cyber strategy 2025-10-28T20:52:38Z
-
 Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we
Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we -
 Cyber School ManagerAbout Us: CSM - School Management Software Cyber School Manager (CSM) is your trusted partner in transforming the educational experience for both parents and students. CSM is a state-of-the-art school management app designed to streamline communication, enhance collaboration, and simplify the academic journey.For Parents: CSM is the one-stop solution to being close to your child's education. Knowing grades, attendance, and other assignments in real-time, you get to monitor yo
Cyber School ManagerAbout Us: CSM - School Management Software Cyber School Manager (CSM) is your trusted partner in transforming the educational experience for both parents and students. CSM is a state-of-the-art school management app designed to streamline communication, enhance collaboration, and simplify the academic journey.For Parents: CSM is the one-stop solution to being close to your child's education. Knowing grades, attendance, and other assignments in real-time, you get to monitor yo -
 Cyber Force Strike: ShootGamesCyber Force Strike: ShootGames is an action-packed third-person shooter mobile game available for the Android platform. This game immerses players in a colorful night city environment where they engage in combat against reptiloid invaders. Designed to provide a thrillin
Cyber Force Strike: ShootGamesCyber Force Strike: ShootGames is an action-packed third-person shooter mobile game available for the Android platform. This game immerses players in a colorful night city environment where they engage in combat against reptiloid invaders. Designed to provide a thrillin -
 Cyber Music RushLet's give a warm round of applause for Durple the Purple Dragon, straight from Incredible Sprunki! He loves collecting and playing trumpets with the Sprunki Group. Want to hear the latest remix from him and his Sprunki friends? Take a listen:Hello! Would you like to have some fun? W
Cyber Music RushLet's give a warm round of applause for Durple the Purple Dragon, straight from Incredible Sprunki! He loves collecting and playing trumpets with the Sprunki Group. Want to hear the latest remix from him and his Sprunki friends? Take a listen:Hello! Would you like to have some fun? W -
 Strategy TrainingWorld's largest strategy, management consulting proposals and consulting business-building training platform.Strategy Training is an online 24-hour strategy training channel offering incredibly detailed, and realistic, training programs in strategy, operations, implementation, leadership, management, critical problem solving, and case interviews. We offer reviews and guides to >USD$1MM winning management proposalsMcKinsey, BCG, PwC, Deloitte, BMO et. al former senior partners/di
Strategy TrainingWorld's largest strategy, management consulting proposals and consulting business-building training platform.Strategy Training is an online 24-hour strategy training channel offering incredibly detailed, and realistic, training programs in strategy, operations, implementation, leadership, management, critical problem solving, and case interviews. We offer reviews and guides to >USD$1MM winning management proposalsMcKinsey, BCG, PwC, Deloitte, BMO et. al former senior partners/di -
 Battle Strategy: Tower DefenseDefend your kingdom in intense tower defense battles, where your strategic thinking will be tested across various defense games and tower war games. Experience the thrill of \xd0\xbe\xd1\x84\xd0\xbb\xd0\xb0\xd0\xb9\xd0\xbd \xd0\xb8\xd0\xb3\xd1\x80\xd1\x8b, where you can perfect your strategy and defend against waves of enemies without the need for an internet connection. Use your skills in tower defense to outsmart your foes and enhance your towers to create an unst
Battle Strategy: Tower DefenseDefend your kingdom in intense tower defense battles, where your strategic thinking will be tested across various defense games and tower war games. Experience the thrill of \xd0\xbe\xd1\x84\xd0\xbb\xd0\xb0\xd0\xb9\xd0\xbd \xd0\xb8\xd0\xb3\xd1\x80\xd1\x8b, where you can perfect your strategy and defend against waves of enemies without the need for an internet connection. Use your skills in tower defense to outsmart your foes and enhance your towers to create an unst -
 Deal.II - Strategy GameDeal.II is a Deal Card Game that allows you to experience the followings - Collecting different sets of properties, performing Sly/Swap/Deal Actions, requesting birthday expenses / debts from your opponents.The modes of this Deal Card game are customize-able:1. Easy or Hard2. Two, Three or Four Players3. The goal of Three, Four or Five Property SetsReminder:1. In the Three/Four Players mode, you can directly tap the action card on his table.Please drop feedback through em
Deal.II - Strategy GameDeal.II is a Deal Card Game that allows you to experience the followings - Collecting different sets of properties, performing Sly/Swap/Deal Actions, requesting birthday expenses / debts from your opponents.The modes of this Deal Card game are customize-able:1. Easy or Hard2. Two, Three or Four Players3. The goal of Three, Four or Five Property SetsReminder:1. In the Three/Four Players mode, you can directly tap the action card on his table.Please drop feedback through em -
 Age of StrategyAge of Strategy is a free turn-based strategy game that immerses players in a historical setting filled with knights, vikings, samurais, and other legendary warriors. This Android app offers a gameplay experience reminiscent of classic strategy games, allowing users to engage in numerous campaigns, skirmishes, and multiplayer matches. Players can download Age of Strategy to explore its diverse features and enjoy its gameplay-oriented approach.The app includes over 500 campaign map
Age of StrategyAge of Strategy is a free turn-based strategy game that immerses players in a historical setting filled with knights, vikings, samurais, and other legendary warriors. This Android app offers a gameplay experience reminiscent of classic strategy games, allowing users to engage in numerous campaigns, skirmishes, and multiplayer matches. Players can download Age of Strategy to explore its diverse features and enjoy its gameplay-oriented approach.The app includes over 500 campaign map -
 OUTERPLANE - Strategy Anime\xe2\x96\xaeNew Players Up to 700 Free Recruits!The Action Anime, OUTERPLANE\xe2\x97\x8e The revenge saga of an Earthling summoned to another world commences! Summoned to "Mirsha," Earthling "K" pledges vengeance against betrayers, setting forth on a journey with the autom
OUTERPLANE - Strategy Anime\xe2\x96\xaeNew Players Up to 700 Free Recruits!The Action Anime, OUTERPLANE\xe2\x97\x8e The revenge saga of an Earthling summoned to another world commences! Summoned to "Mirsha," Earthling "K" pledges vengeance against betrayers, setting forth on a journey with the autom -
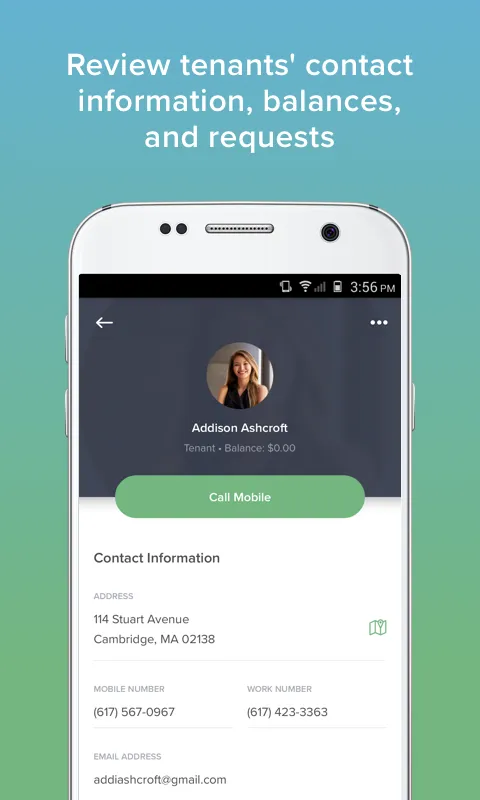 Rain lashed against my office window when the screens went black – not from the storm, but from a ransomware notification flashing on every device. My property management firm’s servers were dead. Tenant records? Gone. Lease agreements? Encrypted. Payment histories? Held hostage. That sinking feeling hit like physical nausea; 347 units across three states suddenly felt like dominoes about to collapse.
Rain lashed against my office window when the screens went black – not from the storm, but from a ransomware notification flashing on every device. My property management firm’s servers were dead. Tenant records? Gone. Lease agreements? Encrypted. Payment histories? Held hostage. That sinking feeling hit like physical nausea; 347 units across three states suddenly felt like dominoes about to collapse. -
 The stale aftertaste of generic shooters still lingered when my thumb first hovered over the download icon. Another alien blaster? My expectations flatlined. But as the neon-drenched warzone materialized, something primal kicked in - like smelling ozone before lightning strikes. Those first seconds weren't gameplay; they were sensory overload. Holographic billboards flickered corrosive green across rain-slicked alleys while the invaders' hydraulic hisses crawled up my spine. My cheap earbuds tra
The stale aftertaste of generic shooters still lingered when my thumb first hovered over the download icon. Another alien blaster? My expectations flatlined. But as the neon-drenched warzone materialized, something primal kicked in - like smelling ozone before lightning strikes. Those first seconds weren't gameplay; they were sensory overload. Holographic billboards flickered corrosive green across rain-slicked alleys while the invaders' hydraulic hisses crawled up my spine. My cheap earbuds tra -
 The 7:15 express smelled of stale coffee and existential dread that Tuesday. Jammed between a man yelling stock prices and a teenager blasting dubstep through cracked earbuds, I nearly missed my stop - again. My thumb scrolled through app store wastelands until I stumbled upon Damru Bead 16. What happened next wasn't gaming. It was warfare.
The 7:15 express smelled of stale coffee and existential dread that Tuesday. Jammed between a man yelling stock prices and a teenager blasting dubstep through cracked earbuds, I nearly missed my stop - again. My thumb scrolled through app store wastelands until I stumbled upon Damru Bead 16. What happened next wasn't gaming. It was warfare. -
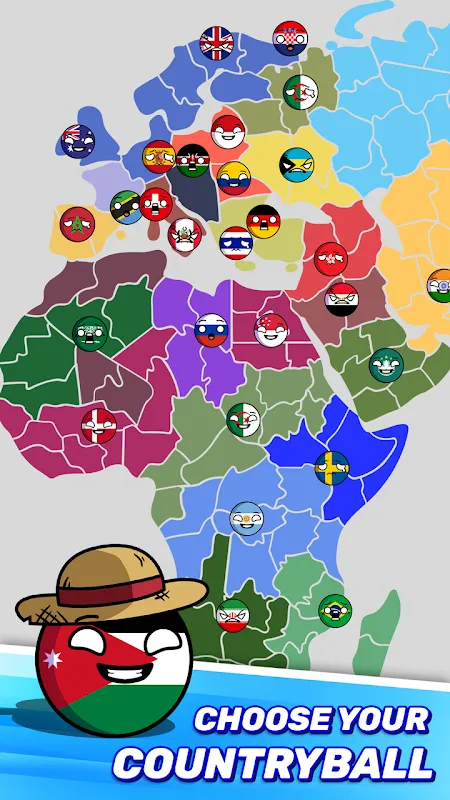 That gloomy afternoon, I was scrolling through endless cartoonish battle games feeling utterly numb - until spherical soldiers in berets caught my eye. Country Balls: World Battle didn't just distract me from the thunder outside; it consumed my entire weekend in the best possible way. I remember nervously wiping sweaty palms on my jeans during the Poland campaign, artillery units positioned behind wheat fields while cavalry circled through mountain passes. The terrain elevation mechanics complet
That gloomy afternoon, I was scrolling through endless cartoonish battle games feeling utterly numb - until spherical soldiers in berets caught my eye. Country Balls: World Battle didn't just distract me from the thunder outside; it consumed my entire weekend in the best possible way. I remember nervously wiping sweaty palms on my jeans during the Poland campaign, artillery units positioned behind wheat fields while cavalry circled through mountain passes. The terrain elevation mechanics complet -
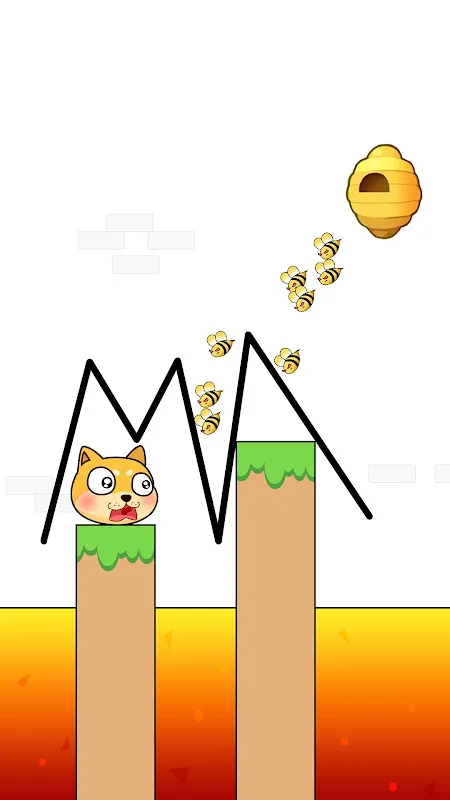 Rain lashed against the train windows as we crawled through the outskirts, the 6:45am local shuddering like my tired nerves. Another predawn sprint to make this metal tube, another day facing spreadsheets that sucked my soul dry. My thumb hovered over my usual time-killers - the candy-crush clones and endless runners that left me feeling emptier than before. Then I spotted it: a jagged sword icon promising five-minute conquests. What harm could one download do?
Rain lashed against the train windows as we crawled through the outskirts, the 6:45am local shuddering like my tired nerves. Another predawn sprint to make this metal tube, another day facing spreadsheets that sucked my soul dry. My thumb hovered over my usual time-killers - the candy-crush clones and endless runners that left me feeling emptier than before. Then I spotted it: a jagged sword icon promising five-minute conquests. What harm could one download do? -
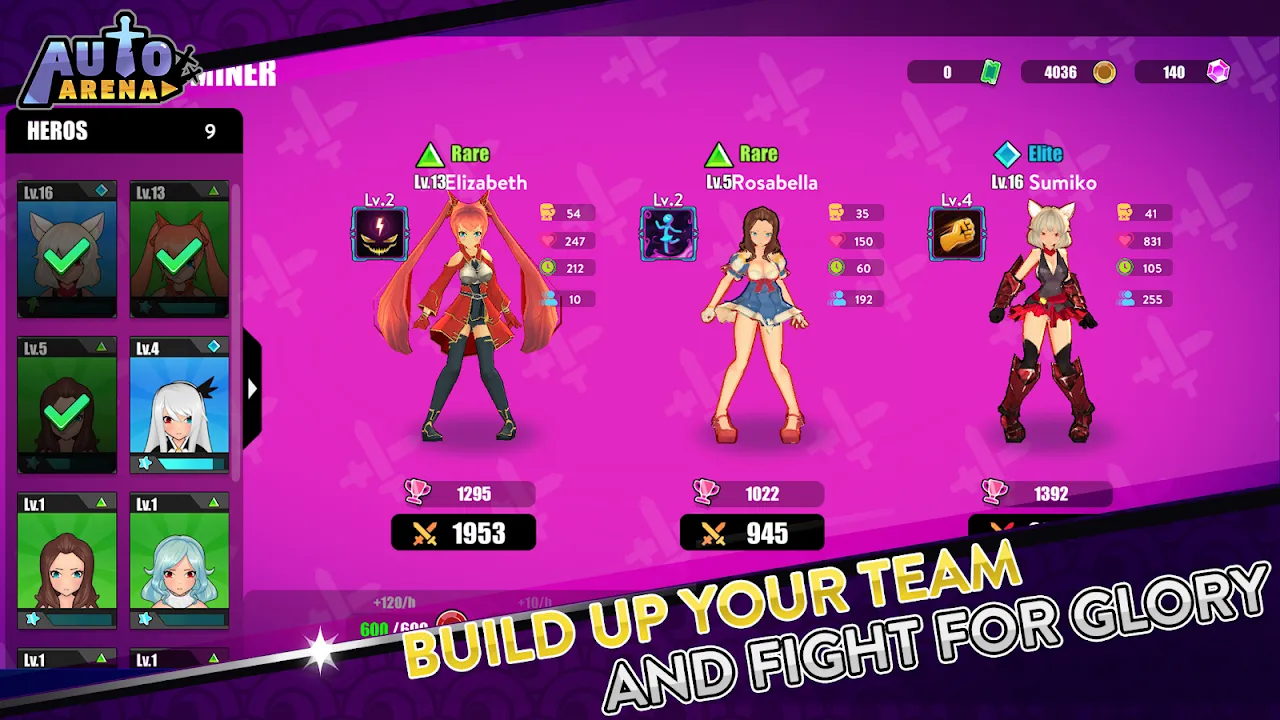 Thunder rattled my apartment windows last Saturday while I stared at a spreadsheet that refused to make sense. My brain felt like overcooked noodles - utterly useless for analytical work yet buzzing with restless energy. That's when I remembered the neon-green icon glaring from my third homescreen: Auto Arena: My Brutes. With nothing left to lose, I tapped it and fell headfirst into the most unexpectedly tactical rabbit hole of my gaming life.
Thunder rattled my apartment windows last Saturday while I stared at a spreadsheet that refused to make sense. My brain felt like overcooked noodles - utterly useless for analytical work yet buzzing with restless energy. That's when I remembered the neon-green icon glaring from my third homescreen: Auto Arena: My Brutes. With nothing left to lose, I tapped it and fell headfirst into the most unexpectedly tactical rabbit hole of my gaming life. -
 BlackJack Trainer 21 StrategyLearn how to play BlackJack, when to Hit, Stand, Split, Double or Surrender.BlackJack Trainer Lite will teach you to how to play any hand, such that you maximize your chance of winning by playing the basic strategy. Use this app as the fastest way to improve your BlackJack game skills.******** \xf0\x9f\x9b\x91 This app is so successful, it's use is banned from casinos in The United States and across Europe \xf0\x9f\x9b\x91 ********Features:\xe2\x99\xa3\xef\xb8\x8f Hi
BlackJack Trainer 21 StrategyLearn how to play BlackJack, when to Hit, Stand, Split, Double or Surrender.BlackJack Trainer Lite will teach you to how to play any hand, such that you maximize your chance of winning by playing the basic strategy. Use this app as the fastest way to improve your BlackJack game skills.******** \xf0\x9f\x9b\x91 This app is so successful, it's use is banned from casinos in The United States and across Europe \xf0\x9f\x9b\x91 ********Features:\xe2\x99\xa3\xef\xb8\x8f Hi -
 Rain lashed against the coffee shop window as I stared blankly at my laptop's error logs. Another deployment failure. Three weeks of coding hell had reduced my confidence to rubble when a notification pierced the gloom - "Doctor, new operators await command." On a whim, I tapped in. What greeted me wasn't escapism, but a tactical crucible demanding absolute focus. Suddenly, my real-world frustrations dissolved into calculating enemy paths on Lungmen's rain-slicked streets. Each drag-and-drop ope
Rain lashed against the coffee shop window as I stared blankly at my laptop's error logs. Another deployment failure. Three weeks of coding hell had reduced my confidence to rubble when a notification pierced the gloom - "Doctor, new operators await command." On a whim, I tapped in. What greeted me wasn't escapism, but a tactical crucible demanding absolute focus. Suddenly, my real-world frustrations dissolved into calculating enemy paths on Lungmen's rain-slicked streets. Each drag-and-drop ope


