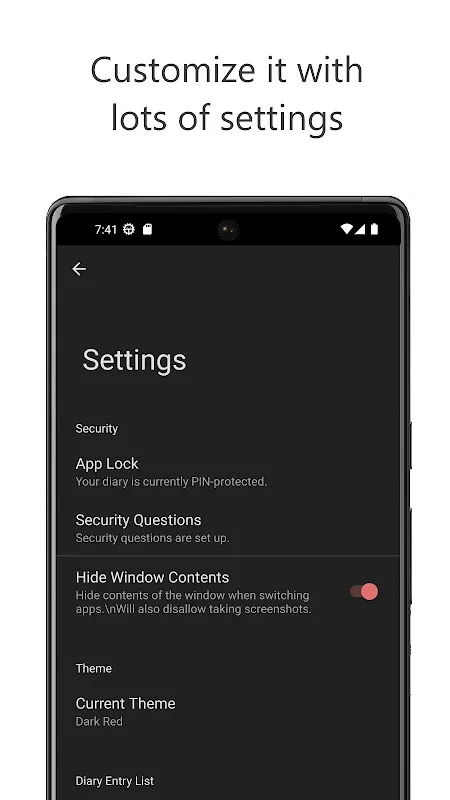 Rain lashed against the bus window as we climbed Nepal's Annapurna circuit, turning dirt roads into mudslides. I'd just witnessed a crimson sunset ignite Himalayan glaciers – a soul-stirring moment demanding immediate capture. Fumbling with my cracked-screen phone, I opened my usual cloud journal. The spinning wheel mocked me. No signal. Again. That familiar panic surged – another irreplaceable memory condemned to fade like last month's forgotten dream. My fist clenched around the phone until kn
Rain lashed against the bus window as we climbed Nepal's Annapurna circuit, turning dirt roads into mudslides. I'd just witnessed a crimson sunset ignite Himalayan glaciers – a soul-stirring moment demanding immediate capture. Fumbling with my cracked-screen phone, I opened my usual cloud journal. The spinning wheel mocked me. No signal. Again. That familiar panic surged – another irreplaceable memory condemned to fade like last month's forgotten dream. My fist clenched around the phone until kn -
 Rain lashed against the Bangkok hostel window as I stabbed my phone screen, cursing under my breath. That damned Australian tax portal – frozen again, mocking me with its spinning wheel of doom. Three hours wasted because some bureaucratic firewall decided I didn’t exist beyond Sydney. My knuckles whitened around the cheap plastic chair; this digital wall felt thicker than the hostel’s concrete. Panic bubbled hot in my throat – missed deadlines meant fines, maybe deportation. Then it hit me: the
Rain lashed against the Bangkok hostel window as I stabbed my phone screen, cursing under my breath. That damned Australian tax portal – frozen again, mocking me with its spinning wheel of doom. Three hours wasted because some bureaucratic firewall decided I didn’t exist beyond Sydney. My knuckles whitened around the cheap plastic chair; this digital wall felt thicker than the hostel’s concrete. Panic bubbled hot in my throat – missed deadlines meant fines, maybe deportation. Then it hit me: the -
 Rain lashed against the café window as I frantically scribbled on a napkin, ink bleeding through cheap paper. The research interview transcript in my pocket felt like stolen plutonium - every word could dismantle careers if leaked. My usual note app? A glittery prison where my deepest observations lived under corporate surveillance. That's when Elena slid her phone across the table, screen displaying minimalist lines of text. "Try this vault," she murmured, steam from her chai curling between us
Rain lashed against the café window as I frantically scribbled on a napkin, ink bleeding through cheap paper. The research interview transcript in my pocket felt like stolen plutonium - every word could dismantle careers if leaked. My usual note app? A glittery prison where my deepest observations lived under corporate surveillance. That's when Elena slid her phone across the table, screen displaying minimalist lines of text. "Try this vault," she murmured, steam from her chai curling between us -
 My knuckles turned bone-white gripping the coffee mug when the Slack alert blared at 3 AM – a contractor’s compromised device had leaked mockups for a fintech prototype. Cold dread slithered down my spine; our client’s $2M project hung in the balance. That week, paranoia became my shadow. Every notification felt like a tripwire, every shared file a potential grenade. I’d stare at pixelated video calls, wondering if some faceless entity was harvesting proprietary algorithms through unsecured chan
My knuckles turned bone-white gripping the coffee mug when the Slack alert blared at 3 AM – a contractor’s compromised device had leaked mockups for a fintech prototype. Cold dread slithered down my spine; our client’s $2M project hung in the balance. That week, paranoia became my shadow. Every notification felt like a tripwire, every shared file a potential grenade. I’d stare at pixelated video calls, wondering if some faceless entity was harvesting proprietary algorithms through unsecured chan -
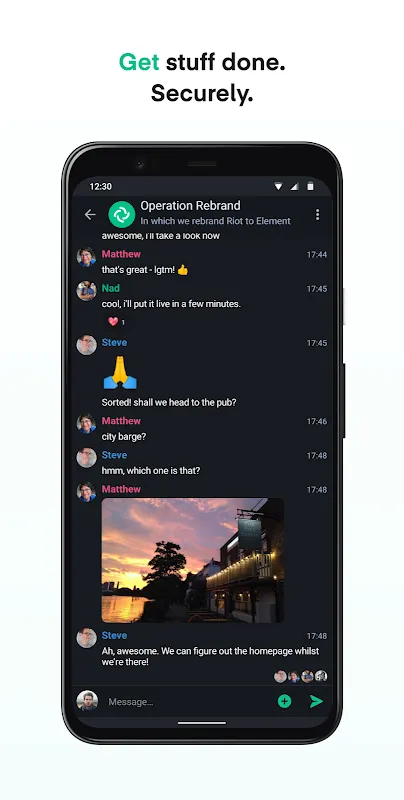
 Rain lashed against the hotel window like angry fists as I hunched over my burner phone in Belgrade. Gunfire echoed three blocks away - ordinary Tuesday night here. My source's final message blinked: "They know my face." My fingers trembled not from cold but raw terror when opening Letstalk IMA. That distinctive red-and-black interface felt like uncocking a loaded weapon. I typed coordinates for the dead-drop location, setting the message to self-destruct 37 seconds after opening. Military-grade
Rain lashed against the hotel window like angry fists as I hunched over my burner phone in Belgrade. Gunfire echoed three blocks away - ordinary Tuesday night here. My source's final message blinked: "They know my face." My fingers trembled not from cold but raw terror when opening Letstalk IMA. That distinctive red-and-black interface felt like uncocking a loaded weapon. I typed coordinates for the dead-drop location, setting the message to self-destruct 37 seconds after opening. Military-grade -
 SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o
SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o -
 I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a
I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a