authentication tech 2025-11-10T23:56:42Z
-
 Forty minutes after the convention doors swung open, I was drowning in sensory overload. Sweaty bodies pressed against me in the exhibit hall, neon lights strobing off cosplay armor while bass-heavy remixes of game soundtracks vibrated through my ribcage. My crumpled paper schedule – already smeared with taco grease from breakfast – showed three overlapping meetups starting NOW. That's when my thumb smashed the TwitchCon app icon in pure panic, desperation overriding my tech skepticism. What hap
Forty minutes after the convention doors swung open, I was drowning in sensory overload. Sweaty bodies pressed against me in the exhibit hall, neon lights strobing off cosplay armor while bass-heavy remixes of game soundtracks vibrated through my ribcage. My crumpled paper schedule – already smeared with taco grease from breakfast – showed three overlapping meetups starting NOW. That's when my thumb smashed the TwitchCon app icon in pure panic, desperation overriding my tech skepticism. What hap -
 Protege ConfigProtege Config provides the ability for installers to configure ICT TSEC readers(requires firmware version 1.04.254 or higher) without the need for extra hardware. Configurations can be setup and saved on a per profile (site) basis.Important:Please ensure that Protege Mobile is not run
Protege ConfigProtege Config provides the ability for installers to configure ICT TSEC readers(requires firmware version 1.04.254 or higher) without the need for extra hardware. Configurations can be setup and saved on a per profile (site) basis.Important:Please ensure that Protege Mobile is not run -
 That sinking feeling hit when I noticed the odd login alert - someone halfway across the globe trying to access my trading account. My fingers trembled as I canceled transactions just in time, cold sweat tracing my spine. All those nights checking and rechecking my phone's authenticator app suddenly felt like guarding a vault with tissue paper. The digital locks I trusted could be shattered by a single phishing link or malware-infected update. I needed something physical, something untouchable b
That sinking feeling hit when I noticed the odd login alert - someone halfway across the globe trying to access my trading account. My fingers trembled as I canceled transactions just in time, cold sweat tracing my spine. All those nights checking and rechecking my phone's authenticator app suddenly felt like guarding a vault with tissue paper. The digital locks I trusted could be shattered by a single phishing link or malware-infected update. I needed something physical, something untouchable b -
 \xd0\x9a\xd0\xbe\xd0\xbd\xd1\x82\xd1\x83\xd1\x80.\xd0\x9a\xd0\xbe\xd0\xbd\xd0\xbd\xd0\xb5\xd0\xba\xd1\x82Data protectionConnect generates two-factor authentication codes to further protect your account. When using two-factor authentication (2FA), to log into your account you must enter not only a pa
\xd0\x9a\xd0\xbe\xd0\xbd\xd1\x82\xd1\x83\xd1\x80.\xd0\x9a\xd0\xbe\xd0\xbd\xd0\xbd\xd0\xb5\xd0\xba\xd1\x82Data protectionConnect generates two-factor authentication codes to further protect your account. When using two-factor authentication (2FA), to log into your account you must enter not only a pa -
 Rain lashed against my windshield like pebbles as I white-knuckled the steering wheel through downtown gridlock. The insulated box beside me held bone marrow destined for a leukemia patient - viable for just six more hours. My old three-ring binder lay waterlogged on the passenger seat, ink bleeding through shipping manifests. That’s when dispatch pinged: "Priority reroute to Children’s Hospital." Panic seized my throat. Scrambling for a pen with greasy fingers from roadside tacos, I nearly side
Rain lashed against my windshield like pebbles as I white-knuckled the steering wheel through downtown gridlock. The insulated box beside me held bone marrow destined for a leukemia patient - viable for just six more hours. My old three-ring binder lay waterlogged on the passenger seat, ink bleeding through shipping manifests. That’s when dispatch pinged: "Priority reroute to Children’s Hospital." Panic seized my throat. Scrambling for a pen with greasy fingers from roadside tacos, I nearly side -
 Rain lashed against my studio window as I stared at lines of Python mocking me from the screen. Three days. Seventy-two hours wrestling with this authentication module that kept rejecting valid tokens like a bouncer at an exclusive club. My coffee had gone cold, my neck stiff as rebar, and that familiar acid-burn of frustration bubbled in my chest – the kind that makes you want to hurl your mechanical keyboard through drywall. I’d been here before; that limbo where logic evaporates and imposter
Rain lashed against my studio window as I stared at lines of Python mocking me from the screen. Three days. Seventy-two hours wrestling with this authentication module that kept rejecting valid tokens like a bouncer at an exclusive club. My coffee had gone cold, my neck stiff as rebar, and that familiar acid-burn of frustration bubbled in my chest – the kind that makes you want to hurl your mechanical keyboard through drywall. I’d been here before; that limbo where logic evaporates and imposter -
 Anchor WalletAnchor is a next-generation authenticator powered by blockchain technology.Securely sign in to applications using your blockchain accounts and execute smart contract actions with ease.Supported EOSIO networks:\xe2\x80\xa2 EOS\xe2\x80\xa2 WAX\xe2\x80\xa2 Telos\xe2\x80\xa2 Proton\xe2\x80\xa2 FIOAnchor Wallet is a Greymass project. Connect with us on Twitter @greymass, visit our website at https://greymass.com, or join us on the forums at https://forums.eoscommunity.org.
Anchor WalletAnchor is a next-generation authenticator powered by blockchain technology.Securely sign in to applications using your blockchain accounts and execute smart contract actions with ease.Supported EOSIO networks:\xe2\x80\xa2 EOS\xe2\x80\xa2 WAX\xe2\x80\xa2 Telos\xe2\x80\xa2 Proton\xe2\x80\xa2 FIOAnchor Wallet is a Greymass project. Connect with us on Twitter @greymass, visit our website at https://greymass.com, or join us on the forums at https://forums.eoscommunity.org. -
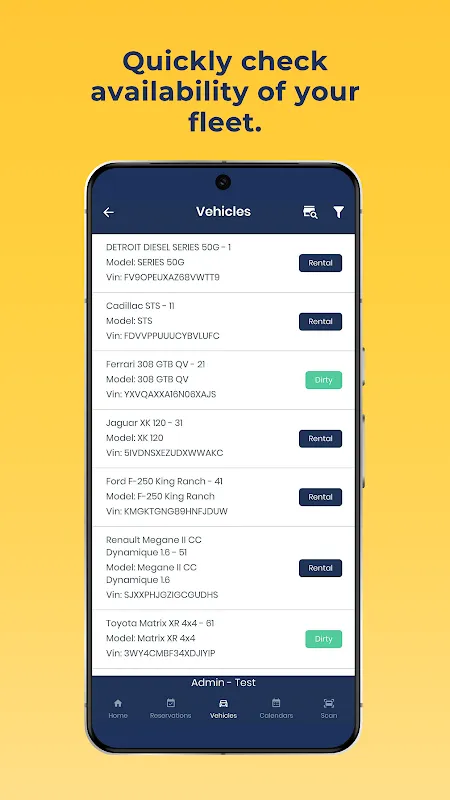 That sweltering Tuesday at the desert outpost rental station nearly broke me. My fingers slipped on damp paperwork as a queue of overheated travelers glared, their plane departures ticking away. One businessman actually threw his keys at the counter when I asked him to initial clause 7B on the carbon copy - the form's tiny text swimming before my sweat-stung eyes. That's when I remembered the trial download blinking on my work tablet: HQ's mobile solution. With trembling hands, I tapped it open,
That sweltering Tuesday at the desert outpost rental station nearly broke me. My fingers slipped on damp paperwork as a queue of overheated travelers glared, their plane departures ticking away. One businessman actually threw his keys at the counter when I asked him to initial clause 7B on the carbon copy - the form's tiny text swimming before my sweat-stung eyes. That's when I remembered the trial download blinking on my work tablet: HQ's mobile solution. With trembling hands, I tapped it open, -
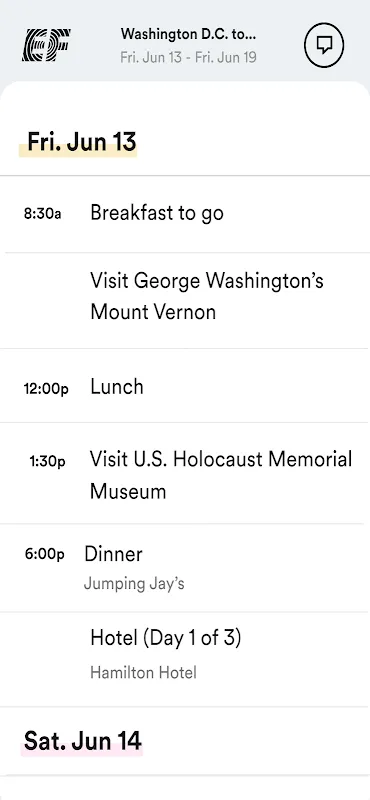 Thirty pairs of soaking Converse squeaked across the Termini station floor as I counted heads for the third time. Marco's insulin pump alarm pierced the humid air while Sofia sobbed over her waterlogged sketchbook - casualties of Rome's biblical downpour that canceled our Colosseum tour. My paper itinerary dissolved into blue pulp in my hands, the ink bleeding like my confidence. That damp panic tasted metallic, like licking a battery. Forty-eight hours into leading middle schoolers through hist
Thirty pairs of soaking Converse squeaked across the Termini station floor as I counted heads for the third time. Marco's insulin pump alarm pierced the humid air while Sofia sobbed over her waterlogged sketchbook - casualties of Rome's biblical downpour that canceled our Colosseum tour. My paper itinerary dissolved into blue pulp in my hands, the ink bleeding like my confidence. That damp panic tasted metallic, like licking a battery. Forty-eight hours into leading middle schoolers through hist -
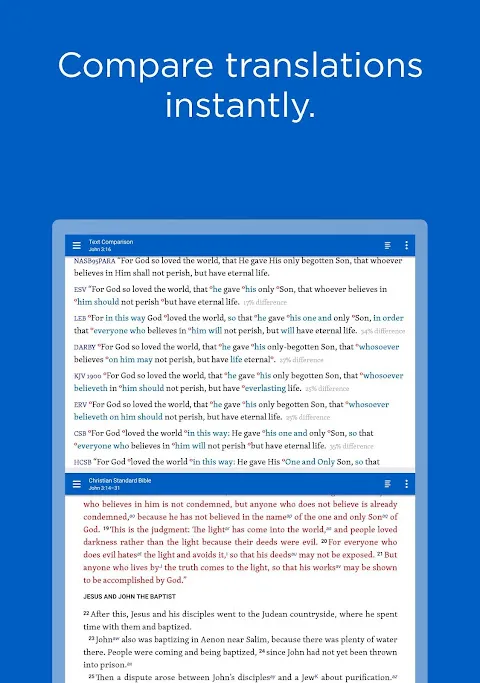 The cracked leather of my backpack felt like it was melting onto my shoulders as I trudged through the Kalahari heat, sand gritting between my teeth with every gust of wind. I'd volunteered to teach scripture at this remote Namibian village school, armed with nothing but idealism and a single dog-eared Bible. When Pastor Mbeke asked me to explain Paul's thorn in the flesh using early church perspectives, panic seized my throat. My theological library? A continent away. My internet? Slower than a
The cracked leather of my backpack felt like it was melting onto my shoulders as I trudged through the Kalahari heat, sand gritting between my teeth with every gust of wind. I'd volunteered to teach scripture at this remote Namibian village school, armed with nothing but idealism and a single dog-eared Bible. When Pastor Mbeke asked me to explain Paul's thorn in the flesh using early church perspectives, panic seized my throat. My theological library? A continent away. My internet? Slower than a -
 It was one of those heart-pounding moments that make you question your career choices. I was holed up in a dimly lit hotel room in Berlin, the rain tapping insistently against the window, while my laptop screen glared back with a spreadsheet that could make or break our quarterly earnings report. The numbers were bleeding red, and I needed to get this sensitive financial data to our CFO within the hour—but every attempt to email it was blocked by our corporate security protocols. My palms were s
It was one of those heart-pounding moments that make you question your career choices. I was holed up in a dimly lit hotel room in Berlin, the rain tapping insistently against the window, while my laptop screen glared back with a spreadsheet that could make or break our quarterly earnings report. The numbers were bleeding red, and I needed to get this sensitive financial data to our CFO within the hour—but every attempt to email it was blocked by our corporate security protocols. My palms were s -
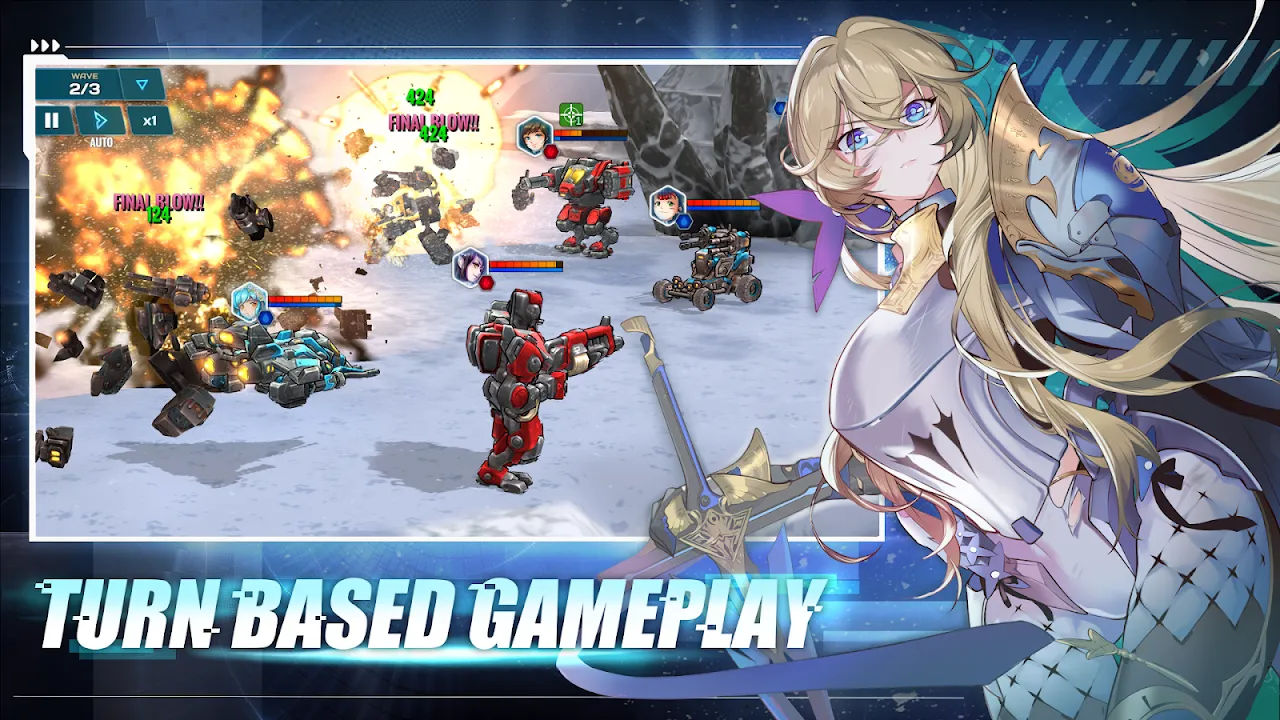 Rain smeared my apartment windows like cheap watercolors that Tuesday evening, mirroring the blur of another identical RPG grind on my phone. My thumb moved on muscle memory—tap, swipe, collect virtual trash—while my brain screamed into the void. Four months of this. Four months of cloned dragons, predictable loot boxes, and characters with all the personality of drying paint. I’d nearly chucked my phone into the ramen bowl when an ad flickered: chrome-plated legs, neon-pink hair, and a laser ca
Rain smeared my apartment windows like cheap watercolors that Tuesday evening, mirroring the blur of another identical RPG grind on my phone. My thumb moved on muscle memory—tap, swipe, collect virtual trash—while my brain screamed into the void. Four months of this. Four months of cloned dragons, predictable loot boxes, and characters with all the personality of drying paint. I’d nearly chucked my phone into the ramen bowl when an ad flickered: chrome-plated legs, neon-pink hair, and a laser ca -
 Another soul-crushing Wednesday. My cramped apartment smelled of stale coffee and defeat as Excel sheets blurred before my eyes. That's when I swiped right on destiny - or rather, Epic Mecha Girls glowing like neon salvation in the app store. Not expecting much, I tapped download while microwaving another sad dinner. Big mistake. The moment those laser cannons roared through my cheap earbuds, my lukewarm ramen bowl became a forgotten relic. Suddenly I wasn't Dave the spreadsheet jockey - I was C
Another soul-crushing Wednesday. My cramped apartment smelled of stale coffee and defeat as Excel sheets blurred before my eyes. That's when I swiped right on destiny - or rather, Epic Mecha Girls glowing like neon salvation in the app store. Not expecting much, I tapped download while microwaving another sad dinner. Big mistake. The moment those laser cannons roared through my cheap earbuds, my lukewarm ramen bowl became a forgotten relic. Suddenly I wasn't Dave the spreadsheet jockey - I was C -
 Digidentity WalletManage your digital identity effortlessly with the Digidentity Wallet. Log in with ease while at the highest levels of assurance. Sign your documents with qualified e-signatures (QES). Explore our wallet and it\xe2\x80\x99s services. Stay in control of your personal data.About Digi
Digidentity WalletManage your digital identity effortlessly with the Digidentity Wallet. Log in with ease while at the highest levels of assurance. Sign your documents with qualified e-signatures (QES). Explore our wallet and it\xe2\x80\x99s services. Stay in control of your personal data.About Digi -
 Rain lashed against the windshield as I sped down the highway, knuckles white on the steering wheel. Another frantic call from a tenant—"The cleaner can't get in!"—and I was racing across town like a medieval courier delivering scrolls. My glove compartment rattled with thirty-seven keys, each representing a moment of vulnerability. That night, soaked and apologizing to a furious Airbnb guest stranded in the storm, I finally broke. Physical keys weren't just inconvenient; they were emotional lan
Rain lashed against the windshield as I sped down the highway, knuckles white on the steering wheel. Another frantic call from a tenant—"The cleaner can't get in!"—and I was racing across town like a medieval courier delivering scrolls. My glove compartment rattled with thirty-seven keys, each representing a moment of vulnerability. That night, soaked and apologizing to a furious Airbnb guest stranded in the storm, I finally broke. Physical keys weren't just inconvenient; they were emotional lan -
 The airport departure board flickered as I frantically dug through my backpack, fingers greasy from a hurried breakfast croissant. My flight was boarding in 15 minutes, and my noise-canceling headphones—critical armor against crying babies and engine roars—remained stubbornly disconnected. Sweat trickled down my neck as I stabbed at my phone like a woodpecker on meth: Settings > Bluetooth > Scan > Pair > Authentication Failed. Again. That familiar cocktail of rage and panic bubbled in my throat
The airport departure board flickered as I frantically dug through my backpack, fingers greasy from a hurried breakfast croissant. My flight was boarding in 15 minutes, and my noise-canceling headphones—critical armor against crying babies and engine roars—remained stubbornly disconnected. Sweat trickled down my neck as I stabbed at my phone like a woodpecker on meth: Settings > Bluetooth > Scan > Pair > Authentication Failed. Again. That familiar cocktail of rage and panic bubbled in my throat -
 CyberArk IdentityCyberArk Identity is a mobile application designed to provide users with secure access to organizational applications and resources on Android devices. This app is also known for its functionality in facilitating single sign-on (SSO) access, which allows users to log into multiple c
CyberArk IdentityCyberArk Identity is a mobile application designed to provide users with secure access to organizational applications and resources on Android devices. This app is also known for its functionality in facilitating single sign-on (SSO) access, which allows users to log into multiple c -
 Rain lashed against the airport windows as I frantically swiped through my phone, the glow illuminating panic-sweat on my forehead. Somewhere over the Atlantic, a hacker was methodically dismantling my life. Email notifications flooded in - password reset requests for banking apps, social media, even my smart home system. Each ping was a detonation in the hollow pit of my stomach. I'd become that cautionary tale IT departments whisper about during onboarding, the idiot who reused passwords acros
Rain lashed against the airport windows as I frantically swiped through my phone, the glow illuminating panic-sweat on my forehead. Somewhere over the Atlantic, a hacker was methodically dismantling my life. Email notifications flooded in - password reset requests for banking apps, social media, even my smart home system. Each ping was a detonation in the hollow pit of my stomach. I'd become that cautionary tale IT departments whisper about during onboarding, the idiot who reused passwords acros -
 Rain lashed against the taxi window as I fumbled with trembling fingers, trying to access the acquisition documents before my meeting with VentureX. My throat tightened when the banking app demanded a security token I'd left charging on my hotel nightstand. Panic rose like bile - years of negotiations about to collapse because of a forgotten plastic dongle. That's when I remembered the biometric authentication I'd casually enabled in TuID weeks earlier. With one trembling thumb press on my phone
Rain lashed against the taxi window as I fumbled with trembling fingers, trying to access the acquisition documents before my meeting with VentureX. My throat tightened when the banking app demanded a security token I'd left charging on my hotel nightstand. Panic rose like bile - years of negotiations about to collapse because of a forgotten plastic dongle. That's when I remembered the biometric authentication I'd casually enabled in TuID weeks earlier. With one trembling thumb press on my phone
