encrypted access 2025-11-03T15:36:22Z
-
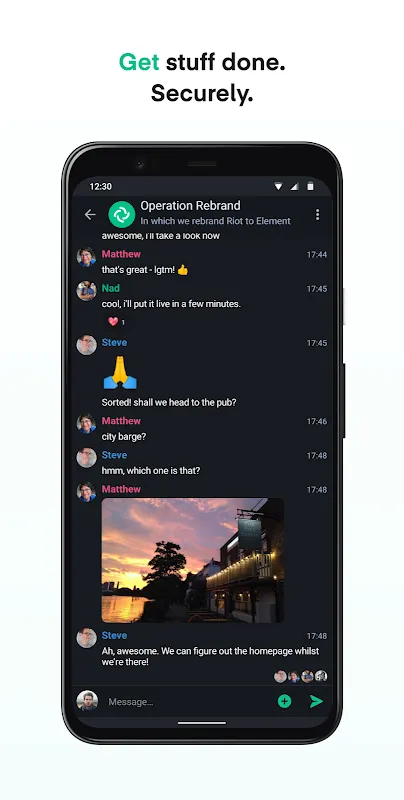 My knuckles turned bone-white gripping the coffee mug when the Slack alert blared at 3 AM – a contractor’s compromised device had leaked mockups for a fintech prototype. Cold dread slithered down my spine; our client’s $2M project hung in the balance. That week, paranoia became my shadow. Every notification felt like a tripwire, every shared file a potential grenade. I’d stare at pixelated video calls, wondering if some faceless entity was harvesting proprietary algorithms through unsecured chan
My knuckles turned bone-white gripping the coffee mug when the Slack alert blared at 3 AM – a contractor’s compromised device had leaked mockups for a fintech prototype. Cold dread slithered down my spine; our client’s $2M project hung in the balance. That week, paranoia became my shadow. Every notification felt like a tripwire, every shared file a potential grenade. I’d stare at pixelated video calls, wondering if some faceless entity was harvesting proprietary algorithms through unsecured chan -
 Rain lashed against the hotel window like angry fists as I hunched over my burner phone in Belgrade. Gunfire echoed three blocks away - ordinary Tuesday night here. My source's final message blinked: "They know my face." My fingers trembled not from cold but raw terror when opening Letstalk IMA. That distinctive red-and-black interface felt like uncocking a loaded weapon. I typed coordinates for the dead-drop location, setting the message to self-destruct 37 seconds after opening. Military-grade
Rain lashed against the hotel window like angry fists as I hunched over my burner phone in Belgrade. Gunfire echoed three blocks away - ordinary Tuesday night here. My source's final message blinked: "They know my face." My fingers trembled not from cold but raw terror when opening Letstalk IMA. That distinctive red-and-black interface felt like uncocking a loaded weapon. I typed coordinates for the dead-drop location, setting the message to self-destruct 37 seconds after opening. Military-grade -
 Schlage Mobile AccessThe Schlage Mobile Access app is developed for multifamily, commercial and institutional properties only. Commercial electronic hardware that connects to this app includes Schlage mobile enabled Control, Schlage MTB Readers, and Schlage NDEB and LEB wireless locks. Please note, residential homeowners who wish to manage Schlage Encode\xe2\x84\xa2 or Schlage Sense\xe2\x84\xa2 smart locks should use the Schlage Home app. For multifamily residents and end users: The new Schla
Schlage Mobile AccessThe Schlage Mobile Access app is developed for multifamily, commercial and institutional properties only. Commercial electronic hardware that connects to this app includes Schlage mobile enabled Control, Schlage MTB Readers, and Schlage NDEB and LEB wireless locks. Please note, residential homeowners who wish to manage Schlage Encode\xe2\x84\xa2 or Schlage Sense\xe2\x84\xa2 smart locks should use the Schlage Home app. For multifamily residents and end users: The new Schla -
 bizhub Remote AccessEnables Remote MFP panel operations, data entry and importing of scanned data using Android devices. In addition, it is possible to use the Android device address book when sending data from the MFP.[Introduction of Main Functions of Application]Panel Link:-Enables remote operation by displaying the MFP panel screen on the Android screen.Panel Link Scan:-Enables saving image data scanned using the MFP to the connected Android device.It is possible to select PDF and Compact P
bizhub Remote AccessEnables Remote MFP panel operations, data entry and importing of scanned data using Android devices. In addition, it is possible to use the Android device address book when sending data from the MFP.[Introduction of Main Functions of Application]Panel Link:-Enables remote operation by displaying the MFP panel screen on the Android screen.Panel Link Scan:-Enables saving image data scanned using the MFP to the connected Android device.It is possible to select PDF and Compact P -
 Absolute Secure AccessBeginning with version 12.70, NetMotion Mobility is rebranded as Absolute Secure Access. Software and documentation reflect the new naming, including graphics, icons, fonts, and color schemes. The Absolute Secure Access product portfolio provides resilient network connectivity for users to securely access critical resources in the public cloud, private data centers, and on-premises. These products allow users to transition from traditional VPN to a resilient Zero Trust appr
Absolute Secure AccessBeginning with version 12.70, NetMotion Mobility is rebranded as Absolute Secure Access. Software and documentation reflect the new naming, including graphics, icons, fonts, and color schemes. The Absolute Secure Access product portfolio provides resilient network connectivity for users to securely access critical resources in the public cloud, private data centers, and on-premises. These products allow users to transition from traditional VPN to a resilient Zero Trust appr -
 OpenItem Access ControlOpenItem Access Control App for residents. Once registered residents may invite visitors using their contacts on their phone. The app provides the functionality to send invitations via SMS, iMessage or WhatsApp.Visitors then provide security with the PAC ( Personal Access Code
OpenItem Access ControlOpenItem Access Control App for residents. Once registered residents may invite visitors using their contacts on their phone. The app provides the functionality to send invitations via SMS, iMessage or WhatsApp.Visitors then provide security with the PAC ( Personal Access Code -
 CFC Mobile AccessCFC Mobile Access is a free service offered to cardholders of:\xc2\xb7 The Verve\xc2\xae Mastercard\xc2\xae\xc2\xb7 The Reflex\xc2\xae Mastercard\xc2\xae\xc2\xb7 The Surge\xc2\xae Mastercard\xc2\xae\xc2\xb7 The FIT\xe2\x84\xa2 Mastercard\xc2\xae\xc2\xb7 The Matrix\xc2\xae Mastercard
CFC Mobile AccessCFC Mobile Access is a free service offered to cardholders of:\xc2\xb7 The Verve\xc2\xae Mastercard\xc2\xae\xc2\xb7 The Reflex\xc2\xae Mastercard\xc2\xae\xc2\xb7 The Surge\xc2\xae Mastercard\xc2\xae\xc2\xb7 The FIT\xe2\x84\xa2 Mastercard\xc2\xae\xc2\xb7 The Matrix\xc2\xae Mastercard -
 dormakaba mobile accessWith the dormakaba Mobile Access App you receive access permissions to your smartphone, which were provided by dormakaba access systems. For effective access, interfaces such as Bluetooth Low Energy (BLE) or Near Field Communication (NFC) are used.NOTE! To ensure that the smar
dormakaba mobile accessWith the dormakaba Mobile Access App you receive access permissions to your smartphone, which were provided by dormakaba access systems. For effective access, interfaces such as Bluetooth Low Energy (BLE) or Near Field Communication (NFC) are used.NOTE! To ensure that the smar -
 Remote Access PlusRemote into your computer while you're on the move!ManageEngine Remote Access Plus helps you access remote computers irrespective of their location and lets you resolve troubleshooting requests at lightning speed. Available both on cloud and on-premises, Remote Access Plus can be d
Remote Access PlusRemote into your computer while you're on the move!ManageEngine Remote Access Plus helps you access remote computers irrespective of their location and lets you resolve troubleshooting requests at lightning speed. Available both on cloud and on-premises, Remote Access Plus can be d -
 Citrix Secure AccessCitrix Secure Access (formerly Citrix SSO) app enables secure access to business critical applications, virtual desktops, and corporate data from anywhere at any time, providing an optimal user experience with the NetScaler Gateway.Secure Access features:\xe2\x80\xa2 Full layer 3
Citrix Secure AccessCitrix Secure Access (formerly Citrix SSO) app enables secure access to business critical applications, virtual desktops, and corporate data from anywhere at any time, providing an optimal user experience with the NetScaler Gateway.Secure Access features:\xe2\x80\xa2 Full layer 3 -
 Access Care PlanningFormerly Mobizio, now Access Care Planning. Access Care Planning enables organisations to replace their paper processes with mobile solutions that work with or without a network connection. Easy to configure, Access Care Planning can be tailored to specific business needs without
Access Care PlanningFormerly Mobizio, now Access Care Planning. Access Care Planning enables organisations to replace their paper processes with mobile solutions that work with or without a network connection. Easy to configure, Access Care Planning can be tailored to specific business needs without -
 Hospitality Mobile AccessHospitality Mobile Access is an application developed by ASSA ABLOY that allows users to check in to their hotel rooms prior to their arrival and receive a mobile key directly on their smartphones. This app utilizes advanced technology to facilitate a seamless hotel experien
Hospitality Mobile AccessHospitality Mobile Access is an application developed by ASSA ABLOY that allows users to check in to their hotel rooms prior to their arrival and receive a mobile key directly on their smartphones. This app utilizes advanced technology to facilitate a seamless hotel experien -
 Genea Mobile AccessWith Genea Mobile Access, your smartphone becomes your keycard. Simply tap your phone to a Genea-enabled reader, the same way you would a keycard, and the door will unlock. You may also have the option to open the door or gate from a distance by twisting your phone.\xe2\x80\xa2 No
Genea Mobile AccessWith Genea Mobile Access, your smartphone becomes your keycard. Simply tap your phone to a Genea-enabled reader, the same way you would a keycard, and the door will unlock. You may also have the option to open the door or gate from a distance by twisting your phone.\xe2\x80\xa2 No -
 I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a
I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a -
 I remember the icy dread crawling up my spine when targeted ads started mocking me. There it was - the exact hiking boot I'd photographed for my dying father's bucket list trip, plastered across every platform after I'd shared it via mainstream messengers. That night, I tore through privacy forums like a madwoman, fingers trembling against my keyboard until dawn's pale light revealed Element X. The promise of true data sovereignty felt like finding an unbreakable vault in a world of cardboard lo
I remember the icy dread crawling up my spine when targeted ads started mocking me. There it was - the exact hiking boot I'd photographed for my dying father's bucket list trip, plastered across every platform after I'd shared it via mainstream messengers. That night, I tore through privacy forums like a madwoman, fingers trembling against my keyboard until dawn's pale light revealed Element X. The promise of true data sovereignty felt like finding an unbreakable vault in a world of cardboard lo -
 Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv.
Sweat glued my shirt to the backseat vinyl as the unmarked sedan trailed my taxi through Istanbul's winding alleys. Three days earlier, I'd uncovered the shipping manifests proving illegal arms transfers - digital evidence now burning a hole in my encrypted drive. Every shadow felt like a sniper's perch when my burner phone vibrated with a new threat: "Stop digging or lose more than your story." That's when I remembered the encrypted messenger my source swore by last month in Kyiv. -
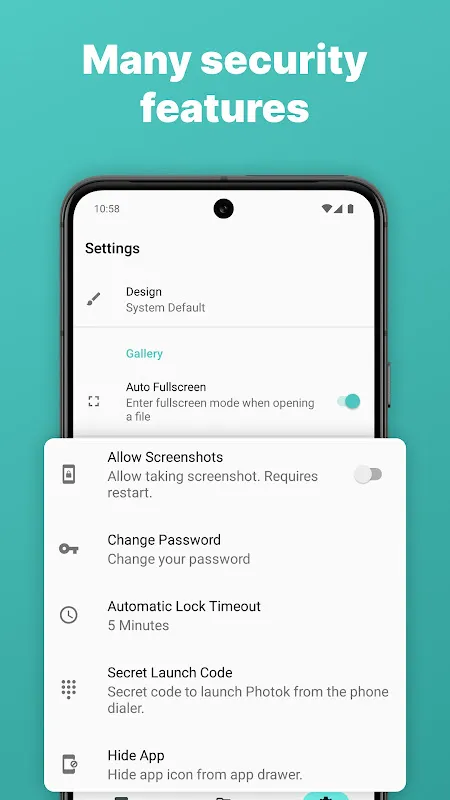 The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima
The champagne flute nearly slipped from my palm when Dave swiped left on my Istanbul sunset shots. "Whoa, what's this?" he murmured, squinting at my phone screen. My blood turned to ice as I recognized the tax return document I'd photographed for urgent reference. That split-second exposure felt like walking naked through Times Square. I'd trusted Android's native gallery like a fool, letting personal grenades nestle between harmless cat memes and holiday snaps. For three sleepless nights, I ima -
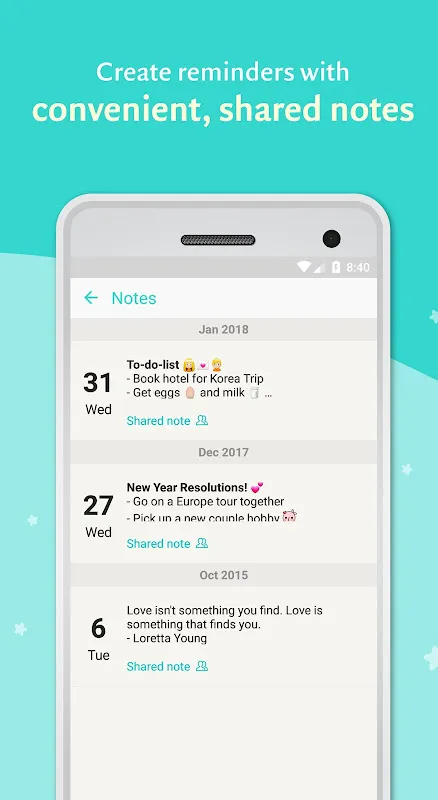 Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw
Rain lashed against the Bangkok hotel window as I frantically swiped through three different cloud services. Our fifth anniversary dinner reservation confirmation had vanished into the digital ether - again. My knuckles whitened around the phone, that familiar acid burn of technological betrayal rising in my throat. Across thirteen time zones, Alex would be waking to disappointment because our love couldn't survive Google's algorithm. That's when my trembling fingers discovered Between tucked aw -
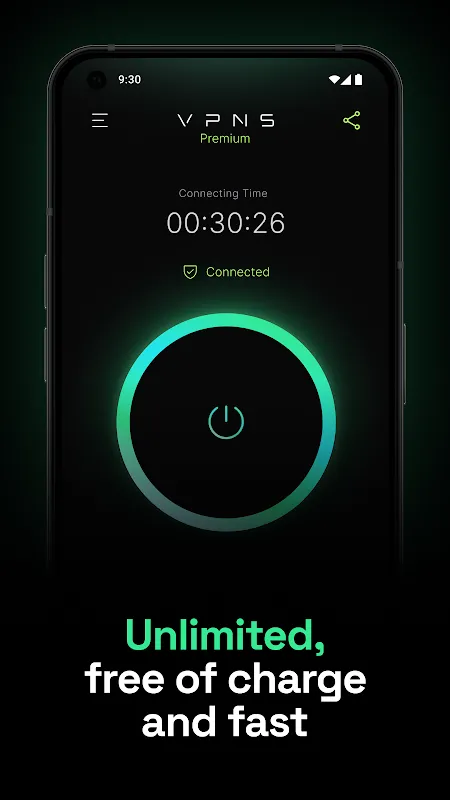 Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious
Rain lashed against the café window as I frantically refreshed my banking app on Berlin's free U-Bahn Wi-Fi. My fingertips turned icy when that dreaded red shield icon appeared mid-transfer - the universal symbol of digital vulnerability. In that suspended heartbeat between tapping "confirm" and seeing the security alert, I felt naked. Exposed. A sitting duck in a digital shooting gallery. My 8,000 euro apartment deposit hung in the digital void while commuters sipped lattes around me, oblivious -
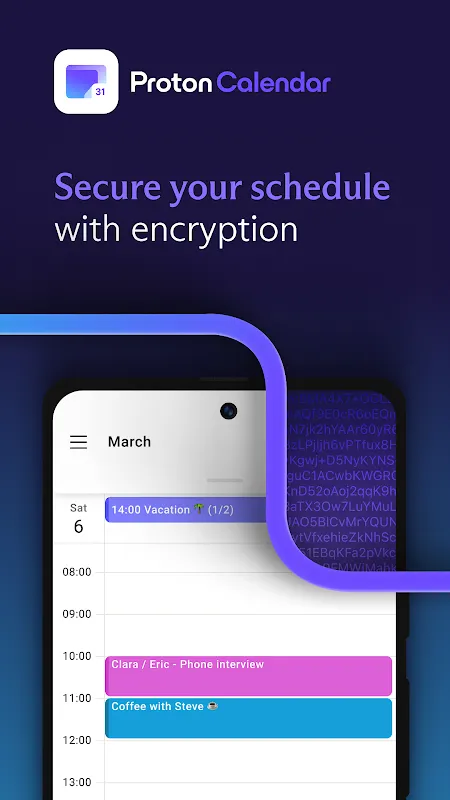 The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality.
The cracked pavement vibrated beneath my worn sneakers as I sprinted toward the safehouse, rain soaking through my jacket like icy needles. My burner phone buzzed - third alert this hour. As an investigative reporter documenting war crimes in Eastern Europe, every digital footprint could be my death warrant. That's when end-to-end encrypted scheduling became my oxygen mask in this suffocating reality.