decentralized authentication 2025-11-19T03:10:54Z
-
 Rain lashed against my apartment window as I thumb-scrolled through another soul-crushing feed. Ads for weight loss teas sandwiched between political screaming matches, while some algorithm kept resurrecting my ex's vacation photos. My thumb hovered over the uninstall button when a notification blinked – a signal from the void. My tech-anarchist friend had messaged: "The rats are abandoning the ship. Try Jerboa." No link, no explanation. Just coordinates to a digital life raft.
Rain lashed against my apartment window as I thumb-scrolled through another soul-crushing feed. Ads for weight loss teas sandwiched between political screaming matches, while some algorithm kept resurrecting my ex's vacation photos. My thumb hovered over the uninstall button when a notification blinked – a signal from the void. My tech-anarchist friend had messaged: "The rats are abandoning the ship. Try Jerboa." No link, no explanation. Just coordinates to a digital life raft. -
 Elisa RingWith Elisa Ring's communication application you can easily manage, among others. your calls, change your status or phone number, and use the contacts in your phone or Ring Address Book. For use, the organization must have an Elisa Ring service and an Elisa Ring subscription.For Dual-SIM phones, in the application start-up phase, the non-ELISA SIM card must be turned off completely. This ensures that authentication is successful. Once the software authentication is complete, another SIM
Elisa RingWith Elisa Ring's communication application you can easily manage, among others. your calls, change your status or phone number, and use the contacts in your phone or Ring Address Book. For use, the organization must have an Elisa Ring service and an Elisa Ring subscription.For Dual-SIM phones, in the application start-up phase, the non-ELISA SIM card must be turned off completely. This ensures that authentication is successful. Once the software authentication is complete, another SIM -
 Rain lashed against the cafe window in Berlin as my phone buzzed violently - my sister's panicked face flashing on screen. Our mother had been rushed to hospital in Buenos Aires needing immediate surgery, and the international wire transfer system was crawling at glacial speed. Sweat mixed with condensation on my palms as I fumbled with my hardware wallet, desperately trying to recall which permutation of 24 words I'd used for this account. The seed phrase notebook? Left in my New York apartment
Rain lashed against the cafe window in Berlin as my phone buzzed violently - my sister's panicked face flashing on screen. Our mother had been rushed to hospital in Buenos Aires needing immediate surgery, and the international wire transfer system was crawling at glacial speed. Sweat mixed with condensation on my palms as I fumbled with my hardware wallet, desperately trying to recall which permutation of 24 words I'd used for this account. The seed phrase notebook? Left in my New York apartment -
 The fluorescent glare of my monitor reflected off empty coffee cups at 3AM when I first encountered the beast. There I was, knee-deep in federation protocol documentation, my fingers trembling from caffeine overload and frustration. I'd spent hours trying to debug why my instance wasn't syncing with a new art community server when that radioactive green icon caught my eye - Tusky Nightly. "Nightly" sounded like a dare. I clicked download like defusing a bomb with sweaty palms.
The fluorescent glare of my monitor reflected off empty coffee cups at 3AM when I first encountered the beast. There I was, knee-deep in federation protocol documentation, my fingers trembling from caffeine overload and frustration. I'd spent hours trying to debug why my instance wasn't syncing with a new art community server when that radioactive green icon caught my eye - Tusky Nightly. "Nightly" sounded like a dare. I clicked download like defusing a bomb with sweaty palms. -
 AOK IdentWith the \xe2\x80\x9cAOK Ident\xe2\x80\x9d app you get access to your health ID. You can register using the \xe2\x80\x9cAOK Ident\xe2\x80\x9d app and use it to log in to your AOK\xe2\x80\x99s services. By registering in the "AOK Ident" app, you have the opportunity to securely log in to other applications. For example, with the \xe2\x80\x9cAOK Ident\xe2\x80\x9d app you get access to the electronic patient file (ePA) in the \xe2\x80\x9cAOK Mein Leben\xe2\x80\x9d app. We will gr
AOK IdentWith the \xe2\x80\x9cAOK Ident\xe2\x80\x9d app you get access to your health ID. You can register using the \xe2\x80\x9cAOK Ident\xe2\x80\x9d app and use it to log in to your AOK\xe2\x80\x99s services. By registering in the "AOK Ident" app, you have the opportunity to securely log in to other applications. For example, with the \xe2\x80\x9cAOK Ident\xe2\x80\x9d app you get access to the electronic patient file (ePA) in the \xe2\x80\x9cAOK Mein Leben\xe2\x80\x9d app. We will gr -
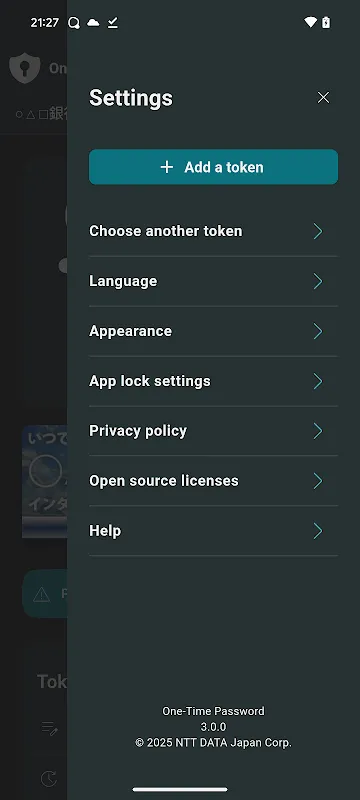 Rain lashed against the Amsterdam airport windows as I frantically tapped my phone's cracked screen. My flight boarded in 17 minutes, and the airline app demanded verification. Sweat trickled down my neck when I realized - my password manager vault had just expired. That familiar icy dread spread through my chest as I imagined missed connections, stranded luggage, and a hotel booking evaporating into digital ether. Then I remembered the tiny shield icon buried in my utilities folder.
Rain lashed against the Amsterdam airport windows as I frantically tapped my phone's cracked screen. My flight boarded in 17 minutes, and the airline app demanded verification. Sweat trickled down my neck when I realized - my password manager vault had just expired. That familiar icy dread spread through my chest as I imagined missed connections, stranded luggage, and a hotel booking evaporating into digital ether. Then I remembered the tiny shield icon buried in my utilities folder. -
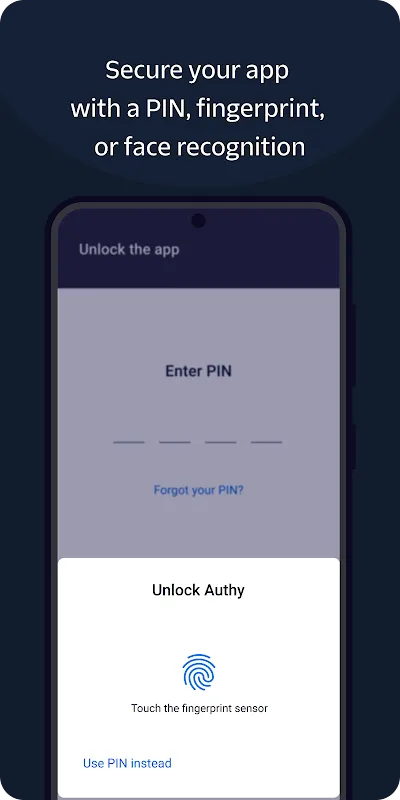 Rain lashed against the hostel window in Berlin as I stared at my dead phone, that hollow panic rising in my throat. Forty-eight hours until my flight, zero access to banking apps, and my work email demanding two-factor authentication like a digital prison guard. I'd smugly dismissed cloud backups as paranoid overkill months ago - until that moment when my charger failed in a foreign outlet and my arrogance evaporated with the battery percentage. My fingers trembled holding the hostel's loaner t
Rain lashed against the hostel window in Berlin as I stared at my dead phone, that hollow panic rising in my throat. Forty-eight hours until my flight, zero access to banking apps, and my work email demanding two-factor authentication like a digital prison guard. I'd smugly dismissed cloud backups as paranoid overkill months ago - until that moment when my charger failed in a foreign outlet and my arrogance evaporated with the battery percentage. My fingers trembled holding the hostel's loaner t -
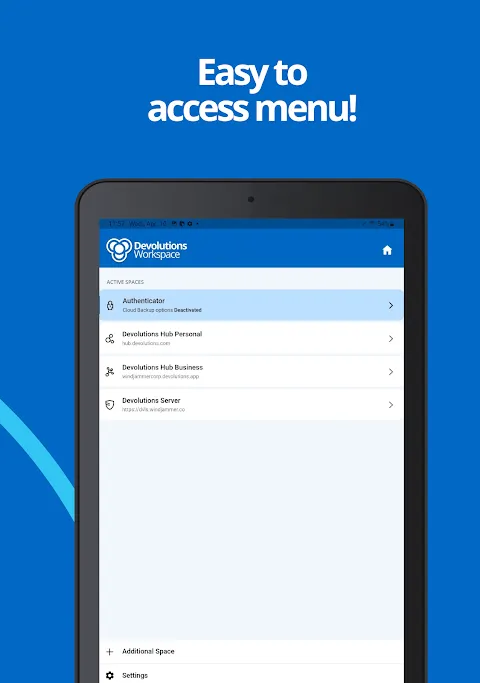 Rain lashed against my home office window when the alert screamed through my monitor - our client's payment gateway had flatlined during peak holiday sales. Icy panic shot through my veins as I scrambled across seven browser tabs, each demanding different credentials. My password manager spat out one set of keys while Google Authenticator blinked impatiently on my dying phone. When the third authentication failure locked me out of the firewall console, I nearly put my fist through the screen. Th
Rain lashed against my home office window when the alert screamed through my monitor - our client's payment gateway had flatlined during peak holiday sales. Icy panic shot through my veins as I scrambled across seven browser tabs, each demanding different credentials. My password manager spat out one set of keys while Google Authenticator blinked impatiently on my dying phone. When the third authentication failure locked me out of the firewall console, I nearly put my fist through the screen. Th -
 Rain hammered the safari jeep's roof like angry spirits as mud swallowed our tires whole. My guide Joseph whispered "simba" while pointing at amber eyes glowing in the torchlight - magnificent until I realized my wallet was drowning in a puddle outside. Fifty miles from Arusha with lions between us and civilization, cold panic slithered down my spine. The lodge demanded upfront payment for rescue, and my usual banking apps choked on the weak signal, spinning like helpless compasses. When Joseph
Rain hammered the safari jeep's roof like angry spirits as mud swallowed our tires whole. My guide Joseph whispered "simba" while pointing at amber eyes glowing in the torchlight - magnificent until I realized my wallet was drowning in a puddle outside. Fifty miles from Arusha with lions between us and civilization, cold panic slithered down my spine. The lodge demanded upfront payment for rescue, and my usual banking apps choked on the weak signal, spinning like helpless compasses. When Joseph -
 Dah Sing BankDah Sing Bank is a mobile banking application that enables users to manage their finances conveniently from their Android devices. The app combines various banking services into a single platform, making it easy for customers to perform transactions, monitor their spending, and access f
Dah Sing BankDah Sing Bank is a mobile banking application that enables users to manage their finances conveniently from their Android devices. The app combines various banking services into a single platform, making it easy for customers to perform transactions, monitor their spending, and access f -
 1Password: Password Manager1Password has been helping folks forget their passwords since 2006. Trusted by millions of people and more than 150,000 businesses, "1Password offers the best combination of features, compatibility, security, and ease of use" among password managers, according to The New Y
1Password: Password Manager1Password has been helping folks forget their passwords since 2006. Trusted by millions of people and more than 150,000 businesses, "1Password offers the best combination of features, compatibility, security, and ease of use" among password managers, according to The New Y -
 Rain lashed against the airport windows as I fumbled with my phone, hands trembling. My flight boarding pass vanished behind a fortress of authentication layers - password long forgotten, SMS code lost in roaming limbo. That familiar acid taste of panic rose in my throat when the gate agent called final boarding. Then I remembered the silent guardian in my pocket.
Rain lashed against the airport windows as I fumbled with my phone, hands trembling. My flight boarding pass vanished behind a fortress of authentication layers - password long forgotten, SMS code lost in roaming limbo. That familiar acid taste of panic rose in my throat when the gate agent called final boarding. Then I remembered the silent guardian in my pocket. -
 ADAMANT MessengerDecentralized and anonymous blockchain messenger. Independent of any governments, corporations, and developers. Distributed network infrastructure with open-source code.ANONYMOUS. Neither phone numbers nor emails are required. App has no access to the contact list or geotags, IPs are hidden from chatters.DECENTRALIZED. The ADAMANT blockchain system belongs to its users. Nobody can control, block, deactivate, restrict or censor accounts. Users take full responsibility for their c
ADAMANT MessengerDecentralized and anonymous blockchain messenger. Independent of any governments, corporations, and developers. Distributed network infrastructure with open-source code.ANONYMOUS. Neither phone numbers nor emails are required. App has no access to the contact list or geotags, IPs are hidden from chatters.DECENTRALIZED. The ADAMANT blockchain system belongs to its users. Nobody can control, block, deactivate, restrict or censor accounts. Users take full responsibility for their c -
 FaceTec DemoFaceTec Demo App - 3D Liveness & 3D Face Matching*Please Do Not Rate as a Consumer App; this is for Demo Purposes Only.FaceTec proves human Liveness, and matches 3D FaceMaps to both Photo ID\xe2\x80\x99s for Onboarding and to stored 3D FaceMaps. FaceTec has performed hundreds-of-millions of Liveness Checks for users in +170 countries.FaceTec is the only 3D Face Authenticator that has a $600,000 Spoof Bounty Program for Levels 1-5 and is Level 1&2 Certified. FaceTec has been proven in
FaceTec DemoFaceTec Demo App - 3D Liveness & 3D Face Matching*Please Do Not Rate as a Consumer App; this is for Demo Purposes Only.FaceTec proves human Liveness, and matches 3D FaceMaps to both Photo ID\xe2\x80\x99s for Onboarding and to stored 3D FaceMaps. FaceTec has performed hundreds-of-millions of Liveness Checks for users in +170 countries.FaceTec is the only 3D Face Authenticator that has a $600,000 Spoof Bounty Program for Levels 1-5 and is Level 1&2 Certified. FaceTec has been proven in -
 PIV-D Manager - Workspace ONEWorkspace ONE PIV-D Manager breaks you free from the need to carry awkward authentication hardware to access sensitive corporate resources. By integrating with various Derived Credential solution providers, PIV-D Manager leverages two-factor authentication to give you in
PIV-D Manager - Workspace ONEWorkspace ONE PIV-D Manager breaks you free from the need to carry awkward authentication hardware to access sensitive corporate resources. By integrating with various Derived Credential solution providers, PIV-D Manager leverages two-factor authentication to give you in -
 Duo MobileDuo Mobile is a mobile application developed by Duo Security that enhances the security of online logins through two-factor authentication. This app is available for the Android platform and can be easily downloaded for users looking to add an extra layer of protection to their accounts. D
Duo MobileDuo Mobile is a mobile application developed by Duo Security that enhances the security of online logins through two-factor authentication. This app is available for the Android platform and can be easily downloaded for users looking to add an extra layer of protection to their accounts. D -
 That godawful hacking sound ripped through our silent apartment at 2 AM - the kind of wet, ragged cough that shoots adrenaline straight to your temples. I found Biscuit trembling in a corner, eyes wide with animal panic, sides heaving like bellows. My hands shook so violently I dropped his vaccination papers twice before giving up, scattered documents sliding under furniture as precious seconds bled away. In that fluorescent-lit ER waiting room with its antiseptic stench, I realized our chaotic
That godawful hacking sound ripped through our silent apartment at 2 AM - the kind of wet, ragged cough that shoots adrenaline straight to your temples. I found Biscuit trembling in a corner, eyes wide with animal panic, sides heaving like bellows. My hands shook so violently I dropped his vaccination papers twice before giving up, scattered documents sliding under furniture as precious seconds bled away. In that fluorescent-lit ER waiting room with its antiseptic stench, I realized our chaotic -
 Yandex Key \xe2\x80\x93 your passwordsYandex.Key is an authenticator generating one-time passwords (OTP) for Yandex, Google, GitHub, Dropbox, Vk.com, and other services with two-factor authentication (2FA). To log in to Yandex, enter this one-time password instead of your regular password, and to si
Yandex Key \xe2\x80\x93 your passwordsYandex.Key is an authenticator generating one-time passwords (OTP) for Yandex, Google, GitHub, Dropbox, Vk.com, and other services with two-factor authentication (2FA). To log in to Yandex, enter this one-time password instead of your regular password, and to si -
 The screen flickered like a dying torch in Dudael’s deepest crypt as my rogue’s health bar plummeted to crimson. My thumb jammed against the dodge button – sticky with coffee residue – but nothing happened. "Move, damn you!" I hissed at the pixelated figure now frozen mid-leap while skeletal mages charged their death spells. Three hours of strategic positioning, resource management, and carefully timed ability rotations evaporated in that single lag spike. I nearly spiked my phone onto the subwa
The screen flickered like a dying torch in Dudael’s deepest crypt as my rogue’s health bar plummeted to crimson. My thumb jammed against the dodge button – sticky with coffee residue – but nothing happened. "Move, damn you!" I hissed at the pixelated figure now frozen mid-leap while skeletal mages charged their death spells. Three hours of strategic positioning, resource management, and carefully timed ability rotations evaporated in that single lag spike. I nearly spiked my phone onto the subwa
