cybersecurity tools 2025-10-31T00:22:58Z
-
 Bot Changer VPNBot Changer VPN is Ultra fast VPN service. Bot Changer VPN is the ultimate Android VPN. It is a 100% unlimited VPN that does not require any type of registration.Bot Changer VPN is completely anonymous. All of your traffic is encrypted while VPN is on.Bot Changer VPN protects your privacy and identity and allows you to browse the web anonymously without fear of being tracked.How does Bot Changer VPN Work?Bot Changer VPN encrypts your data and safely connects you to any web site or
Bot Changer VPNBot Changer VPN is Ultra fast VPN service. Bot Changer VPN is the ultimate Android VPN. It is a 100% unlimited VPN that does not require any type of registration.Bot Changer VPN is completely anonymous. All of your traffic is encrypted while VPN is on.Bot Changer VPN protects your privacy and identity and allows you to browse the web anonymously without fear of being tracked.How does Bot Changer VPN Work?Bot Changer VPN encrypts your data and safely connects you to any web site or -
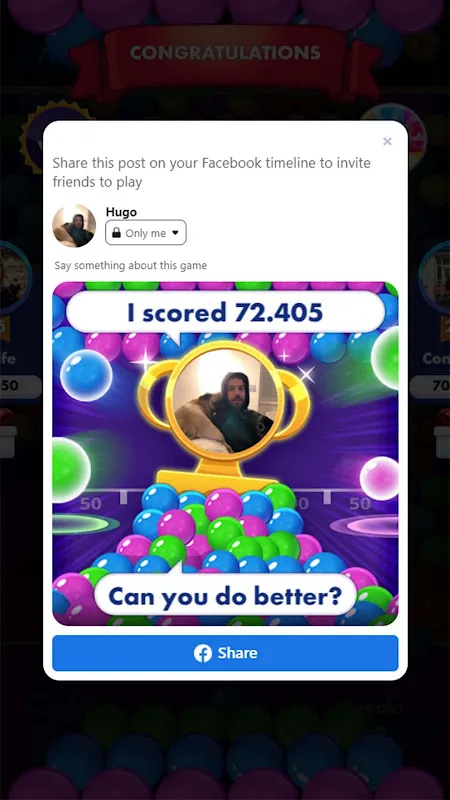 Rain lashed against the office window like pebbles on tin as my spreadsheet blurred into meaningless cells. That familiar tightness crept up my neck - deadlines looming, emails piling up, and my brain refusing to cooperate. I grabbed my phone with trembling fingers, not for social media, but for salvation: Bubble Shooter Pro. What happened next wasn't just distraction; it became a masterclass in cognitive recalibration.
Rain lashed against the office window like pebbles on tin as my spreadsheet blurred into meaningless cells. That familiar tightness crept up my neck - deadlines looming, emails piling up, and my brain refusing to cooperate. I grabbed my phone with trembling fingers, not for social media, but for salvation: Bubble Shooter Pro. What happened next wasn't just distraction; it became a masterclass in cognitive recalibration. -
 Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we
Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we -
 NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/
NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/ -
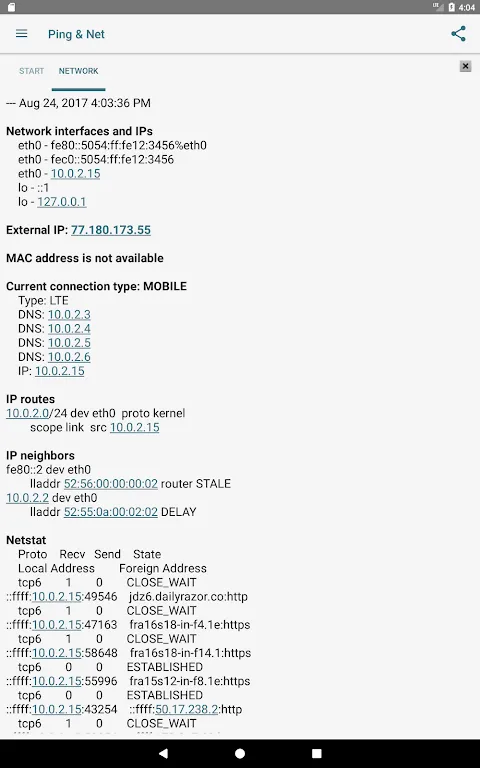 Sweat pooled at my collar as the projector screen froze mid-sentence during the Acme Corp pitch. "Just refreshing!" I chirped through clenched teeth while frantic pings died in the void. Three failed presentations in two weeks had management eyeing my termination letter. That night, I tore open server cabinets until dawn, yanking ethernet cables like rotten teeth while our IT guy mumbled about "possible packet storms." Desperation made me try Ping & Net - that unassuming Android toolkit I'd mock
Sweat pooled at my collar as the projector screen froze mid-sentence during the Acme Corp pitch. "Just refreshing!" I chirped through clenched teeth while frantic pings died in the void. Three failed presentations in two weeks had management eyeing my termination letter. That night, I tore open server cabinets until dawn, yanking ethernet cables like rotten teeth while our IT guy mumbled about "possible packet storms." Desperation made me try Ping & Net - that unassuming Android toolkit I'd mock -
 Epidemic Sound Music for VideoBring your story to life with the Epidemic Sound app.Discover, save, and download music for your content on the go. Get unlimited access to over 50,000 tracks and 200,000 sound effects to add more feeling and more meaning to everything you create. With personalized recommendations, curated collections, and soundtracking tools that fit seamlessly into your workflow, you can find the perfect soundtrack, fast. And with all rights included, you can soundtrack and publis
Epidemic Sound Music for VideoBring your story to life with the Epidemic Sound app.Discover, save, and download music for your content on the go. Get unlimited access to over 50,000 tracks and 200,000 sound effects to add more feeling and more meaning to everything you create. With personalized recommendations, curated collections, and soundtracking tools that fit seamlessly into your workflow, you can find the perfect soundtrack, fast. And with all rights included, you can soundtrack and publis -
 Rain lashed against my apartment windows like a thousand tiny hackers probing for vulnerabilities. I'd just spent eight hours reviewing firewall logs – real-world cybersecurity that felt less like digital warfare and more like watching paint dry on server racks. My coffee had gone cold three times, each reheating a sad ritual mirroring the monotony of threat alerts blinking across dual monitors. That's when the notification appeared: "Your underground botnet awaits deployment." Not on my work da
Rain lashed against my apartment windows like a thousand tiny hackers probing for vulnerabilities. I'd just spent eight hours reviewing firewall logs – real-world cybersecurity that felt less like digital warfare and more like watching paint dry on server racks. My coffee had gone cold three times, each reheating a sad ritual mirroring the monotony of threat alerts blinking across dual monitors. That's when the notification appeared: "Your underground botnet awaits deployment." Not on my work da -
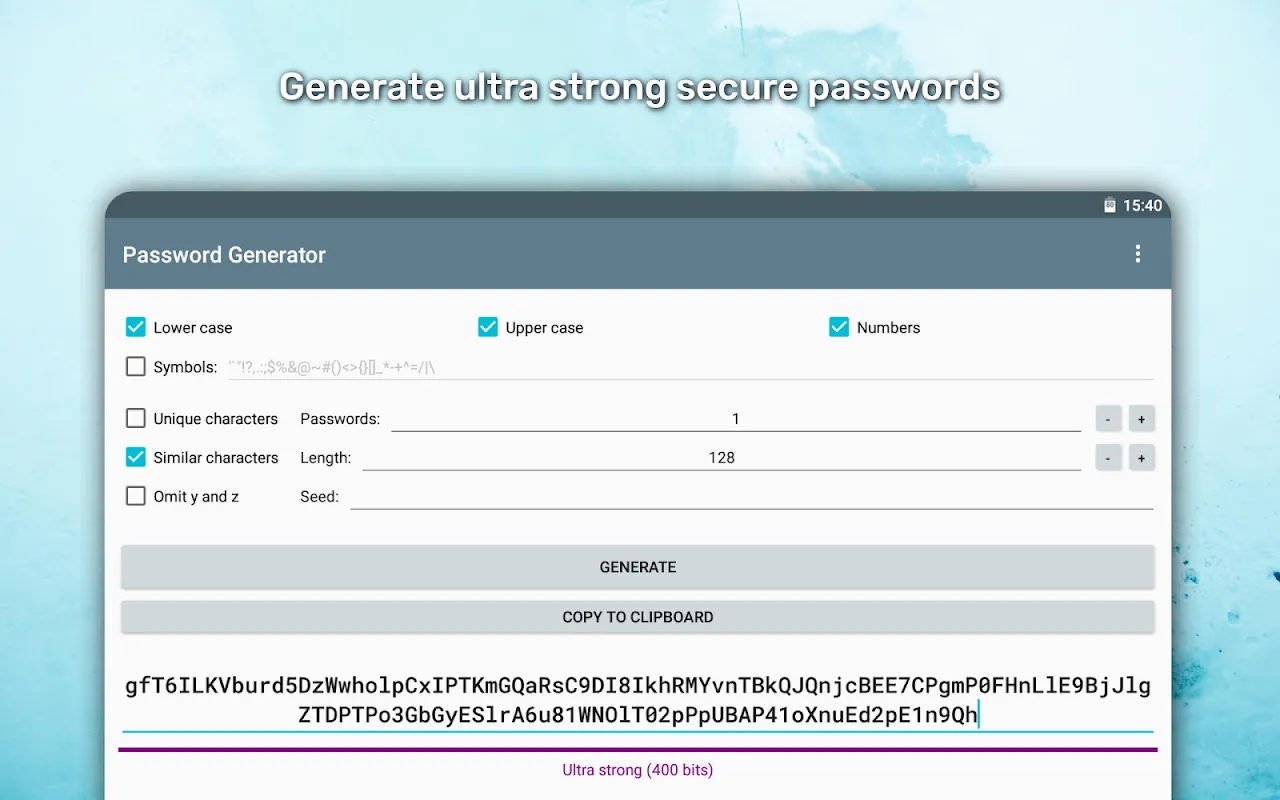 Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu
Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu -
 GartnerGartner delivers actionable, objective insight to executives and their teams. With Gartner Mobile you're able to access our expert guidance and tools wherever you are.As a registered Gartner client, the app allows you to:- Make faster, smarter, decisions with personalized content based on your mission-critical priorities.- Easily search for additional insights.- Save documents and access them anytime on both mobile and web.- Pick up where you left off from your most recently accessed rese
GartnerGartner delivers actionable, objective insight to executives and their teams. With Gartner Mobile you're able to access our expert guidance and tools wherever you are.As a registered Gartner client, the app allows you to:- Make faster, smarter, decisions with personalized content based on your mission-critical priorities.- Easily search for additional insights.- Save documents and access them anytime on both mobile and web.- Pick up where you left off from your most recently accessed rese -
 LEPoLEKOn our platform you will find dozens of courses, hundreds of articles and slides, thousands of questions with comments, and much more. The platform is updated daily with new guidelines or recommendations.With LEPOLK Revolution you can use your laptop, tablet or smartphone, no matter if you ar
LEPoLEKOn our platform you will find dozens of courses, hundreds of articles and slides, thousands of questions with comments, and much more. The platform is updated daily with new guidelines or recommendations.With LEPOLK Revolution you can use your laptop, tablet or smartphone, no matter if you ar -
 1Password: Password Manager1Password has been helping folks forget their passwords since 2006. Trusted by millions of people and more than 150,000 businesses, "1Password offers the best combination of features, compatibility, security, and ease of use" among password managers, according to The New Y
1Password: Password Manager1Password has been helping folks forget their passwords since 2006. Trusted by millions of people and more than 150,000 businesses, "1Password offers the best combination of features, compatibility, security, and ease of use" among password managers, according to The New Y -
 The relentless Kolkata sun beat down as I stood ankle-deep in mud, staring at the crumbling boundary markers of what was supposed to be my dream farm. My contractor's voice cut through the humidity like a rusty blade - "If these measurements are wrong, your entire irrigation system collapses next monsoon." I'd spent three weeks chasing patwari office clerks for land records only to receive contradictory parchments smelling of mildew and bureaucracy. That sinking feeling of watching a lifetime in
The relentless Kolkata sun beat down as I stood ankle-deep in mud, staring at the crumbling boundary markers of what was supposed to be my dream farm. My contractor's voice cut through the humidity like a rusty blade - "If these measurements are wrong, your entire irrigation system collapses next monsoon." I'd spent three weeks chasing patwari office clerks for land records only to receive contradictory parchments smelling of mildew and bureaucracy. That sinking feeling of watching a lifetime in -
 TchapTchap is an instant messaging service intended for communications by French administration agents, to exchange information on the move or from an office workstation. Tchap allows you to chat via messages in pairs and in groups, and to share files like any instant messenger, with an integrated directory of user agents, simultaneous use on several devices and confidentiality of private exchanges.Agents can invite outsiders into a professional conversation.The app requires the USE_FULL_SCREEN_
TchapTchap is an instant messaging service intended for communications by French administration agents, to exchange information on the move or from an office workstation. Tchap allows you to chat via messages in pairs and in groups, and to share files like any instant messenger, with an integrated directory of user agents, simultaneous use on several devices and confidentiality of private exchanges.Agents can invite outsiders into a professional conversation.The app requires the USE_FULL_SCREEN_ -
 DarktraceDarktrace is a cybersecurity application designed to enhance threat detection and response capabilities for users on the go. This app allows individuals to remain connected to their Darktrace deployment, utilizing advanced technologies known as Darktrace DETECT and Darktrace RESPOND. Available for the Android platform, users can download Darktrace to receive real-time notifications about potential threats and activate AI-driven autonomous responses from their mobile devices.The primary
DarktraceDarktrace is a cybersecurity application designed to enhance threat detection and response capabilities for users on the go. This app allows individuals to remain connected to their Darktrace deployment, utilizing advanced technologies known as Darktrace DETECT and Darktrace RESPOND. Available for the Android platform, users can download Darktrace to receive real-time notifications about potential threats and activate AI-driven autonomous responses from their mobile devices.The primary -
 BB Internacional"BB Internacional", EXCLUSIVE for customers of Banco do Brasil in Japan.You are one step away from a new digital experience: now the new BB Internacional app is much more agile and intuitive.With it, you can access your Banco do Brasil Japan international account from wherever you are!It became much easier and more practical to have the Bank in your hands, without having to leave the comfort of your home to carry out your operations!In addition to the new Smartphone ATM function,
BB Internacional"BB Internacional", EXCLUSIVE for customers of Banco do Brasil in Japan.You are one step away from a new digital experience: now the new BB Internacional app is much more agile and intuitive.With it, you can access your Banco do Brasil Japan international account from wherever you are!It became much easier and more practical to have the Bank in your hands, without having to leave the comfort of your home to carry out your operations!In addition to the new Smartphone ATM function, -
 Black Hat EventsBlack Hat Events are the most technical and relevant information security conferences and trainings in the world. Providing attendees with the very latest in information security research, development, and trends, Black Hat Events bring the global InfoSec community together to share ideas, learn from experts, and network with peers, practitioners, researchers, and solutions providers from around the globe. The Black Hat Events portfolio includes all Black Hat global events, as we
Black Hat EventsBlack Hat Events are the most technical and relevant information security conferences and trainings in the world. Providing attendees with the very latest in information security research, development, and trends, Black Hat Events bring the global InfoSec community together to share ideas, learn from experts, and network with peers, practitioners, researchers, and solutions providers from around the globe. The Black Hat Events portfolio includes all Black Hat global events, as we -
 URLCheckThis application acts as an intermediary when opening url links. When you do so, a window containing information about the url is displayed, allowing you to make changes to it as well.Specially useful when you need to open an external link either from an email, a social network app or others.URLCheck is developed by TrianguloY, originally for personal use. It is open source (under CC BY 4.0 license), free, without any ads or trackers, light sized and using as few permissions as necessary
URLCheckThis application acts as an intermediary when opening url links. When you do so, a window containing information about the url is displayed, allowing you to make changes to it as well.Specially useful when you need to open an external link either from an email, a social network app or others.URLCheck is developed by TrianguloY, originally for personal use. It is open source (under CC BY 4.0 license), free, without any ads or trackers, light sized and using as few permissions as necessary


