cybersecurity authentication 2025-11-06T06:53:34Z
-
 Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo
Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo -
 NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/
NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/ -
 TunnelBear VPNTunnelBear VPN. Privacy. For everyone. TunnelBear is an easy-to-use VPN app that helps you browse privately and securely from anywhere. With just one tap, TunnelBear changes your IP address and encrypts your browsing data, protecting it from online threats. It\xe2\x80\x99s so simple, e
TunnelBear VPNTunnelBear VPN. Privacy. For everyone. TunnelBear is an easy-to-use VPN app that helps you browse privately and securely from anywhere. With just one tap, TunnelBear changes your IP address and encrypts your browsing data, protecting it from online threats. It\xe2\x80\x99s so simple, e -
 Digidentity WalletManage your digital identity effortlessly with the Digidentity Wallet. Log in with ease while at the highest levels of assurance. Sign your documents with qualified e-signatures (QES). Explore our wallet and it\xe2\x80\x99s services. Stay in control of your personal data.About Digi
Digidentity WalletManage your digital identity effortlessly with the Digidentity Wallet. Log in with ease while at the highest levels of assurance. Sign your documents with qualified e-signatures (QES). Explore our wallet and it\xe2\x80\x99s services. Stay in control of your personal data.About Digi -
 Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu
Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu -
 The fluorescent lights hummed overhead as I slumped in another soul-crushing training session, watching colleagues covertly check phones beneath the table. Our compliance officer droned through GDPR regulations like a metronome set to funeral tempo. Then the HR director burst in waving her tablet - "We're trying something new today!" My eyes rolled so hard I saw my own brain. Gamification? Please. I'd suffered through enough cringe-worthy corporate "fun" to know this would be another patronizing
The fluorescent lights hummed overhead as I slumped in another soul-crushing training session, watching colleagues covertly check phones beneath the table. Our compliance officer droned through GDPR regulations like a metronome set to funeral tempo. Then the HR director burst in waving her tablet - "We're trying something new today!" My eyes rolled so hard I saw my own brain. Gamification? Please. I'd suffered through enough cringe-worthy corporate "fun" to know this would be another patronizing -
 TrackIP - Track any IP AddressTrack IP is a free and user-friendly tool that allows you to search and track any IP address in the world. With our easy-to-use app, you can quickly and accurately locate any IP address and get detailed information about its location, including the city, country, region, and ZIP code. Whether you're a professional network administrator or a casual internet user, Track IP is the perfect tool for finding and tracking IP addresses with ease and speed.Features :Copy, Sh
TrackIP - Track any IP AddressTrack IP is a free and user-friendly tool that allows you to search and track any IP address in the world. With our easy-to-use app, you can quickly and accurately locate any IP address and get detailed information about its location, including the city, country, region, and ZIP code. Whether you're a professional network administrator or a casual internet user, Track IP is the perfect tool for finding and tracking IP addresses with ease and speed.Features :Copy, Sh -
 Safehouse VPN & MobileSecuritySafehouse is a mobile application designed to enhance online privacy and security for users. This app, formerly known as Bodyguard Mobile Security, offers a variety of features that help protect personal data and ensure a safe browsing experience. Safehouse is available
Safehouse VPN & MobileSecuritySafehouse is a mobile application designed to enhance online privacy and security for users. This app, formerly known as Bodyguard Mobile Security, offers a variety of features that help protect personal data and ensure a safe browsing experience. Safehouse is available -
 CFC ResponseThe CFC incident response app gives you the ability to instantly notify our incident response team of a cyber event. The app includes a tailored threat intelligence feed, direct access to our world-class cyber incident response team via the 'Ask the expert' functionality, and a number of tools to help you protect your business against cyber attacks.Enhanced features include:\xc2\xb7 Fast and detailed instant reporting of live cyber incidents to the cyber claims team;\xc2\xb7 Bespoke
CFC ResponseThe CFC incident response app gives you the ability to instantly notify our incident response team of a cyber event. The app includes a tailored threat intelligence feed, direct access to our world-class cyber incident response team via the 'Ask the expert' functionality, and a number of tools to help you protect your business against cyber attacks.Enhanced features include:\xc2\xb7 Fast and detailed instant reporting of live cyber incidents to the cyber claims team;\xc2\xb7 Bespoke -
 The fluorescent lights of the Istanbul airport departure lounge hummed like angry hornets as I frantically jabbed at my phone. "Invalid code" glared back at me for the seventh time. Sweat trickled down my collar as I realized my work VPN had just locked me out halfway across the world. That cursed authenticator app had betrayed me again, turning a simple email check into a panic attack at Gate C17. Right then I remembered the odd little USB key my security-obsessed friend had shoved into my palm
The fluorescent lights of the Istanbul airport departure lounge hummed like angry hornets as I frantically jabbed at my phone. "Invalid code" glared back at me for the seventh time. Sweat trickled down my collar as I realized my work VPN had just locked me out halfway across the world. That cursed authenticator app had betrayed me again, turning a simple email check into a panic attack at Gate C17. Right then I remembered the odd little USB key my security-obsessed friend had shoved into my palm -
 I still remember the chill that ran down my spine when my phone buzzed late that Tuesday night. It was a message from my sister, Lena, who was studying abroad in Spain. Her voice, usually bubbly and full of life, was strained through the text: "I need help, fast. Medical emergency, and I'm short on cash." My heart hammered against my ribs; she was thousands of miles away, alone, and I felt utterly helpless. Scrolling through my apps in a panic, my thumb hovered over banking icons
I still remember the chill that ran down my spine when my phone buzzed late that Tuesday night. It was a message from my sister, Lena, who was studying abroad in Spain. Her voice, usually bubbly and full of life, was strained through the text: "I need help, fast. Medical emergency, and I'm short on cash." My heart hammered against my ribs; she was thousands of miles away, alone, and I felt utterly helpless. Scrolling through my apps in a panic, my thumb hovered over banking icons -
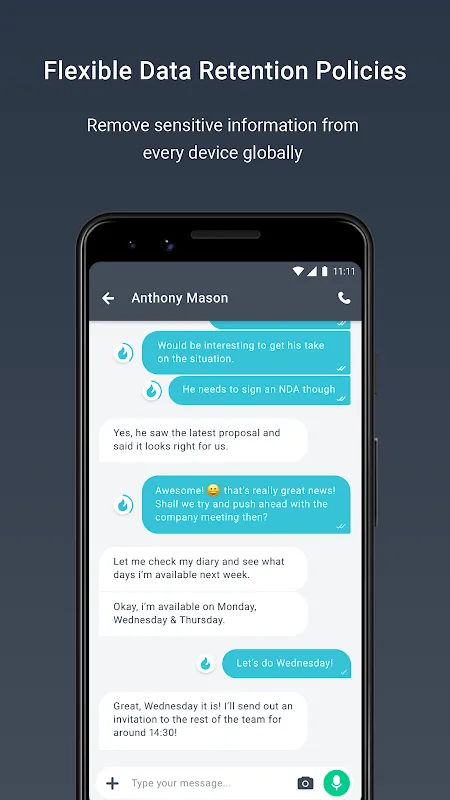 It was 3 AM, and the glow of my laptop screen was the only light in the silent office, casting shadows that seemed to whisper of impending doom. I had been chasing a phantom data breach for weeks, my nerves frayed like old rope, and every notification from our team's messaging app felt like a potential tripwire. As the head of cybersecurity for a mid-sized financial advisory firm, I was drowning in paranoia—until our IT director slid a new device across my desk with a single app installed: SaltI
It was 3 AM, and the glow of my laptop screen was the only light in the silent office, casting shadows that seemed to whisper of impending doom. I had been chasing a phantom data breach for weeks, my nerves frayed like old rope, and every notification from our team's messaging app felt like a potential tripwire. As the head of cybersecurity for a mid-sized financial advisory firm, I was drowning in paranoia—until our IT director slid a new device across my desk with a single app installed: SaltI -
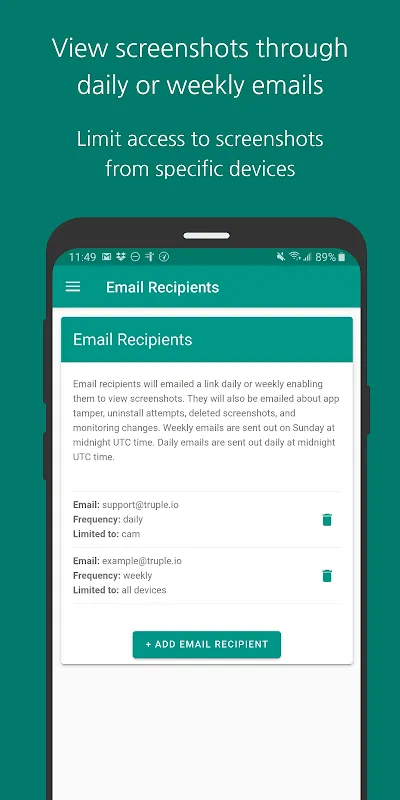 My knuckles turned bone-white gripping the phone at 3:17 AM, its cold blue light cutting through the nursery darkness where I rocked my colicky newborn. The alert vibration felt like an electric cattle prod - not for sleep deprivation, but for the gut-churning screenshot flashing on screen: my 14-year-old daughter's Instagram DM thread filled with razor-blade emojis and "KYS" messages from an account named @grimreaperfan. Milk stains soaked my shirt as panic iced my veins. This wasn't just cyber
My knuckles turned bone-white gripping the phone at 3:17 AM, its cold blue light cutting through the nursery darkness where I rocked my colicky newborn. The alert vibration felt like an electric cattle prod - not for sleep deprivation, but for the gut-churning screenshot flashing on screen: my 14-year-old daughter's Instagram DM thread filled with razor-blade emojis and "KYS" messages from an account named @grimreaperfan. Milk stains soaked my shirt as panic iced my veins. This wasn't just cyber -
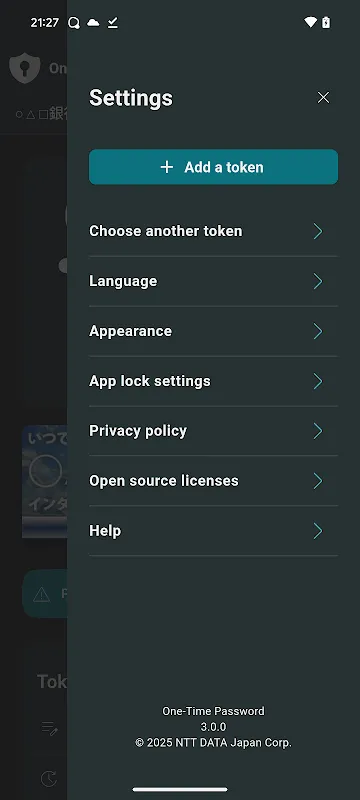 That frantic Tuesday morning still haunts me - stranded at Heathrow with a dead SIM card, desperately needing to approve a client contract. Sweat trickled down my neck as airport Wi-Fi mocked my login attempts. Corporate security protocols demanded secondary verification, but my phone couldn't receive SMS codes. Just as panic tightened its grip around my throat, I remembered the tiny shield icon tucked in my utilities folder.
That frantic Tuesday morning still haunts me - stranded at Heathrow with a dead SIM card, desperately needing to approve a client contract. Sweat trickled down my neck as airport Wi-Fi mocked my login attempts. Corporate security protocols demanded secondary verification, but my phone couldn't receive SMS codes. Just as panic tightened its grip around my throat, I remembered the tiny shield icon tucked in my utilities folder. -
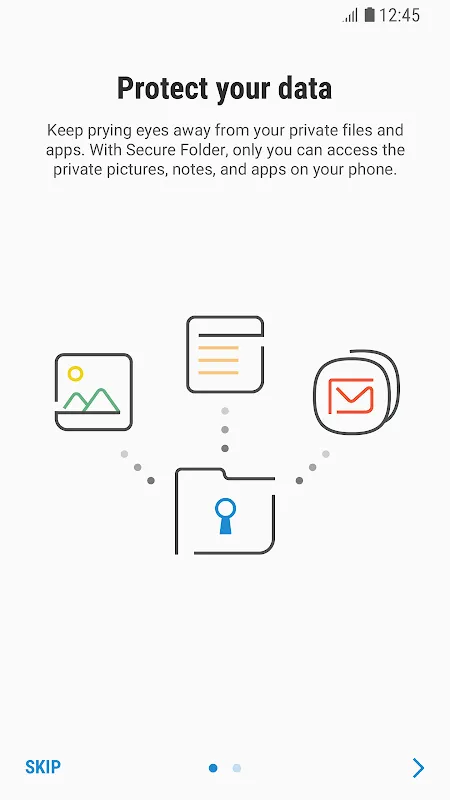 That gut-wrenching lurch when your fingers close around empty air where your phone should be - I tasted pure panic standing outside Frankfurt Airport. My flight had landed 20 minutes prior, and somewhere between baggage claim and taxi queue, my Galaxy S22 had abandoned me. Not just a device gone, but my entire digital existence: client contracts, intimate voice notes to my wife, even those embarrassing gym selfies. As I stood paralyzed watching rain streak the terminal windows, one horrifying re
That gut-wrenching lurch when your fingers close around empty air where your phone should be - I tasted pure panic standing outside Frankfurt Airport. My flight had landed 20 minutes prior, and somewhere between baggage claim and taxi queue, my Galaxy S22 had abandoned me. Not just a device gone, but my entire digital existence: client contracts, intimate voice notes to my wife, even those embarrassing gym selfies. As I stood paralyzed watching rain streak the terminal windows, one horrifying re -
 Okta VerifyOkta Verify is a lightweight app that allows you to securely access your apps via 2-step verification, ensuring that you, and only you, can access your app accounts.While you access your apps, you'll choose a 2-step verification method provided by Okta Verify to finish signing in. You can
Okta VerifyOkta Verify is a lightweight app that allows you to securely access your apps via 2-step verification, ensuring that you, and only you, can access your app accounts.While you access your apps, you'll choose a 2-step verification method provided by Okta Verify to finish signing in. You can -
 Rain lashed against my office window as I stared at the third bounced email notification. "Incomplete KYC documentation," it sneered. My thumb hovered over the fund house's contact number when monsoon water seeped through the sill, soaking the physical NAV statements I'd spent hours collating. Ink bled across six months of careful tracking like financial wounds. That damp, curling paper smell - musty failure - triggered something primal. I hurled the soggy bundle across the room where it slapped
Rain lashed against my office window as I stared at the third bounced email notification. "Incomplete KYC documentation," it sneered. My thumb hovered over the fund house's contact number when monsoon water seeped through the sill, soaking the physical NAV statements I'd spent hours collating. Ink bled across six months of careful tracking like financial wounds. That damp, curling paper smell - musty failure - triggered something primal. I hurled the soggy bundle across the room where it slapped


