cybersecurity tool 2025-11-06T23:53:40Z
-
 DarktraceDarktrace is a cybersecurity application designed to enhance threat detection and response capabilities for users on the go. This app allows individuals to remain connected to their Darktrace deployment, utilizing advanced technologies known as Darktrace DETECT and Darktrace RESPOND. Available for the Android platform, users can download Darktrace to receive real-time notifications about potential threats and activate AI-driven autonomous responses from their mobile devices.The primary
DarktraceDarktrace is a cybersecurity application designed to enhance threat detection and response capabilities for users on the go. This app allows individuals to remain connected to their Darktrace deployment, utilizing advanced technologies known as Darktrace DETECT and Darktrace RESPOND. Available for the Android platform, users can download Darktrace to receive real-time notifications about potential threats and activate AI-driven autonomous responses from their mobile devices.The primary -
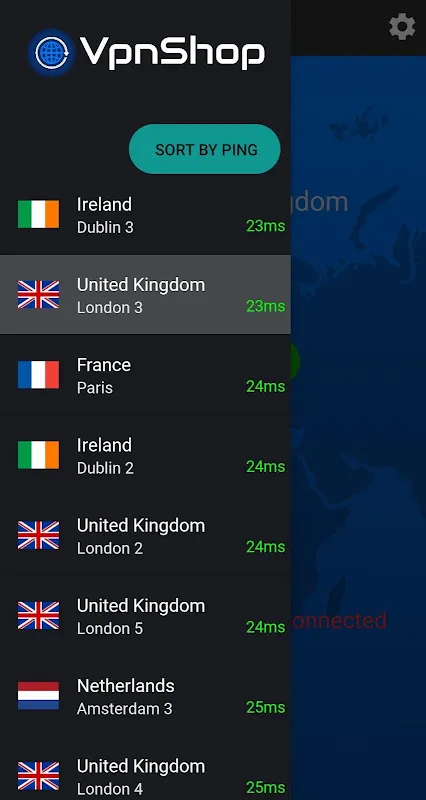 Adrenaline spiked through my veins when the browser notification popped up: "Unencrypted connection exposing financial documents." I'd just uploaded merger details over Frankfurt Airport's free Wi-Fi, my fingertips still humming from frantic typing. Across the crowded terminal, some script kiddie was probably salivating over our seven-figure acquisition plans. That's when muscle memory took over - two taps awakened my encrypted guardian. Within seconds, the ominous notification vanished like smo
Adrenaline spiked through my veins when the browser notification popped up: "Unencrypted connection exposing financial documents." I'd just uploaded merger details over Frankfurt Airport's free Wi-Fi, my fingertips still humming from frantic typing. Across the crowded terminal, some script kiddie was probably salivating over our seven-figure acquisition plans. That's when muscle memory took over - two taps awakened my encrypted guardian. Within seconds, the ominous notification vanished like smo -
 Bot Changer VPNBot Changer VPN is Ultra fast VPN service. Bot Changer VPN is the ultimate Android VPN. It is a 100% unlimited VPN that does not require any type of registration.Bot Changer VPN is completely anonymous. All of your traffic is encrypted while VPN is on.Bot Changer VPN protects your privacy and identity and allows you to browse the web anonymously without fear of being tracked.How does Bot Changer VPN Work?Bot Changer VPN encrypts your data and safely connects you to any web site or
Bot Changer VPNBot Changer VPN is Ultra fast VPN service. Bot Changer VPN is the ultimate Android VPN. It is a 100% unlimited VPN that does not require any type of registration.Bot Changer VPN is completely anonymous. All of your traffic is encrypted while VPN is on.Bot Changer VPN protects your privacy and identity and allows you to browse the web anonymously without fear of being tracked.How does Bot Changer VPN Work?Bot Changer VPN encrypts your data and safely connects you to any web site or -
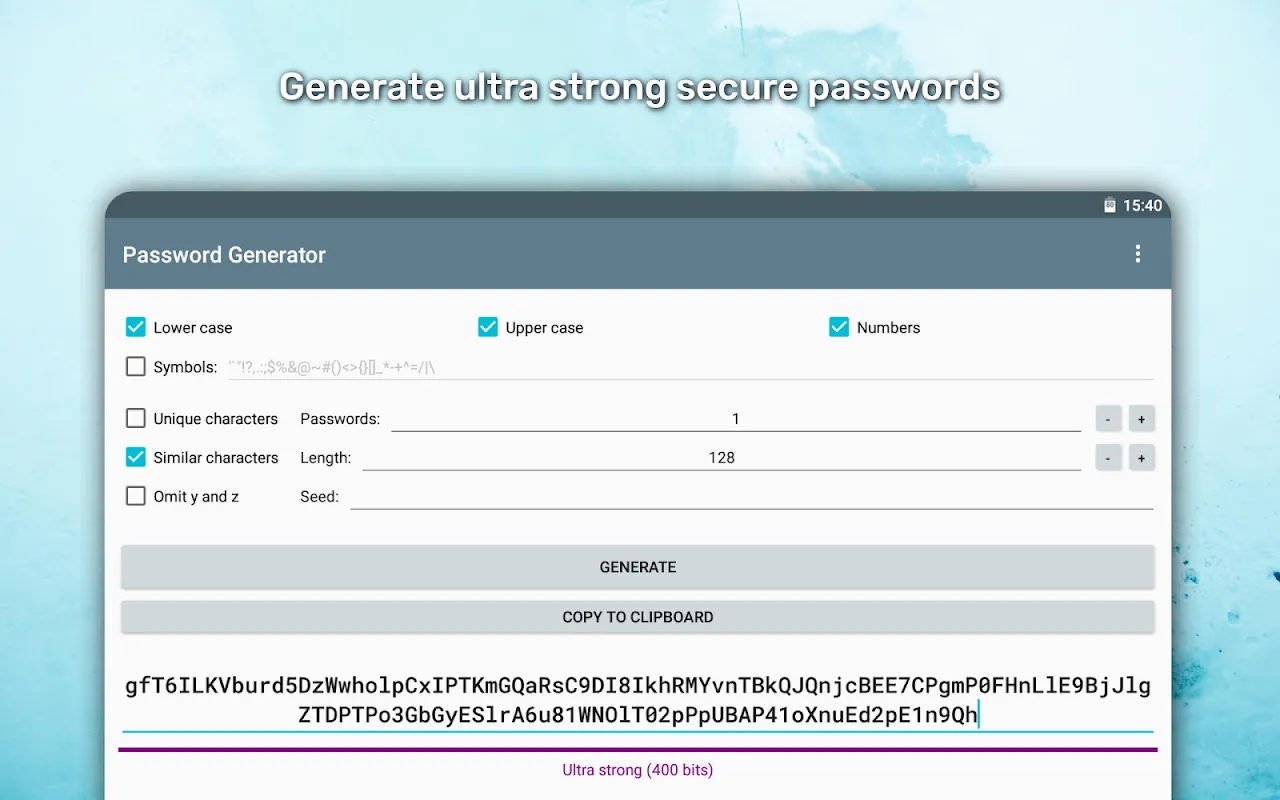 Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu
Rain lashed against my apartment window when the notification hit – "Suspicious login attempt: Russia." My throat tightened. I’d reused that password everywhere: bank, email, even my damn cloud storage full of family photos. Scrambling for my laptop, I typed frantically, only to be greeted by the icy "Invalid Password" screen. That’s when my fingers started trembling. I’d ignored warnings for years, patching together birthdays and pet names like digital duct tape. Now, staring at the flashing cu -
 Rain lashed against my apartment windows like a thousand tiny hackers probing for vulnerabilities. I'd just spent eight hours reviewing firewall logs – real-world cybersecurity that felt less like digital warfare and more like watching paint dry on server racks. My coffee had gone cold three times, each reheating a sad ritual mirroring the monotony of threat alerts blinking across dual monitors. That's when the notification appeared: "Your underground botnet awaits deployment." Not on my work da
Rain lashed against my apartment windows like a thousand tiny hackers probing for vulnerabilities. I'd just spent eight hours reviewing firewall logs – real-world cybersecurity that felt less like digital warfare and more like watching paint dry on server racks. My coffee had gone cold three times, each reheating a sad ritual mirroring the monotony of threat alerts blinking across dual monitors. That's when the notification appeared: "Your underground botnet awaits deployment." Not on my work da -
 Rain lashed against the boarded windows of Willowbrook Asylum as my flashlight beam cut through dust motes dancing in the oppressive darkness. I gripped my phone tighter when a guttural whisper seemed to crawl from the decaying nurses' station - not just in my ears, but vibrating through the Ghost Hunting Tools interface. This wasn't my first paranormal investigation, but it was the first time an app made my throat constrict with primal dread. Earlier that evening, I'd scoffed at my partner Liam
Rain lashed against the boarded windows of Willowbrook Asylum as my flashlight beam cut through dust motes dancing in the oppressive darkness. I gripped my phone tighter when a guttural whisper seemed to crawl from the decaying nurses' station - not just in my ears, but vibrating through the Ghost Hunting Tools interface. This wasn't my first paranormal investigation, but it was the first time an app made my throat constrict with primal dread. Earlier that evening, I'd scoffed at my partner Liam -
 Sweat stung my eyes as server alarms screamed into the humid darkness of the data center. Forty-two degrees Celsius and climbing – I could feel the heat radiating through my boots as racks of financial transaction servers threatened to melt down. My palms left damp streaks on the control panel while corporate security barked updates in my earpiece: "Twenty minutes until trading halt. Fix this or we lose seven figures per minute." That's when my trembling fingers found the cracked screen of my sa
Sweat stung my eyes as server alarms screamed into the humid darkness of the data center. Forty-two degrees Celsius and climbing – I could feel the heat radiating through my boots as racks of financial transaction servers threatened to melt down. My palms left damp streaks on the control panel while corporate security barked updates in my earpiece: "Twenty minutes until trading halt. Fix this or we lose seven figures per minute." That's when my trembling fingers found the cracked screen of my sa -
 Metal jingled against my hipbone like a jailer's ring as I raced between properties that Tuesday. Four guest turnovers, three lost key incidents, and one locksmith invoice that made my eyes water – this was my "vacation" rental reality. The scent of bleach clung to my hair while sweat pooled under the security fob digging into my palm. That crumpled envelope? Mrs. Henderson's 2am arrival instructions. My handwriting blurred through exhaustion: "Rock under ceramic frog... code 4721... call if iss
Metal jingled against my hipbone like a jailer's ring as I raced between properties that Tuesday. Four guest turnovers, three lost key incidents, and one locksmith invoice that made my eyes water – this was my "vacation" rental reality. The scent of bleach clung to my hair while sweat pooled under the security fob digging into my palm. That crumpled envelope? Mrs. Henderson's 2am arrival instructions. My handwriting blurred through exhaustion: "Rock under ceramic frog... code 4721... call if iss -
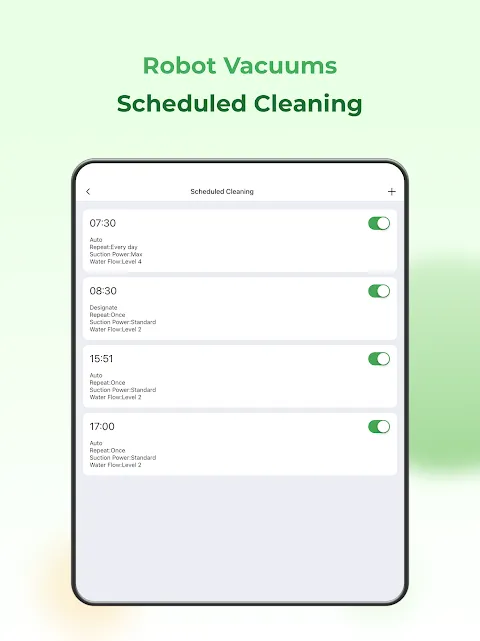 That Tuesday night broke me. I stumbled through the front door at 11:37 PM, my blistered heels screaming inside patent leather prisons. What greeted me wasn't sanctuary but war - a battlefield of cracker crumbs marching across hardwood, tumbleweeds of cat hair rolling like desert nomads, and that godforsaken green glitter from last month's craft project still winking mockingly from baseboards. My throat tightened with the sour tang of failure as I surveyed the carnage. This wasn't just dirt; it
That Tuesday night broke me. I stumbled through the front door at 11:37 PM, my blistered heels screaming inside patent leather prisons. What greeted me wasn't sanctuary but war - a battlefield of cracker crumbs marching across hardwood, tumbleweeds of cat hair rolling like desert nomads, and that godforsaken green glitter from last month's craft project still winking mockingly from baseboards. My throat tightened with the sour tang of failure as I surveyed the carnage. This wasn't just dirt; it -
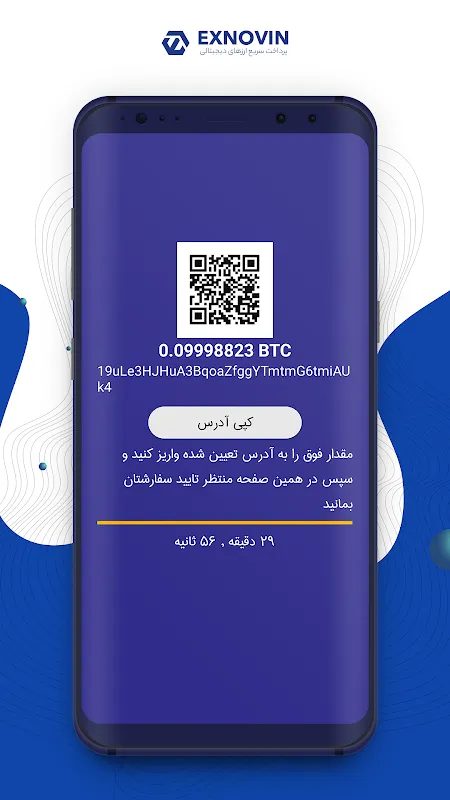 Rain lashed against the coffee shop window as my thumb hovered over the sell button. Bitcoin had just nosedived 12% in five minutes, and my portfolio was hemorrhaging value. But to cash out, I needed to log into my banking app, transfer funds to the exchange, wait for clearance, then execute the trade - a dance that'd take 20 minutes in a market moving at light speed. My palms left damp streaks on the phone case. That's when I remembered the weird purple icon I'd downloaded during a midnight cry
Rain lashed against the coffee shop window as my thumb hovered over the sell button. Bitcoin had just nosedived 12% in five minutes, and my portfolio was hemorrhaging value. But to cash out, I needed to log into my banking app, transfer funds to the exchange, wait for clearance, then execute the trade - a dance that'd take 20 minutes in a market moving at light speed. My palms left damp streaks on the phone case. That's when I remembered the weird purple icon I'd downloaded during a midnight cry -
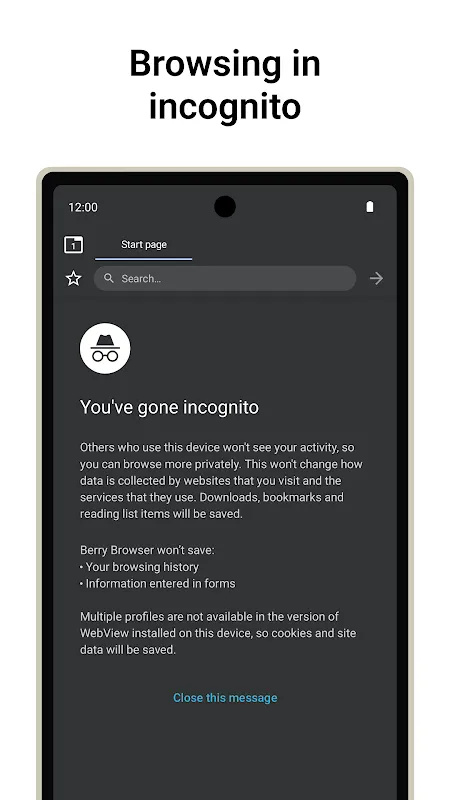 Rain lashed against the bus window as I stabbed at my phone screen, trying to close an ad that kept resurrecting itself like a digital zombie. My knuckles whitened around the strap handle – that damn toolbar was eating half my article about Kyoto's moss temples. For months, I’d tolerated browsers treating my fingers like clumsy invaders, not masters. Then came Tuesday’s espresso-fueled rage-click: I downloaded Berry Browser as a Hail Mary. Within minutes, I was elbow-deep in its guts, ripping ou
Rain lashed against the bus window as I stabbed at my phone screen, trying to close an ad that kept resurrecting itself like a digital zombie. My knuckles whitened around the strap handle – that damn toolbar was eating half my article about Kyoto's moss temples. For months, I’d tolerated browsers treating my fingers like clumsy invaders, not masters. Then came Tuesday’s espresso-fueled rage-click: I downloaded Berry Browser as a Hail Mary. Within minutes, I was elbow-deep in its guts, ripping ou -
 Dynadot \xe2\x80\x93 Domain Name ToolsManage and register your domains using only the most efficient and effective domain tools, directly from your mobile device. The Dynadot mobile app makes growing or adjusting your domain portfolio a breeze, helping you accomplish your domain investing goals or k
Dynadot \xe2\x80\x93 Domain Name ToolsManage and register your domains using only the most efficient and effective domain tools, directly from your mobile device. The Dynadot mobile app makes growing or adjusting your domain portfolio a breeze, helping you accomplish your domain investing goals or k -
 Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we
Cyber Rakshak AcademyWelcome to Secdroid, your ultimate cybersecurity learning platform. Our app is designed to equip users with essential knowledge and skills to stay safe and secure in the digital world. Whether you're a beginner or an experienced cybersecurity professional, Secdroid offers a wide range of courses, tutorials, and resources covering topics such as ethical hacking, network security, data protection, and more. With interactive lessons, hands-on labs, and real-world scenarios, we -
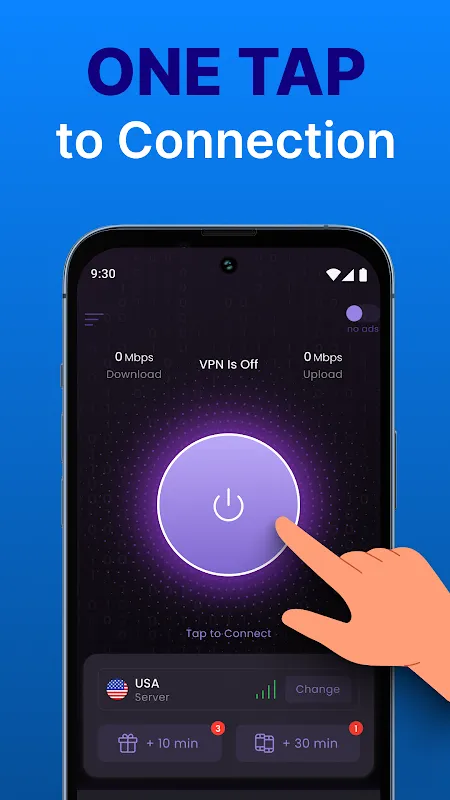 Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo
Rain lashed against the steamed windows of that cramped Barcelona café as I frantically stabbed my keyboard, heart pounding like a trapped bird. Deadline in 90 minutes, client files hostage behind geo-blocks, and public Wi-Fi screaming "hacker buffet" with every flickering connection. My throat tightened with that familiar acid-taste of professional ruin – until cold fingertips found the icon buried in my dock. One tap: encryption wrapped my data like armored silk. Suddenly, New York servers flo -
 NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/
NordLayerNordLayer provides flexible and easy-to-implement cybersecurity tools for businesses of any size or work model developed by the standard of NordVPN.We help organizations of all sizes to resolve sensitive data access and transmission challenges by providing a modern secure remote access solution focused on the Security Service Edge of cybersecurity services.Network access security made simpleEasy to Start- Deployment under ten minutes- Step-by-step guidelines, onboarding content, and 24/ -
 FrejaFreja eID is an electronic identification application that allows users to access online services, verify their identity, and manage their personal data securely. This app is designed for the Android platform and is available for download, offering a range of features that enhance user experience and security.The primary function of Freja eID is to enable users to identify themselves to various services and individuals. This includes proving one\xe2\x80\x99s age, verifying the identity of o
FrejaFreja eID is an electronic identification application that allows users to access online services, verify their identity, and manage their personal data securely. This app is designed for the Android platform and is available for download, offering a range of features that enhance user experience and security.The primary function of Freja eID is to enable users to identify themselves to various services and individuals. This includes proving one\xe2\x80\x99s age, verifying the identity of o -
 Epidemic Sound Music for VideoBring your story to life with the Epidemic Sound app.Discover, save, and download music for your content on the go. Get unlimited access to over 50,000 tracks and 200,000 sound effects to add more feeling and more meaning to everything you create. With personalized recommendations, curated collections, and soundtracking tools that fit seamlessly into your workflow, you can find the perfect soundtrack, fast. And with all rights included, you can soundtrack and publis
Epidemic Sound Music for VideoBring your story to life with the Epidemic Sound app.Discover, save, and download music for your content on the go. Get unlimited access to over 50,000 tracks and 200,000 sound effects to add more feeling and more meaning to everything you create. With personalized recommendations, curated collections, and soundtracking tools that fit seamlessly into your workflow, you can find the perfect soundtrack, fast. And with all rights included, you can soundtrack and publis -
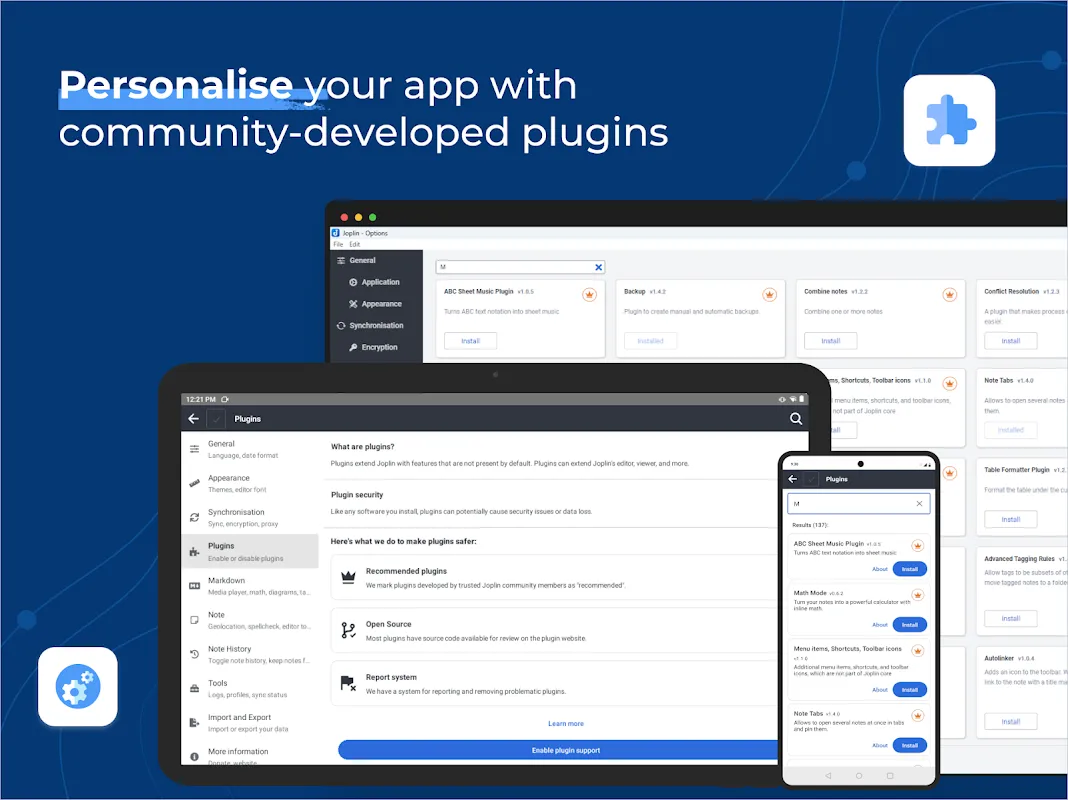 I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a
I remember the day my laptop crashed, taking with it months of research notes I'd foolishly stored only locally. The sinking feeling in my stomach was a visceral punch—all those midnight ideas, interview transcripts, and fragile hypotheses gone in a blink. For weeks, I'd been juggling between Google Keep for quick thoughts and Evernote for longer pieces, but the constant nagging fear of data breaches or losing everything to a hardware failure haunted me. Then, during a caffeine-fueled rant to a -
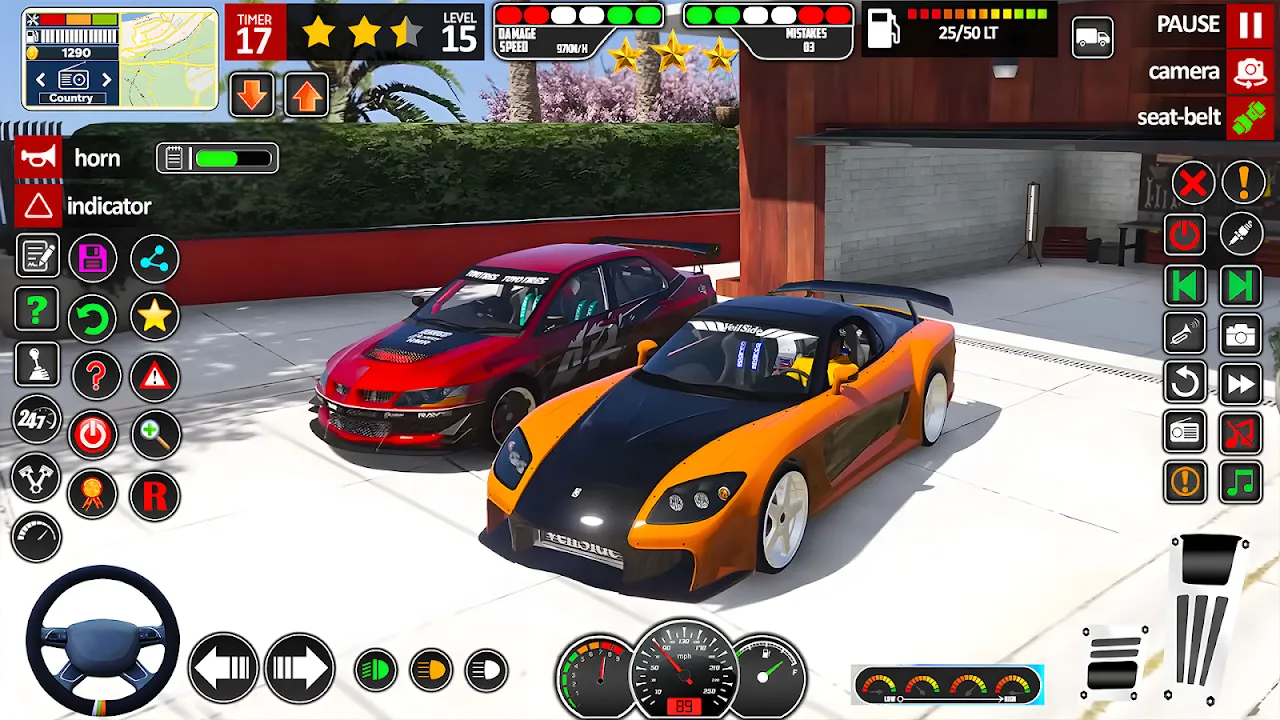 Rain lashed against my apartment windows like prison bars rattling as I jammed my thumb against the acceleration button. My stolen Lamborghini fishtailed across wet pixelated asphalt, sirens wailing behind me in Doppler-shifted terror. This wasn't escapism anymore - Gangster Crime City's physics engine had crossed into visceral territory. Engine oil and ozone flooded my senses despite the cheap headphones, every pothole jolting my spine as the NYPD cruiser's headlights devoured my rearview mirro
Rain lashed against my apartment windows like prison bars rattling as I jammed my thumb against the acceleration button. My stolen Lamborghini fishtailed across wet pixelated asphalt, sirens wailing behind me in Doppler-shifted terror. This wasn't escapism anymore - Gangster Crime City's physics engine had crossed into visceral territory. Engine oil and ozone flooded my senses despite the cheap headphones, every pothole jolting my spine as the NYPD cruiser's headlights devoured my rearview mirro
