geolayered encryption 2025-11-01T03:04:03Z
-
 The drizzle blurred my train window into a watercolor smear of grays and greens, that familiar numbness creeping into my bones. Another soul-crushing commute. I fumbled with my phone, thumb hovering over mindless puzzle games – digital pacifiers for the terminally bored. Then I tapped Project VOID's jagged eye icon. Within minutes, I was sprinting through Hammersmith Station, rain soaking my collar, because a pigeon's feather stuck to a wet bench wasn't debris. It was evidence.
The drizzle blurred my train window into a watercolor smear of grays and greens, that familiar numbness creeping into my bones. Another soul-crushing commute. I fumbled with my phone, thumb hovering over mindless puzzle games – digital pacifiers for the terminally bored. Then I tapped Project VOID's jagged eye icon. Within minutes, I was sprinting through Hammersmith Station, rain soaking my collar, because a pigeon's feather stuck to a wet bench wasn't debris. It was evidence. -
 The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore.
The glow of my laptop screen felt like an interrogation lamp that night. I'd been chasing a data breach trace for hours, sweat trickling down my neck as I realized my usual email client had been silently broadcasting my search patterns. That's when I remembered the Swiss invitation buried in my spam folder weeks earlier - some privacy-focused service called Infomaniak. Desperation makes you try things you'd normally ignore. -
 AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil
AES Encryption (256-Bit)Encryption is a way of protecting your files with a password. This application encrypts your files using 256-Bit AES Encryption Protocol so it would take someone using a brute force attack around "2.29*10^32 years" to unlock your file. In short, it's one of the best encryptions out there.With this app, you can encrypt your files in these simple steps.- Choose a file or multiple files at once- Enter a password- Wait for the encryption/decryption to complete- Your files wil -
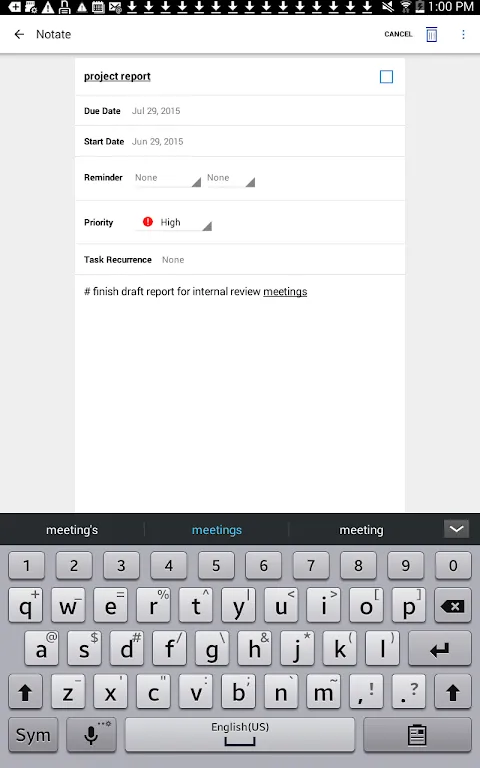 Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor
Rain lashed against the lodge windows like angry spirits as I stared at the financial projections glowing on my BlackBerry. Three hours from civilization, with only a dying generator humming in protest against the storm, and I'd just spotted the lethal typo - a misplaced decimal point that could vaporize our startup's valuation. My fingers trembled not from the alpine chill seeping through log walls, but from the realization that our entire funding round balanced on editing this cursed PDF befor -
 SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o
SSE - File & Text EncryptionSecret Space Encryptor (S.S.E.)File Encryption, Text Encryption and Password Manager applications integrated into the all-in-one solution. Important Introductory Note:This application provides many options and is intended for experienced users. All data are really encrypted (mathematically altered) using keys derived from your password. If you forget the password, your data is lost no matter how many vulgar insults you send to our e-mail. The correct password is the o -
 eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa
eScription OneeScription One allows authorized clinicians to create and manage high quality documentation for an EMR with minimal time and effort. Clinicians dictate the narrative and keep pace with busy patient loads without compromising time with patients, revenue potential or length of workday. Meanwhile, timely, complete, structured data in the EMR reduces claim rejections, decreases time to bill and enhances compliance.A real-time schedule feed serves as a daily work list while access to pa -
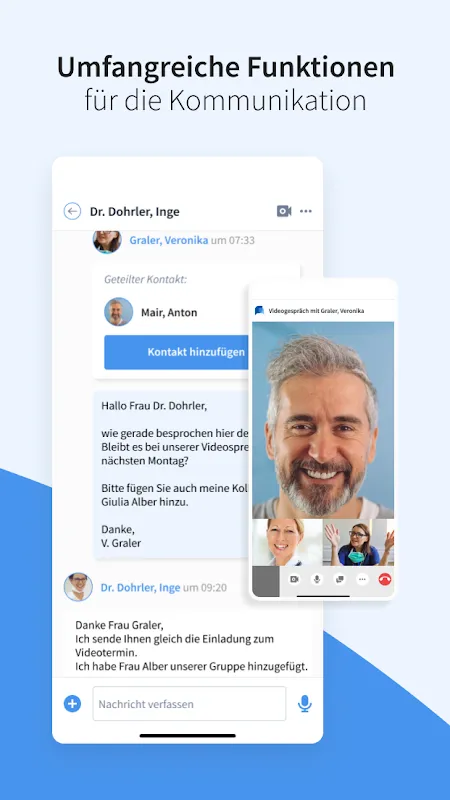 Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res
Rain lashed against the window as I stared at the glucose monitor's blinking red numbers - 387 mg/dL. Midnight. Alone. That familiar metallic taste of panic flooded my mouth as I fumbled for my endocrinologist's after-hours number. Three rings. Voicemail. Again. My trembling fingers left a sweaty smear on the phone screen when Sarah's text suddenly appeared: "Download that healthcare comms thingy yet? Screenshot attached." The logo glared back: a blue shield with a white heartbeat line. Last res -
 Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f
Rain lashed against the hotel window in Prague as I stared at the encrypted email confirmation, fingers trembling. The client's prototype schematics sat in my cloud drive – blueprints that could bankrupt my firm if intercepted. Earlier that morning, a panicked call from headquarters revealed our usual file transfer service had been compromised; competitors were circling like sharks. My throat tightened with every notification ping. That's when I remembered the unassuming icon buried in my apps f -
 Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m
Sweat pooled beneath my collar as the phone rang for the seventh consecutive morning. That infuriating robotic hold music had become the soundtrack to my tachycardia - a cruel joke reminding me how my own pulse mocked me while specialists remained untouchable. Each dropped call felt like betrayal; each voicemail a black hole swallowing my panic. My cardiologist's office might as well have been on Mars. Then came Tuesday's tuna salad lunch with Sarah, who watched me stab lettuce like it owed me m -
 EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me
EncoderOur app provides a number of encryption methods to ensure the security of your messages and data . Thanks to our user-friendly interface, you can easily encrypt and decrypt texts using various encryption methods.Main Features:Keyword-based encryption: Encrypt your messages with a keyword, adding an extra layer of security.Decryption of keywords: Easily decipher messages using the keyword.Encryption: Encrypt texts without using a keyword, ensuring the user's privacy.Transcripts: Decrypt me -
 Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp
Encrypt Messages And TextEncrypt Messages And Text is a mobile application designed to secure communications by encrypting messages, sensitive information, notes, and passwords. This app is particularly relevant for users who prioritize privacy and seek to protect their data from unauthorized access. Available for the Android platform, users can download Encrypt Messages And Text to enhance the confidentiality of their communications.The app utilizes the AES/CBC/PKCS5Padding algorithm for encryp -
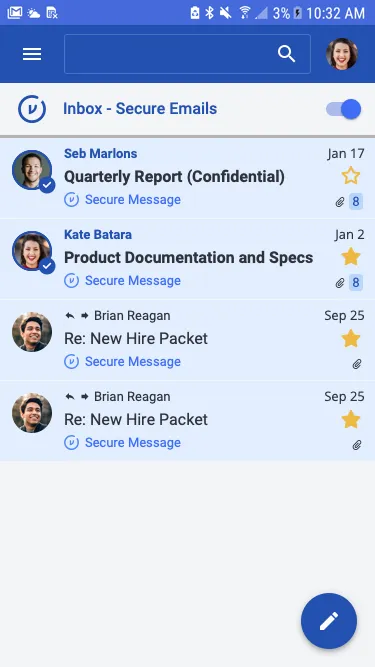 That third flat white was buzzing through my veins when I spotted the attachment icon blinking on my phone - right before hitting send on a proposal containing acquisition targets. Public coffee shop Wi-Fi suddenly felt like broadcasting on Times Square billboards. My thumb hovered over the screen, slick with cold sweat as I imagined competitors intercepting those unencrypted figures. Every notification chime from neighboring laptops sounded like a data breach alarm.
That third flat white was buzzing through my veins when I spotted the attachment icon blinking on my phone - right before hitting send on a proposal containing acquisition targets. Public coffee shop Wi-Fi suddenly felt like broadcasting on Times Square billboards. My thumb hovered over the screen, slick with cold sweat as I imagined competitors intercepting those unencrypted figures. Every notification chime from neighboring laptops sounded like a data breach alarm. -
 Password LockerAre you fretted over forgetting your access data for various websites, applications, etc? Well this app provides you a secure way of storing all your passwords instead of noting them down on some diary. All you need to remember is the master password to unlock the app. You can trust Password Locker 100% as it does not have any access to the internet.MAIN FEATURES-The application does not attempt to send this data out to any other entity by any means.-Contains no advertisements.-Se
Password LockerAre you fretted over forgetting your access data for various websites, applications, etc? Well this app provides you a secure way of storing all your passwords instead of noting them down on some diary. All you need to remember is the master password to unlock the app. You can trust Password Locker 100% as it does not have any access to the internet.MAIN FEATURES-The application does not attempt to send this data out to any other entity by any means.-Contains no advertisements.-Se -
 RIA DigiDocRIA DigiDoc is an application that allows you to digitally sign documents, verify the validity of digital signatures, encrypt and open, save and share files on your mobile device using an Estonian ID card, NFC, mobile ID and Smart ID. Encryption/decryption via RIA DigiDoc only works with an Estonian ID card and a supported reader. Digitally signed containers are files with .bdoc, .ddoc or .asice extensions.With RIA DigiDoc app you can check your ID-card certificate validity, change PI
RIA DigiDocRIA DigiDoc is an application that allows you to digitally sign documents, verify the validity of digital signatures, encrypt and open, save and share files on your mobile device using an Estonian ID card, NFC, mobile ID and Smart ID. Encryption/decryption via RIA DigiDoc only works with an Estonian ID card and a supported reader. Digitally signed containers are files with .bdoc, .ddoc or .asice extensions.With RIA DigiDoc app you can check your ID-card certificate validity, change PI -
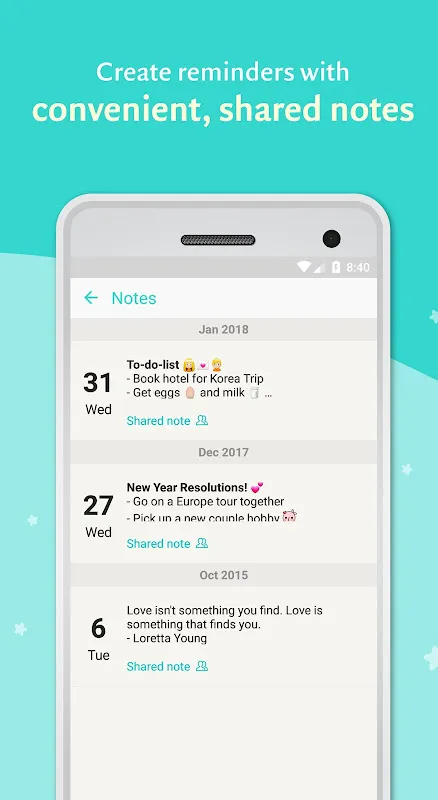 Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw
Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw -
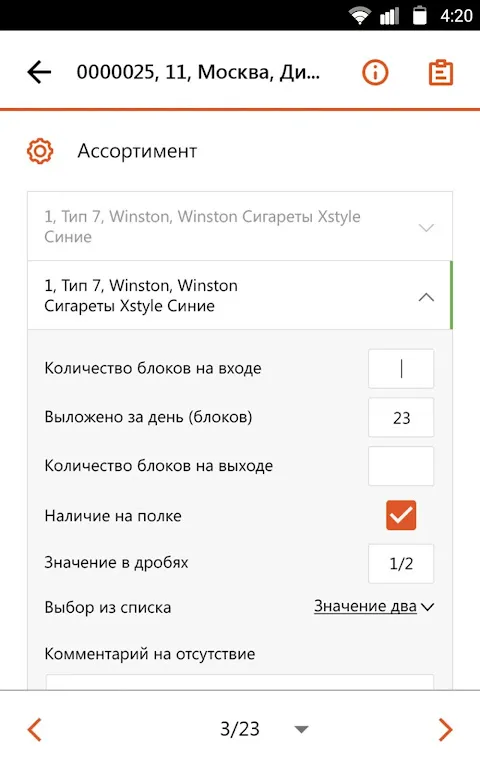 Rain lashed against my studio window like angry fists when the ransomware notification flashed. My entire freelance portfolio—years of architectural visualizations—locked behind that pulsing red skull icon. I remember the sour tang of panic rising in my throat as I frantically disconnected the NAS, fingers trembling against cold metal. That cursed email attachment from "Client_Revision.zip" had detonated silently while I'd been tweaking lighting gradients on a Barcelona penthouse render. For thr
Rain lashed against my studio window like angry fists when the ransomware notification flashed. My entire freelance portfolio—years of architectural visualizations—locked behind that pulsing red skull icon. I remember the sour tang of panic rising in my throat as I frantically disconnected the NAS, fingers trembling against cold metal. That cursed email attachment from "Client_Revision.zip" had detonated silently while I'd been tweaking lighting gradients on a Barcelona penthouse render. For thr -
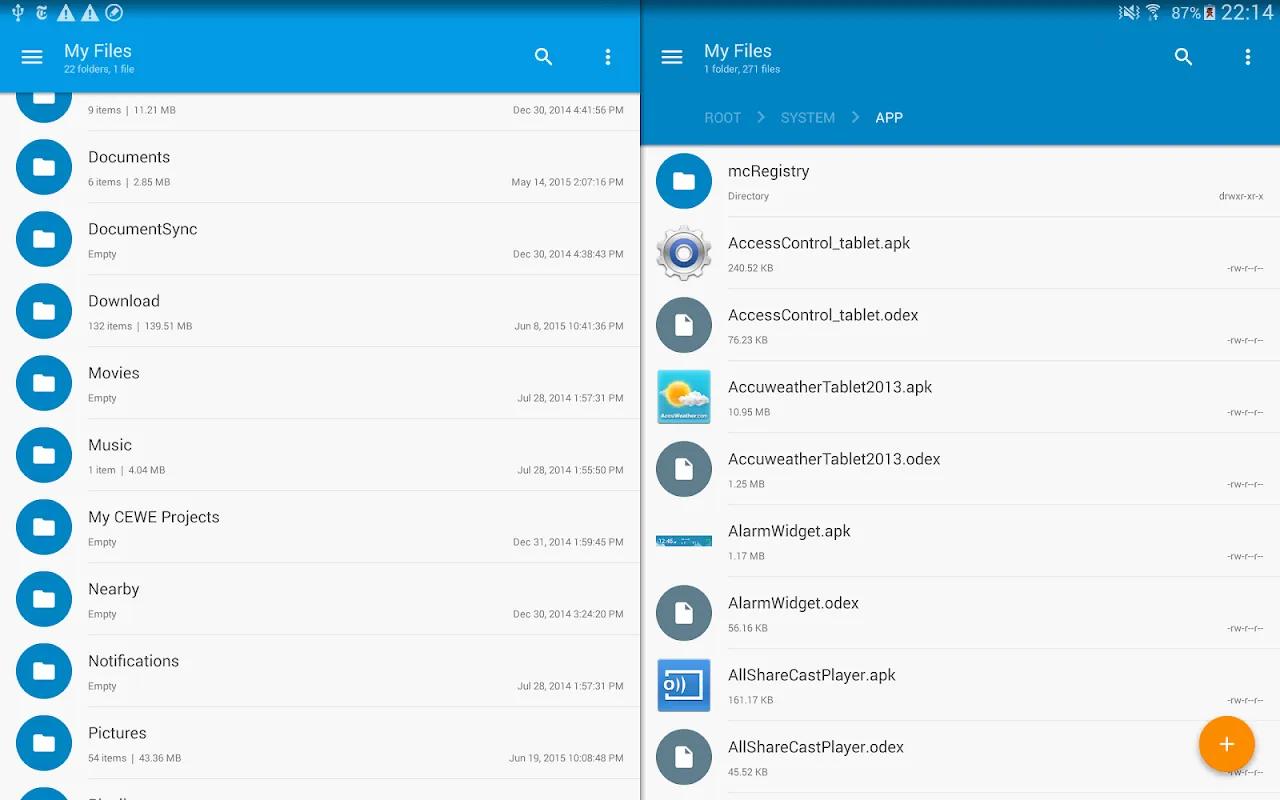 Rain lashed against the airport windows as I frantically swiped through my phone's storage, my flight boarding in 17 minutes. "Where is that damned contract?" I muttered, thumb smudging the screen as chaotic folders blurred together. My default file manager showed only endless nested directories - a digital rat maze. Then I remembered Solid Explorer's blue icon buried in my app drawer. What happened next felt like technological sorcery.
Rain lashed against the airport windows as I frantically swiped through my phone's storage, my flight boarding in 17 minutes. "Where is that damned contract?" I muttered, thumb smudging the screen as chaotic folders blurred together. My default file manager showed only endless nested directories - a digital rat maze. Then I remembered Solid Explorer's blue icon buried in my app drawer. What happened next felt like technological sorcery. -
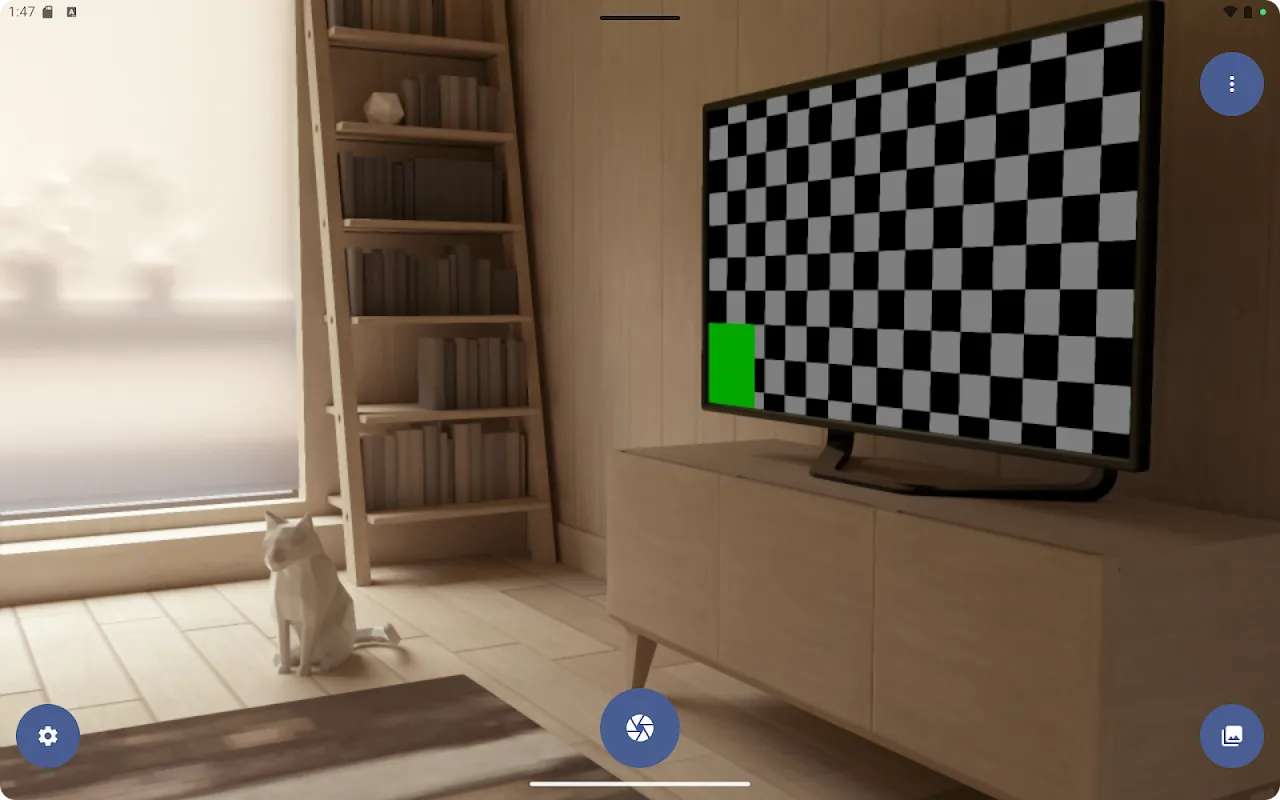 Rain lashed against the cafe window as I frantically swiped through my gallery, stomach churning. There it was - yesterday's street art photo, innocently shared online, now broadcasting the exact alley where I'd met my whistleblower source. The embedded GPS coordinates glared back like digital betrayal. In that humid panic, I finally understood how metadata turns cameras into snitches.
Rain lashed against the cafe window as I frantically swiped through my gallery, stomach churning. There it was - yesterday's street art photo, innocently shared online, now broadcasting the exact alley where I'd met my whistleblower source. The embedded GPS coordinates glared back like digital betrayal. In that humid panic, I finally understood how metadata turns cameras into snitches. -
 Rain lashed against my home office window as midnight approached, the blue glow of my laptop highlighting trembling fingers. Mortgage refinancing documents lay scattered like betrayal letters across my desk. Sending them via standard email felt like shouting my social security number in a crowded train station. That familiar acid reflux burned my throat - financial vulnerability distilled into physical pain. The Digital Handshake
Rain lashed against my home office window as midnight approached, the blue glow of my laptop highlighting trembling fingers. Mortgage refinancing documents lay scattered like betrayal letters across my desk. Sending them via standard email felt like shouting my social security number in a crowded train station. That familiar acid reflux burned my throat - financial vulnerability distilled into physical pain. The Digital Handshake -
 pCloud: Cloud StoragepCloud is the secure place to store, preview and share files, anywhere you go. Start with up to 10 GB free storage.You'll be able to backup photos and videos from your device, play your personal playlists, or preview work-related documents. You'll also be able to share large fil
pCloud: Cloud StoragepCloud is the secure place to store, preview and share files, anywhere you go. Start with up to 10 GB free storage.You'll be able to backup photos and videos from your device, play your personal playlists, or preview work-related documents. You'll also be able to share large fil