encrypted workflows 2025-11-06T06:53:14Z
-
 Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv.
Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv. -
 The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima
The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima -
 Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw
Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw -
 Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious
Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious -
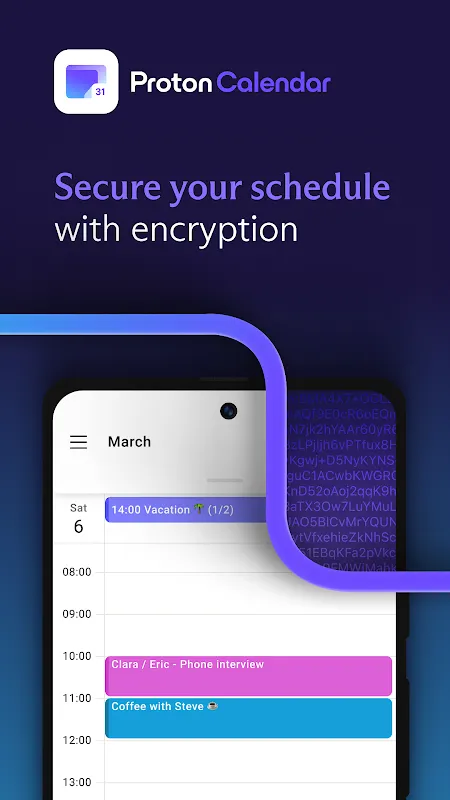 The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality.
The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality. -
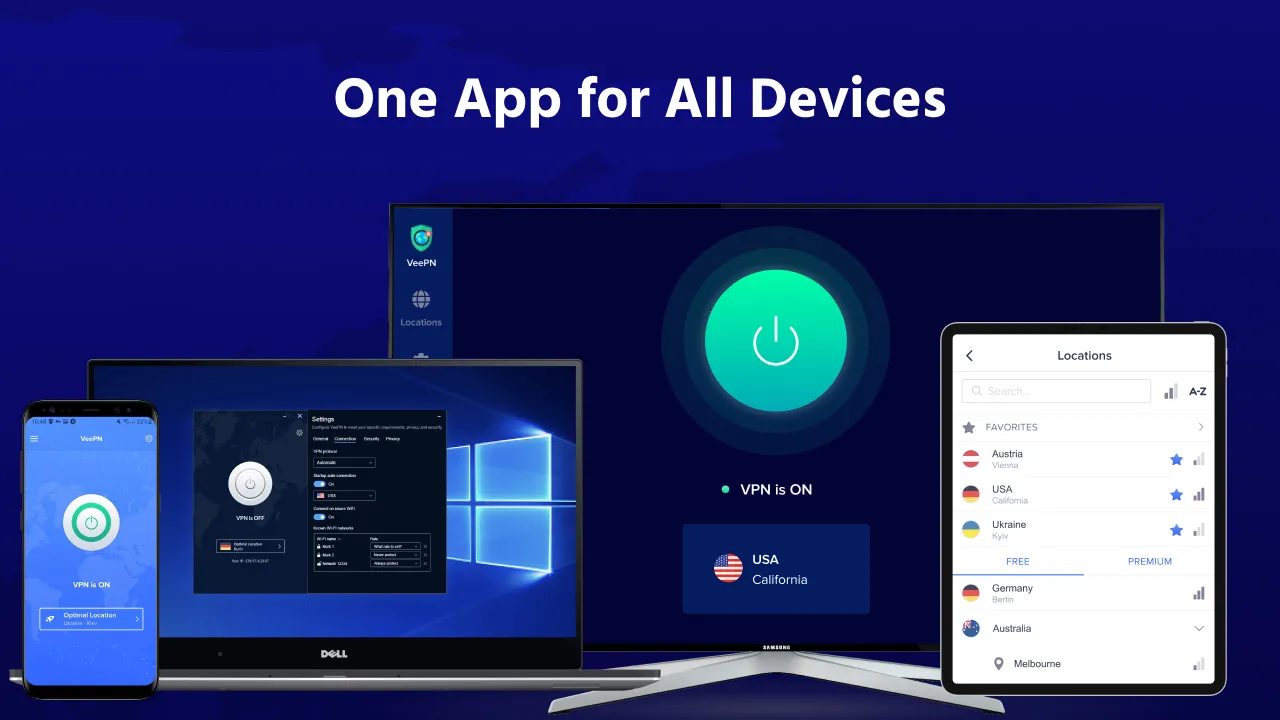 Rain lashed against the Istanbul airport windows as I hunched over my laptop, fingers trembling. That Pulitzer-chasing exposé on my screen? Worthless if intercepted. Public Wi-Fi networks here felt like digital minefields - every byte transmitted might as well be broadcast on Times Square billboards. I'd witnessed a colleague's career implode when state-sponsored hackers intercepted his research in Minsk. Now history threatened to repeat itself with this breaking story about offshore shell compa
Rain lashed against the Istanbul airport windows as I hunched over my laptop, fingers trembling. That Pulitzer-chasing exposé on my screen? Worthless if intercepted. Public Wi-Fi networks here felt like digital minefields - every byte transmitted might as well be broadcast on Times Square billboards. I'd witnessed a colleague's career implode when state-sponsored hackers intercepted his research in Minsk. Now history threatened to repeat itself with this breaking story about offshore shell compa -
 Rain lashed against the cafe window as I frantically swiped through my gallery, stomach churning. There it was - yesterday's street art photo, innocently shared online, now broadcasting the exact alley where I'd met my whistleblower source. The embedded GPS coordinates glared back like digital betrayal. In that humid panic, I finally understood how metadata turns cameras into snitches.
Rain lashed against the cafe window as I frantically swiped through my gallery, stomach churning. There it was - yesterday's street art photo, innocently shared online, now broadcasting the exact alley where I'd met my whistleblower source. The embedded GPS coordinates glared back like digital betrayal. In that humid panic, I finally understood how metadata turns cameras into snitches. -
 Rain lashed against the Bangkok guesthouse window as my fingers trembled over the keyboard. Three days. Seventy-two hours since the local government flipped the kill switch on international news portals, and my investigative piece about cross-border data trafficking was trapped in digital purgatory. Each "connection timed out" error felt like a padlock snapping shut. That's when I remembered the whisper from a cybersecurity contact: "If you truly own nothing, at least own your tunnel." The Clic
Rain lashed against the Bangkok guesthouse window as my fingers trembled over the keyboard. Three days. Seventy-two hours since the local government flipped the kill switch on international news portals, and my investigative piece about cross-border data trafficking was trapped in digital purgatory. Each "connection timed out" error felt like a padlock snapping shut. That's when I remembered the whisper from a cybersecurity contact: "If you truly own nothing, at least own your tunnel." The Clic -
 My palms left sweaty smudges on the tablet screen as I frantically tapped the frozen airline check-in page. Gate agents began final boarding calls while the cursed "processing" spinner mocked me from within the travel app. That moment – stranded at JFK with my luggage halfway to London – was my breaking point with in-app browsers. Little did I know salvation came disguised as Android System WebView Beta, a tool I'd previously dismissed as developer arcana.
My palms left sweaty smudges on the tablet screen as I frantically tapped the frozen airline check-in page. Gate agents began final boarding calls while the cursed "processing" spinner mocked me from within the travel app. That moment – stranded at JFK with my luggage halfway to London – was my breaking point with in-app browsers. Little did I know salvation came disguised as Android System WebView Beta, a tool I'd previously dismissed as developer arcana. -
 The fluorescent hum of the server room felt louder than usual that Tuesday night as I stared at the intrusion detection alerts flashing crimson across three monitors. My palms left damp streaks on the keyboard - some script kiddie had bypassed our legacy chat system like it was tissue paper. Client contracts, architectural schematics, everything vulnerable. That's when my fingers flew to Rocket.Chat's desktop icon, the self-hosted version we'd migrated to just weeks prior.
The fluorescent hum of the server room felt louder than usual that Tuesday night as I stared at the intrusion detection alerts flashing crimson across three monitors. My palms left damp streaks on the keyboard - some script kiddie had bypassed our legacy chat system like it was tissue paper. Client contracts, architectural schematics, everything vulnerable. That's when my fingers flew to Rocket.Chat's desktop icon, the self-hosted version we'd migrated to just weeks prior. -
 That gut-twisting ping echoed at 3 AM again—another Slack notification lighting up my phone like a burglar alarm. I’d been here before: hunched over my laptop in the suffocating dark, heart jackhammering against my ribs as I imagined client contracts bleeding into hacker forums. Last year’s breach cost me six figures and a reputation I’d built over a decade. Now, handling merger blueprints for a biotech startup, every message felt like tossing confidential documents into a public dumpster. My fi
That gut-twisting ping echoed at 3 AM again—another Slack notification lighting up my phone like a burglar alarm. I’d been here before: hunched over my laptop in the suffocating dark, heart jackhammering against my ribs as I imagined client contracts bleeding into hacker forums. Last year’s breach cost me six figures and a reputation I’d built over a decade. Now, handling merger blueprints for a biotech startup, every message felt like tossing confidential documents into a public dumpster. My fi -
 The metallic taste of fear flooded my mouth when my therapist's office called. "Your online research triggered our security alerts," the receptionist whispered. My fingertips turned icy as I realized my midnight searches about dissociative disorders weren't private - they'd become corporate commodities. That night I tore through privacy forums until dawn, desperation souring my throat, until I found it: OrNET. Not a browser. A digital panic room.
The metallic taste of fear flooded my mouth when my therapist's office called. "Your online research triggered our security alerts," the receptionist whispered. My fingertips turned icy as I realized my midnight searches about dissociative disorders weren't private - they'd become corporate commodities. That night I tore through privacy forums until dawn, desperation souring my throat, until I found it: OrNET. Not a browser. A digital panic room. -
 Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp
Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp -
 The espresso machine hissed like an angry cat as I balanced my phone between cheek and shoulder, fingers sticky with syrup from breakfast pancakes. "Can you resend that Slack file?" my manager's voice crackled through Bluetooth while Google Maps blinked urgently about an upcoming turn. In that suspended chaos moment, my thumb fumbled across the screen like a drunk spider - app icons blurring into meaningless colored dots. That's when the delivery notification popped up, obscuring the navigation.
The espresso machine hissed like an angry cat as I balanced my phone between cheek and shoulder, fingers sticky with syrup from breakfast pancakes. "Can you resend that Slack file?" my manager's voice crackled through Bluetooth while Google Maps blinked urgently about an upcoming turn. In that suspended chaos moment, my thumb fumbled across the screen like a drunk spider - app icons blurring into meaningless colored dots. That's when the delivery notification popped up, obscuring the navigation. -
 GOLGOL is a business optimization application developed by OUTLiNK that aims to enhance the performance of various business operations. Known for its capacity to streamline and automate procedures, GOL serves as a comprehensive tool for organizations seeking to improve efficiency and productivity. T
GOLGOL is a business optimization application developed by OUTLiNK that aims to enhance the performance of various business operations. Known for its capacity to streamline and automate procedures, GOL serves as a comprehensive tool for organizations seeking to improve efficiency and productivity. T -
 KeePassVaultClient app for KeePass databases.This app is orientated for my personal use. It may have some bugs, so please make a backup before use it.Features:- Synchronization with WebDav server or Git (HTTPS only, SSH protocol is not available) repository- Create databases, entries and groups- Password or key file unlock- Supports .kdbx files up to version 4.1- Dynamic templates (compatible with other android applications: KeePassDX, keepass2android)- Biometric unlock- Autofill for Android >=
KeePassVaultClient app for KeePass databases.This app is orientated for my personal use. It may have some bugs, so please make a backup before use it.Features:- Synchronization with WebDav server or Git (HTTPS only, SSH protocol is not available) repository- Create databases, entries and groups- Password or key file unlock- Supports .kdbx files up to version 4.1- Dynamic templates (compatible with other android applications: KeePassDX, keepass2android)- Biometric unlock- Autofill for Android >= -
 TchapTchap is an instant messaging service intended for communications by French administration agents, to exchange information on the move or from an office workstation. Tchap allows you to chat via messages in pairs and in groups, and to share files like any instant messenger, with an integrated directory of user agents, simultaneous use on several devices and confidentiality of private exchanges.Agents can invite outsiders into a professional conversation.The app requires the USE_FULL_SCREEN_
TchapTchap is an instant messaging service intended for communications by French administration agents, to exchange information on the move or from an office workstation. Tchap allows you to chat via messages in pairs and in groups, and to share files like any instant messenger, with an integrated directory of user agents, simultaneous use on several devices and confidentiality of private exchanges.Agents can invite outsiders into a professional conversation.The app requires the USE_FULL_SCREEN_


